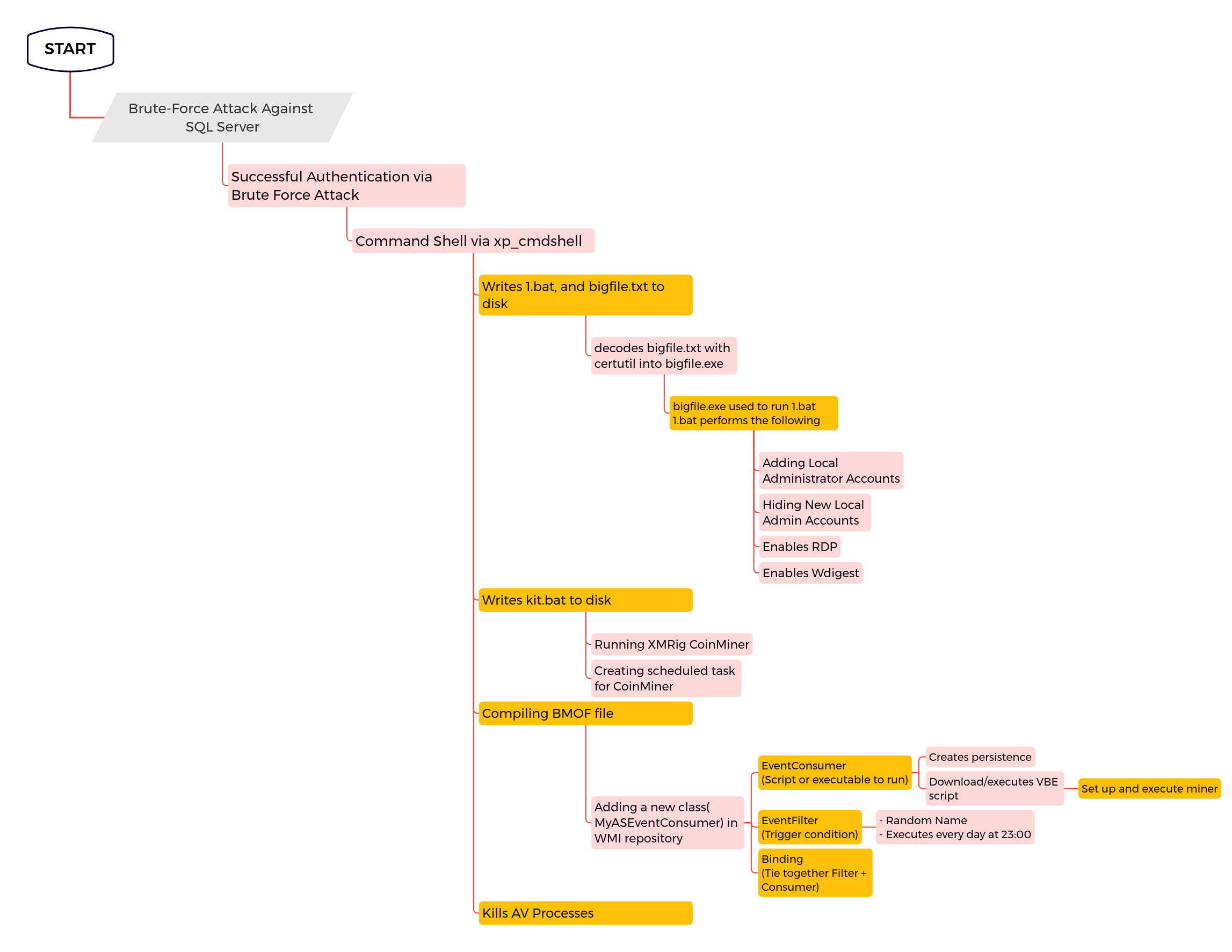
Potentially Suspicious CMD Shell Output Redirect
Detects inline Windows shell commands redirecting output via the ">" symbol to a suspicious location. This technique is sometimes used by malicious actors in order to redirect the output of reconnaissance commands such as "hostname" and "dir" to files for future exfiltration.
Sigma rule (View on GitHub)
1title: Potentially Suspicious CMD Shell Output Redirect
2id: 8e0bb260-d4b2-4fff-bb8d-3f82118e6892
3related:
4 - id: aa2efee7-34dd-446e-8a37-40790a66efd7
5 type: derived
6 - id: 4f4eaa9f-5ad4-410c-a4be-bc6132b0175a
7 type: similar
8status: experimental
9description: |
10 Detects inline Windows shell commands redirecting output via the ">" symbol to a suspicious location.
11 This technique is sometimes used by malicious actors in order to redirect the output of reconnaissance commands such as "hostname" and "dir" to files for future exfiltration.
12references:
13 - https://thedfirreport.com/2022/07/11/select-xmrig-from-sqlserver/
14author: Nasreddine Bencherchali (Nextron Systems)
15date: 2022/07/12
16modified: 2024/03/19
17tags:
18 - attack.defense_evasion
19 - attack.t1218
20logsource:
21 category: process_creation
22 product: windows
23detection:
24 selection_img:
25 - Image|endswith: '\cmd.exe'
26 - OriginalFileName: 'Cmd.Exe'
27 selection_cli_1:
28 CommandLine|contains:
29 # Note: Add more suspicious locations as you find them
30 # Note: The space from the start is missing to cover append operations ">>"
31 # Note: We use the "?" to account for both a single and a double quote
32 # Note: If you want to account for more spaces which is still a valid bypass option. Use a regex with "\s"
33 - '>?%APPDATA%\'
34 - '>?%TEMP%\'
35 - '>?%TMP%\'
36 - '>?%USERPROFILE%\'
37 - '>?C:\ProgramData\'
38 - '>?C:\Temp\'
39 - '>?C:\Users\Public\'
40 - '>?C:\Windows\Temp\'
41 selection_cli_2:
42 CommandLine|contains:
43 - ' >'
44 - '">'
45 - "'>"
46 CommandLine|contains|all:
47 - 'C:\Users\'
48 - '\AppData\Local\'
49 condition: selection_img and 1 of selection_cli_*
50falsepositives:
51 - Legitimate admin or third party scripts used for diagnostic collection might generate some false positives
52level: medium
References
Related rules
- Potentially Suspicious Wuauclt Network Connection
- Application Bypass with DllRegisterServer Function
- Rundll32 Injection into LSASS
- Rundll32 Without a Command Line
- Rundll32 with Suspicious Process Lineage