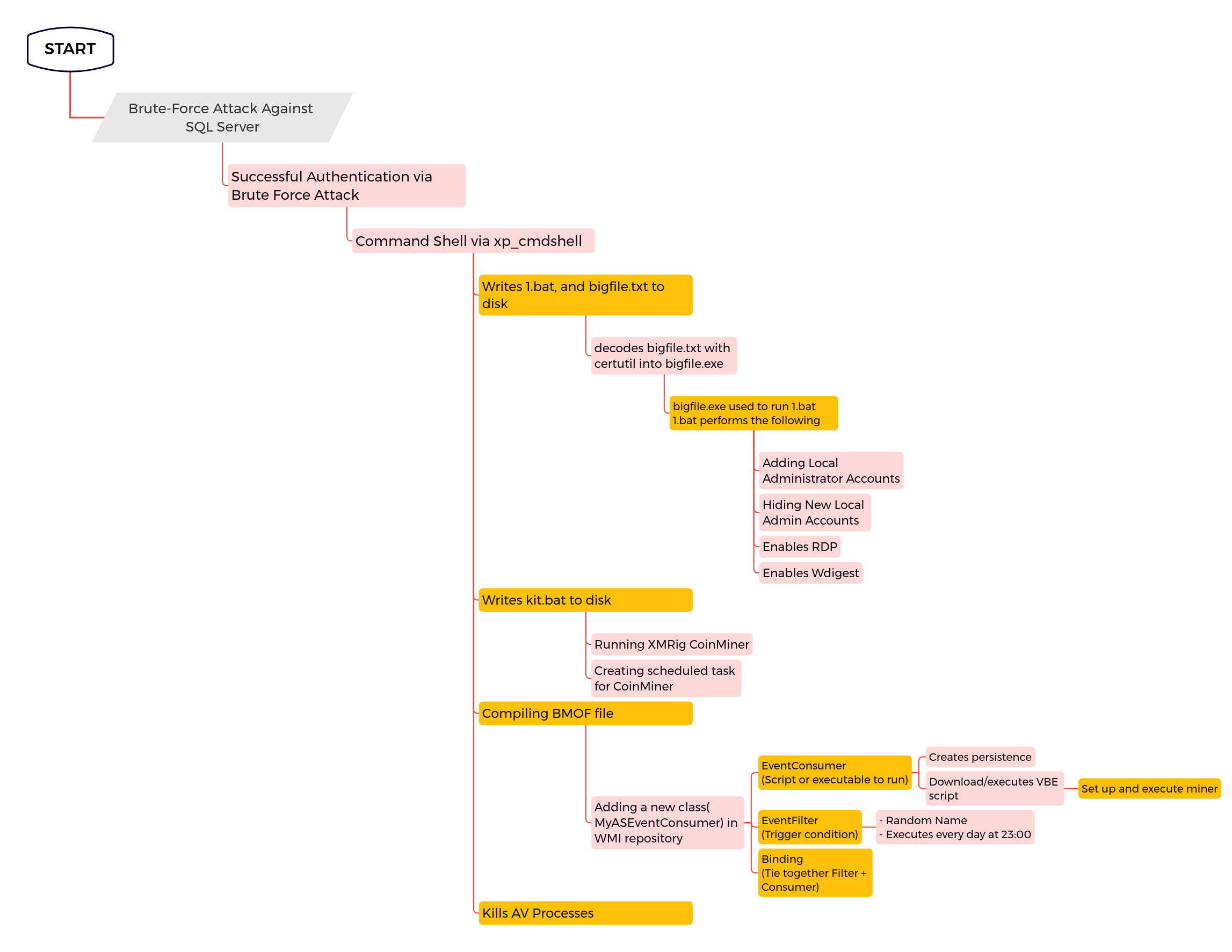
Suspicious Commands by SQL Server
Detects suspicious commands created from sqlservr process.
Sigma rule (View on GitHub)
1title: Suspicious Commands by SQL Server
2id: 9a73f4cc-a727-4b26-a9d8-81d2724b7f5e
3description: Detects suspicious commands created from sqlservr process.
4status: experimental
5author: 'TheDFIRReport'
6references:
7 - https://thedfirreport.com/2022/07/11/select-xmrig-from-sqlserver
8date: 2022/07/11
9modified: 2022/12/16
10tags:
11 - attack.initial_access
12 - attack.persistence
13 - attack.privilege_escalation
14logsource:
15 category: process_creation
16 product: windows
17detection:
18 selection:
19 ParentImage|endswith: '\sqlservr.exe'
20 Image|endswith:
21 - '\cmd.exe'
22 CommandLine|contains:
23 - 'del'
24 - 'cacls'
25 - 'attrib +s +h'
26 - 'takeown'
27 - 'taskkill'
28 - 'net'
29 - 'reg add'
30 - 'echo'
31 - 'cscript'
32 - 'whoami'
33 - 'netsh'
34 condition: selection
35level: high
References
Related rules
- UAC Bypass With Fake DLL
- Scheduled Cron Task/Job - Linux
- Scheduled Cron Task/Job - MacOs
- WMI Persistence - Script Event Consumer
- Path To Screensaver Binary Modified