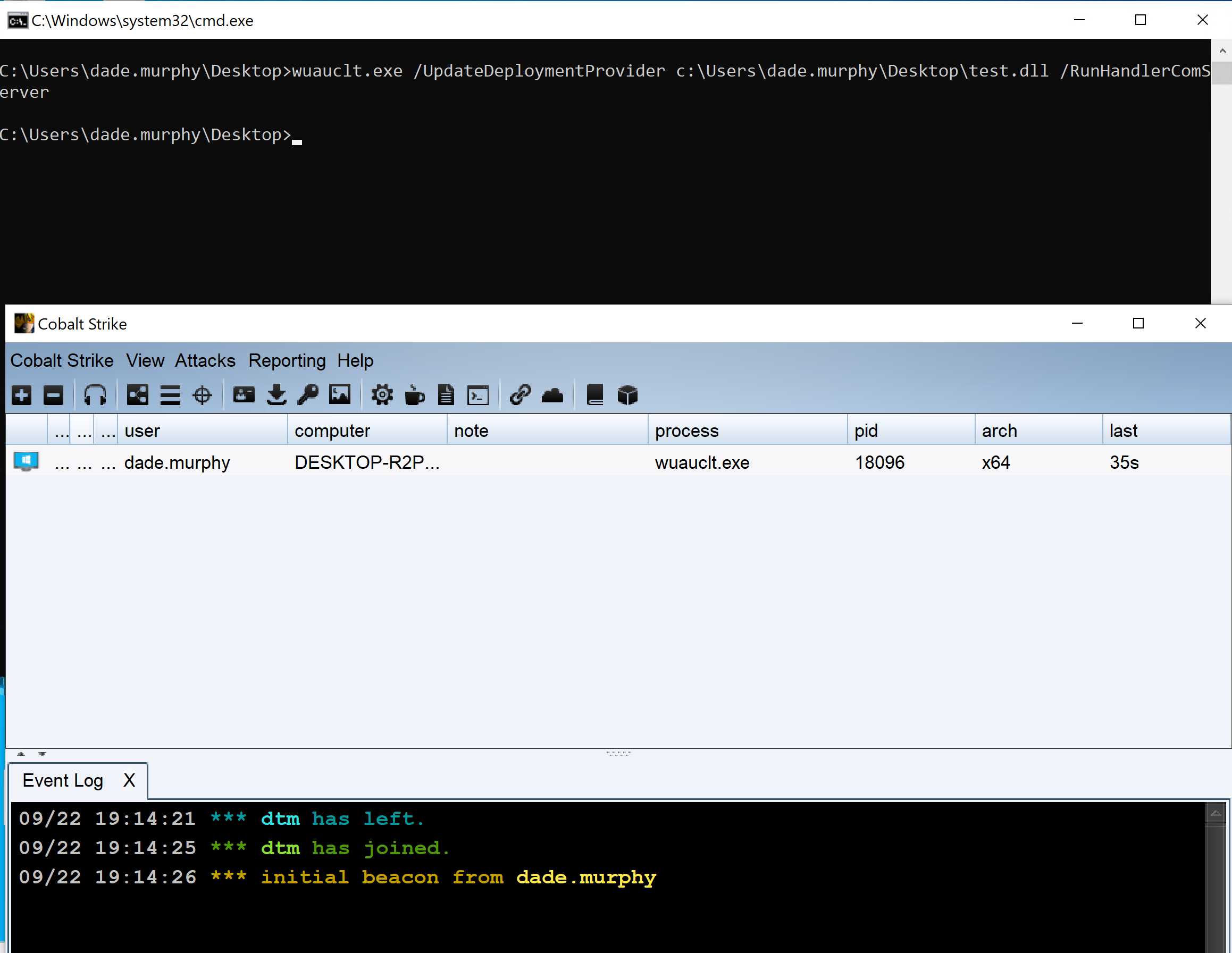
Potentially Suspicious Wuauclt Network Connection
Detects the use of the Windows Update Client binary (wuauclt.exe) to proxy execute code and making network connections. One could easily make the DLL spawn a new process and inject to it to proxy the network connection and bypass this rule.
Sigma rule (View on GitHub)
1title: Potentially Suspicious Wuauclt Network Connection
2id: c649a6c7-cd8c-4a78-9c04-000fc76df954
3status: test
4description: |
5 Detects the use of the Windows Update Client binary (wuauclt.exe) to proxy execute code and making network connections.
6 One could easily make the DLL spawn a new process and inject to it to proxy the network connection and bypass this rule.
7references:
8 - https://dtm.uk/wuauclt/
9author: Roberto Rodriguez (Cyb3rWard0g), OTR (Open Threat Research)
10date: 2020/10/12
11modified: 2024/03/12
12tags:
13 - attack.defense_evasion
14 - attack.t1218
15logsource:
16 category: network_connection
17 product: windows
18 definition: 'Requirements: The CommandLine field enrichment is required in order for this rule to be used.'
19detection:
20 selection:
21 Image|contains: 'wuauclt'
22 CommandLine|contains: ' /RunHandlerComServer'
23 # "C:\WINDOWS\uus\AMD64\wuauclt.exe" /DeploymentHandlerFullPath \\?\C:\Windows\UUS\AMD64\UpdateDeploy.dll /ClassId aaa256e1-5b21-4993-9188-18f07ccb3b98 /RunHandlerComServer
24 filter_main_ip:
25 DestinationIp|cidr: # Ranges excluded based on https://github.com/SigmaHQ/sigma/blob/0f176092326ab9d1e19384d30224e5f29f760d82/rules/windows/network_connection/net_connection_win_dllhost_net_connections.yml
26 - '127.0.0.0/8'
27 - '10.0.0.0/8'
28 - '169.254.0.0/16' # link-local address
29 - '172.16.0.0/12'
30 - '192.168.0.0/16'
31 - '::1/128' # IPv6 loopback
32 - 'fe80::/10' # IPv6 link-local addresses
33 - 'fc00::/7' # IPv6 private addresses
34 filter_main_msrange: # Sysmon
35 DestinationIp|cidr:
36 - '20.184.0.0/13' # Microsoft Corporation
37 - '20.192.0.0/10' # Microsoft Corporation
38 - '23.79.0.0/16' # Microsoft Corporation
39 - '51.10.0.0/15'
40 - '51.103.0.0/16' # Microsoft Corporation
41 - '51.104.0.0/15' # Microsoft Corporation
42 - '52.224.0.0/11' # Microsoft Corporation
43 filter_main_uus:
44 CommandLine|contains:
45 - ':\Windows\UUS\Packages\Preview\amd64\updatedeploy.dll /ClassId'
46 - ':\Windows\UUS\amd64\UpdateDeploy.dll /ClassId'
47 filter_main_winsxs:
48 CommandLine|contains|all:
49 - ':\Windows\WinSxS\'
50 - '\UpdateDeploy.dll /ClassId '
51 filter_main_cli_null:
52 CommandLine: null
53 filter_main_cli_empty:
54 CommandLine: ''
55 condition: selection and not 1 of filter_main_*
56falsepositives:
57 - Unknown
58level: medium
References
Related rules
- Application Bypass with DllRegisterServer Function
- Rundll32 Injection into LSASS
- Rundll32 Without a Command Line
- Rundll32 with Suspicious Process Lineage
- Suspicious Export Functionalities - Rundll32