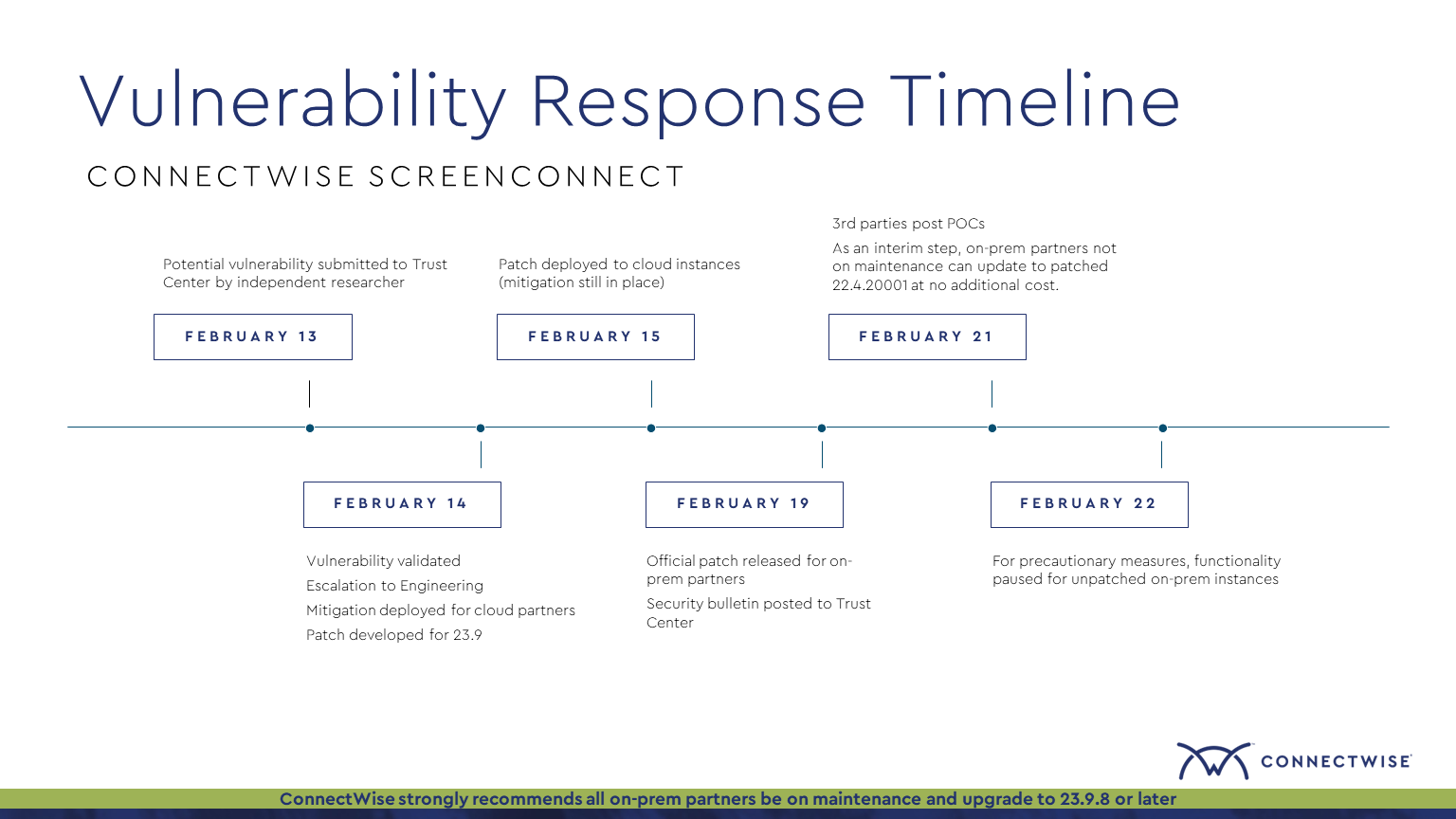
CVE-2024-1708 - ScreenConnect Path Traversal Exploitation - Security
This detects file modifications to ASPX and ASHX files within the root of the App_Extensions directory, which is allowed by a ZipSlip vulnerability in versions prior to 23.9.8. This occurs during exploitation of CVE-2024-1708. This requires an Advanced Auditing policy to log a successful Windows Event ID 4663 events and with a SACL set on the directory.
Sigma rule (View on GitHub)
1title: CVE-2024-1708 - ScreenConnect Path Traversal Exploitation - Security
2id: 4c198a60-7d05-4daf-8bf7-4136fb6f5c62
3related:
4 - id: 44d7af7e-88e6-4490-be11-55f7ff4d9fc1
5 type: similar
6status: experimental
7description: |
8 This detects file modifications to ASPX and ASHX files within the root of the App_Extensions directory, which is allowed by a ZipSlip vulnerability in versions prior to 23.9.8. This occurs during exploitation of CVE-2024-1708.
9 This requires an Advanced Auditing policy to log a successful Windows Event ID 4663 events and with a SACL set on the directory.
10references:
11 - https://www.connectwise.com/company/trust/security-bulletins/connectwise-screenconnect-23.9.8
12 - https://www.cve.org/CVERecord?id=CVE-2024-1708
13 - https://www.huntress.com/blog/a-catastrophe-for-control-understanding-the-screenconnect-authentication-bypass
14author: Matt Anderson, Caleb Stewart, Huntress
15date: 2024/02/20
16tags:
17 - attack.initial_access
18 - attack.persistence
19 - cve.2024.1708
20logsource:
21 product: windows
22 service: security
23 definition: 'Requirements: SACLs must be enabled for the ScreenConnect directory'
24detection:
25 selection:
26 EventID: 4663
27 ObjectType: 'File'
28 ProcessName|contains: 'ScreenConnect.Service.exe'
29 AccessMask: '0x6'
30 ObjectName|endswith:
31 - 'ScreenConnect\\App_Extensions\\*.ashx'
32 - 'ScreenConnect\\App_Extensions\\*.aspx'
33 filter_main_legit_extension:
34 ObjectName|contains: 'ScreenConnect\App_Extensions\\*\\'
35 condition: selection and not 1 of filter_main_*
36falsepositives:
37 - Unknown
38level: critical
References
Related rules
- CVE-2024-1708 - ScreenConnect Path Traversal Exploitation
- CVE-2024-1709 - ScreenConnect Authentication Bypass Exploitation
- Shell Process Spawned by Java.EXE
- Suspicious Processes Spawned by Java.EXE
- Suspicious Processes Spawned by WinRM