Potential Shadow Credentials added to AD Object
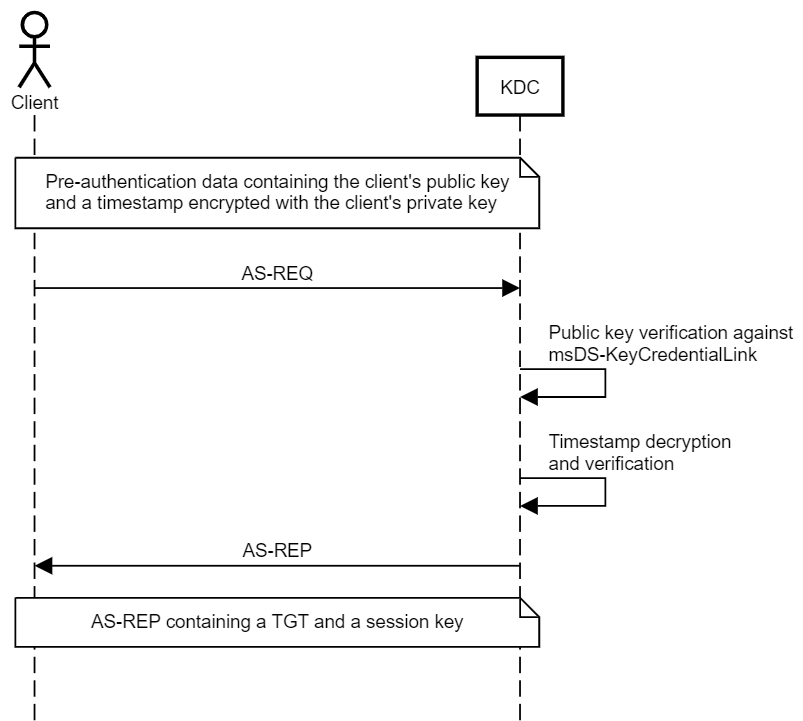
Identify the modification of the msDS-KeyCredentialLink attribute in an Active Directory Computer or User Object. Attackers can abuse control over the object and create a key pair, append to raw public key in the attribute, and obtain persistent and stealthy access to the target user or computer object.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2022/01/26"
3integration = ["system", "windows"]
4maturity = "production"
5updated_date = "2024/07/08"
6
7[rule]
8author = ["Elastic"]
9description = """
10Identify the modification of the msDS-KeyCredentialLink attribute in an Active Directory Computer or User Object.
11Attackers can abuse control over the object and create a key pair, append to raw public key in the attribute, and obtain
12persistent and stealthy access to the target user or computer object.
13"""
14false_positives = [
15 """
16 Modifications in the msDS-KeyCredentialLink attribute can be done legitimately by the Azure AD Connect
17 synchronization account or the ADFS service account. These accounts can be added as Exceptions.
18 """,
19]
20from = "now-9m"
21index = ["winlogbeat-*", "logs-system.*", "logs-windows.*"]
22language = "kuery"
23license = "Elastic License v2"
24name = "Potential Shadow Credentials added to AD Object"
25note = """## Triage and analysis
26
27### Investigating Potential Shadow Credentials added to AD Object
28
29The msDS-KeyCredentialLink is an Active Directory (AD) attribute that links cryptographic certificates to a user or computer for domain authentication.
30
31Attackers with write privileges on this attribute over an object can abuse it to gain access to the object or maintain persistence. This means they can authenticate and perform actions on behalf of the exploited identity, and they can use Shadow Credentials to request Ticket Granting Tickets (TGTs) on behalf of the identity.
32
33#### Possible investigation steps
34
35- Identify whether Windows Hello for Business (WHfB) and/or Azure AD is used in the environment.
36 - Review the event ID 4624 for logon events involving the subject identity (`winlog.event_data.SubjectUserName`).
37 - Check whether the `source.ip` is the server running Azure AD Connect.
38- Contact the account and system owners and confirm whether they are aware of this activity.
39- Investigate other alerts associated with the user/host during the past 48 hours.
40- Review the event IDs 4768 and 4769 for suspicious ticket requests involving the modified identity (`winlog.event_data.ObjectDN`).
41 - Extract the source IP addresses from these events and use them as indicators of compromise (IoCs) to investigate whether the host is compromised and to scope the attacker's access to the environment.
42
43### False positive analysis
44
45- Administrators might use custom accounts on Azure AD Connect. If this is the case, make sure the account is properly secured. You can also create an exception for the account if expected activity makes too much noise in your environment.
46
47### Response and remediation
48
49- Initiate the incident response process based on the outcome of the triage.
50- Investigate credential exposure on systems compromised or used by the attacker to ensure all compromised accounts are identified. Reset passwords for these accounts and other potentially compromised credentials, such as email, business systems, and web services.
51 - Remove the Shadow Credentials from the object.
52- Investigate how the attacker escalated privileges and identify systems they used to conduct lateral movement. Use this information to determine ways the attacker could regain access to the environment.
