ScreenConnect User Database Modification - Security
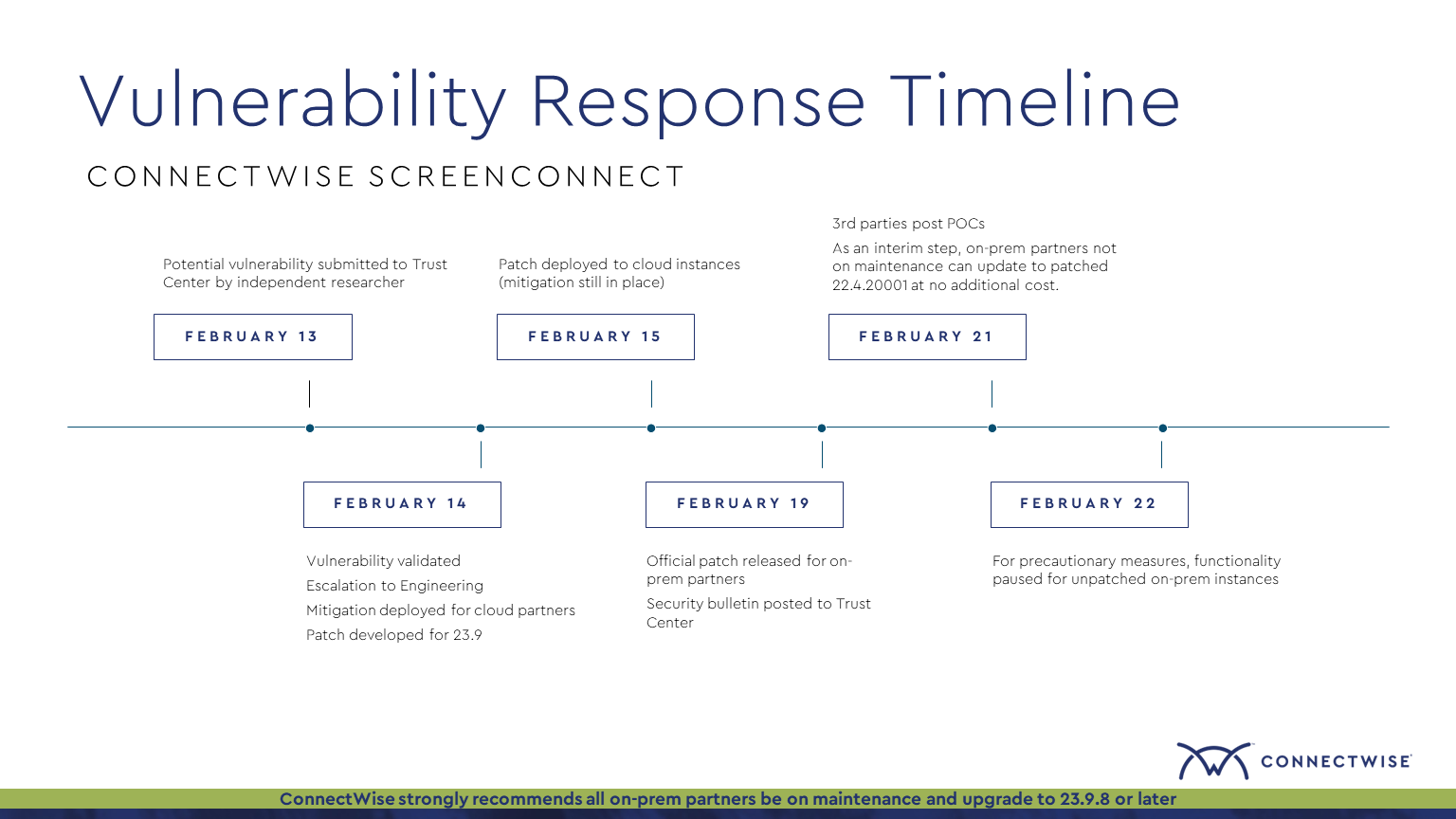
This detects file modifications to the temporary xml user database file indicating local user modification in the ScreenConnect server. This will occur during exploitation of the ScreenConnect Authentication Bypass vulnerability (CVE-2024-1709) in versions <23.9.8, but may also be observed when making legitimate modifications to local users or permissions. This requires an Advanced Auditing policy to log a successful Windows Event ID 4663 events and with a SACL set on the directory.
Sigma rule (View on GitHub)
1title: ScreenConnect User Database Modification - Security
2id: 4109cb6a-a4af-438a-9f0c-056abba41c6f
3related:
4 - id: 1a821580-588b-4323-9422-660f7e131020
5 type: similar
6status: experimental
7description: |
8 This detects file modifications to the temporary xml user database file indicating local user modification in the ScreenConnect server.
9 This will occur during exploitation of the ScreenConnect Authentication Bypass vulnerability (CVE-2024-1709) in versions <23.9.8, but may also be observed when making legitimate modifications to local users or permissions.
10 This requires an Advanced Auditing policy to log a successful Windows Event ID 4663 events and with a SACL set on the directory.
11references:
12 - https://www.connectwise.com/company/trust/security-bulletins/connectwise-screenconnect-23.9.8
13 - https://www.cve.org/CVERecord?id=CVE-2024-1709
14 - https://www.huntress.com/blog/a-catastrophe-for-control-understanding-the-screenconnect-authentication-bypass
15author: Matt Anderson, Kris Luzadre, Andrew Schwartz, Huntress
16date: 2024/02/20
17tags:
18 - attack.defense_evasion
19 - cve.2024.1709
20logsource:
21 product: windows
22 service: security
23 definition: 'Requirements: SACLs must be enabled for the ScreenConnect directory'
24detection:
25 selection:
26 EventID: 4663
27 ObjectType: 'File'
28 AccessMask: '0x6'
29 ObjectName|endswith: '.xml'
30 ObjectName|contains|all:
31 - 'Temp'
32 - 'ScreenConnect'
33 ProcessName|contains: 'ScreenConnect.Service.exe'
34 condition: selection
35falsepositives:
36 - This will occur legitimately as well and will result in some benign activity.
37level: medium
References
Related rules
- CVE-2024-1709 - ScreenConnect Authentication Bypass Exploitation
- ScreenConnect User Database Modification
- BITS Transfer Job Download From File Sharing Domains
- Bypass UAC Using SilentCleanup Task
- Network Connection Initiated By Regsvr32.EXE