ScreenConnect User Database Modification
Detects file modifications to the temporary xml user database file indicating local user modification in the ScreenConnect server. This will occur during exploitation of the ScreenConnect Authentication Bypass vulnerability (CVE-2024-1709) in versions <23.9.8, but may also be observed when making legitimate modifications to local users or permissions.
Sigma rule (View on GitHub)
1title: ScreenConnect User Database Modification
2id: 1a821580-588b-4323-9422-660f7e131020
3related:
4 - id: 4109cb6a-a4af-438a-9f0c-056abba41c6f
5 type: similar
6status: experimental
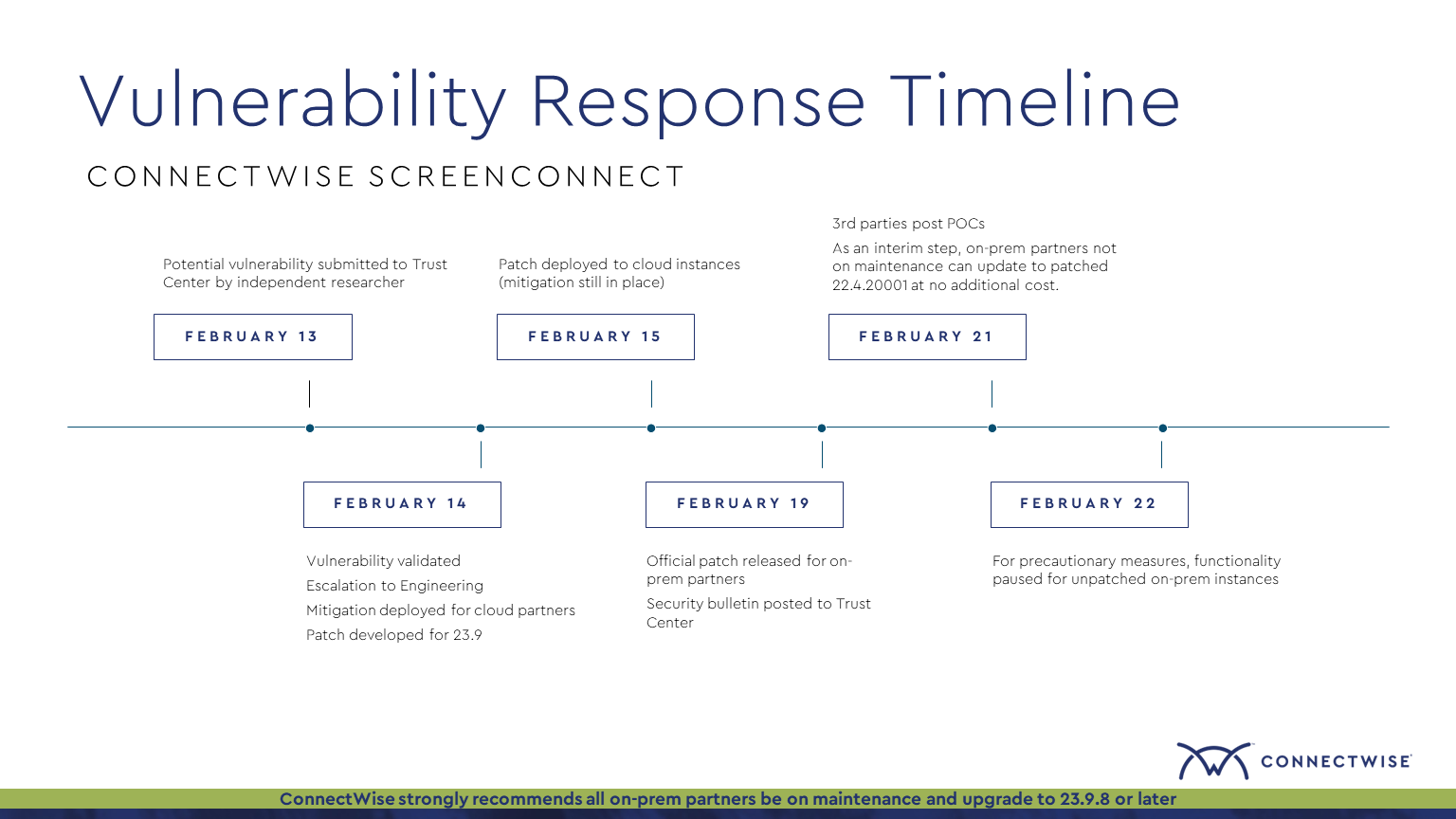
7description: |
8 Detects file modifications to the temporary xml user database file indicating local user modification in the ScreenConnect server.
9 This will occur during exploitation of the ScreenConnect Authentication Bypass vulnerability (CVE-2024-1709) in versions <23.9.8, but may also be observed when making legitimate modifications to local users or permissions.
10references:
11 - https://www.connectwise.com/company/trust/security-bulletins/connectwise-screenconnect-23.9.8
12 - https://www.cve.org/CVERecord?id=CVE-2024-1709
13 - https://www.huntress.com/blog/a-catastrophe-for-control-understanding-the-screenconnect-authentication-bypass
14author: Matt Anderson, Andrew Schwartz, Caleb Stewart, Huntress
15date: 2024/02/21
16tags:
17 - attack.persistence
18 - cve.2024.1709
19logsource:
20 product: windows
21 category: file_event
22detection:
23 selection:
24 TargetFilename|endswith: '.xml'
25 TargetFilename|contains|all:
26 - 'Temp'
27 - 'ScreenConnect'
28 Image|endswith: '\ScreenConnect.Service.exe'
29 condition: selection
30falsepositives:
31 - This will occur legitimately as well and will result in some benign activity.
32level: medium
References
Related rules
- CVE-2024-1709 - ScreenConnect Authentication Bypass Exploitation
- CVE-2024-1708 - ScreenConnect Path Traversal Exploitation
- CVE-2024-1708 - ScreenConnect Path Traversal Exploitation - Security
- ScreenConnect User Database Modification - Security
- BITS Transfer Job Download From File Sharing Domains