53- Determine the initial vector abused by the attacker and take action to prevent reinfection through the same vector.
54- Using the incident response data, update logging and audit policies to improve the mean time to detect (MTTD) and the mean time to respond (MTTR).
55"""
56references = [
57 "https://posts.specterops.io/shadow-credentials-abusing-key-trust-account-mapping-for-takeover-8ee1a53566ab",
58 "https://www.thehacker.recipes/ad/movement/kerberos/shadow-credentials",
59 "https://github.com/OTRF/Set-AuditRule",
60 "https://cyberstoph.org/posts/2022/03/detecting-shadow-credentials/",
61]
62risk_score = 73
63rule_id = "79f97b31-480e-4e63-a7f4-ede42bf2c6de"
64setup = """## Setup
65
66The 'Audit Directory Service Changes' logging policy must be configured for (Success, Failure).
67Steps to implement the logging policy with Advanced Audit Configuration:
Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policies Configuration > Audit Policies > DS Access > Audit Directory Service Changes (Success,Failure)
1
2The above policy does not cover User objects, so we need to set up an AuditRule using https://github.com/OTRF/Set-AuditRule.
3As this specifies the msDS-KeyCredentialLink Attribute GUID, it is expected to be low noise.
Set-AuditRule -AdObjectPath 'AD:\CN=Users,DC=Domain,DC=com' -WellKnownSidType WorldSid -Rights WriteProperty -InheritanceFlags Children -AttributeGUID 5b47d60f-6090-40b2-9f37-2a4de88f3063 -AuditFlags Success
1"""
2severity = "high"
3tags = [
4 "Domain: Endpoint",
5 "OS: Windows",
6 "Use Case: Threat Detection",
7 "Tactic: Credential Access",
8 "Data Source: Active Directory",
9 "Resources: Investigation Guide",
10 "Use Case: Active Directory Monitoring",
11]
12timestamp_override = "event.ingested"
13type = "query"
14
15query = '''
16event.action:("Directory Service Changes" or "directory-service-object-modified") and event.code:"5136" and
17 winlog.event_data.AttributeLDAPDisplayName:"msDS-KeyCredentialLink" and winlog.event_data.AttributeValue :B\:828* and
18 not winlog.event_data.SubjectUserName: MSOL_*
19'''
20
21
22[[rule.threat]]
23framework = "MITRE ATT&CK"
24[[rule.threat.technique]]
25id = "T1556"
26name = "Modify Authentication Process"
27reference = "https://attack.mitre.org/techniques/T1556/"
28
29
30[rule.threat.tactic]
31id = "TA0006"
32name = "Credential Access"
33reference = "https://attack.mitre.org/tactics/TA0006/"
Triage and analysis
Investigating Potential Shadow Credentials added to AD Object
The msDS-KeyCredentialLink is an Active Directory (AD) attribute that links cryptographic certificates to a user or computer for domain authentication.
Attackers with write privileges on this attribute over an object can abuse it to gain access to the object or maintain persistence. This means they can authenticate and perform actions on behalf of the exploited identity, and they can use Shadow Credentials to request Ticket Granting Tickets (TGTs) on behalf of the identity.
Possible investigation steps
- Identify whether Windows Hello for Business (WHfB) and/or Azure AD is used in the environment.
- Review the event ID 4624 for logon events involving the subject identity (
winlog.event_data.SubjectUserName).- Check whether the
source.ipis the server running Azure AD Connect.
- Check whether the
- Review the event ID 4624 for logon events involving the subject identity (
- Contact the account and system owners and confirm whether they are aware of this activity.
- Investigate other alerts associated with the user/host during the past 48 hours.
- Review the event IDs 4768 and 4769 for suspicious ticket requests involving the modified identity (
winlog.event_data.ObjectDN).- Extract the source IP addresses from these events and use them as indicators of compromise (IoCs) to investigate whether the host is compromised and to scope the attacker's access to the environment.
False positive analysis
- Administrators might use custom accounts on Azure AD Connect. If this is the case, make sure the account is properly secured. You can also create an exception for the account if expected activity makes too much noise in your environment.
Response and remediation
- Initiate the incident response process based on the outcome of the triage.
- Investigate credential exposure on systems compromised or used by the attacker to ensure all compromised accounts are identified. Reset passwords for these accounts and other potentially compromised credentials, such as email, business systems, and web services.
- Remove the Shadow Credentials from the object.
- Investigate how the attacker escalated privileges and identify systems they used to conduct lateral movement. Use this information to determine ways the attacker could regain access to the environment.
- Determine the initial vector abused by the attacker and take action to prevent reinfection through the same vector.
- Using the incident response data, update logging and audit policies to improve the mean time to detect (MTTD) and the mean time to respond (MTTR).
References
Related rules
- User account exposed to Kerberoasting
- FirstTime Seen Account Performing DCSync
- Kerberos Pre-authentication Disabled for User
- Potential Credential Access via DCSync
- Sensitive Privilege SeEnableDelegationPrivilege assigned to a User