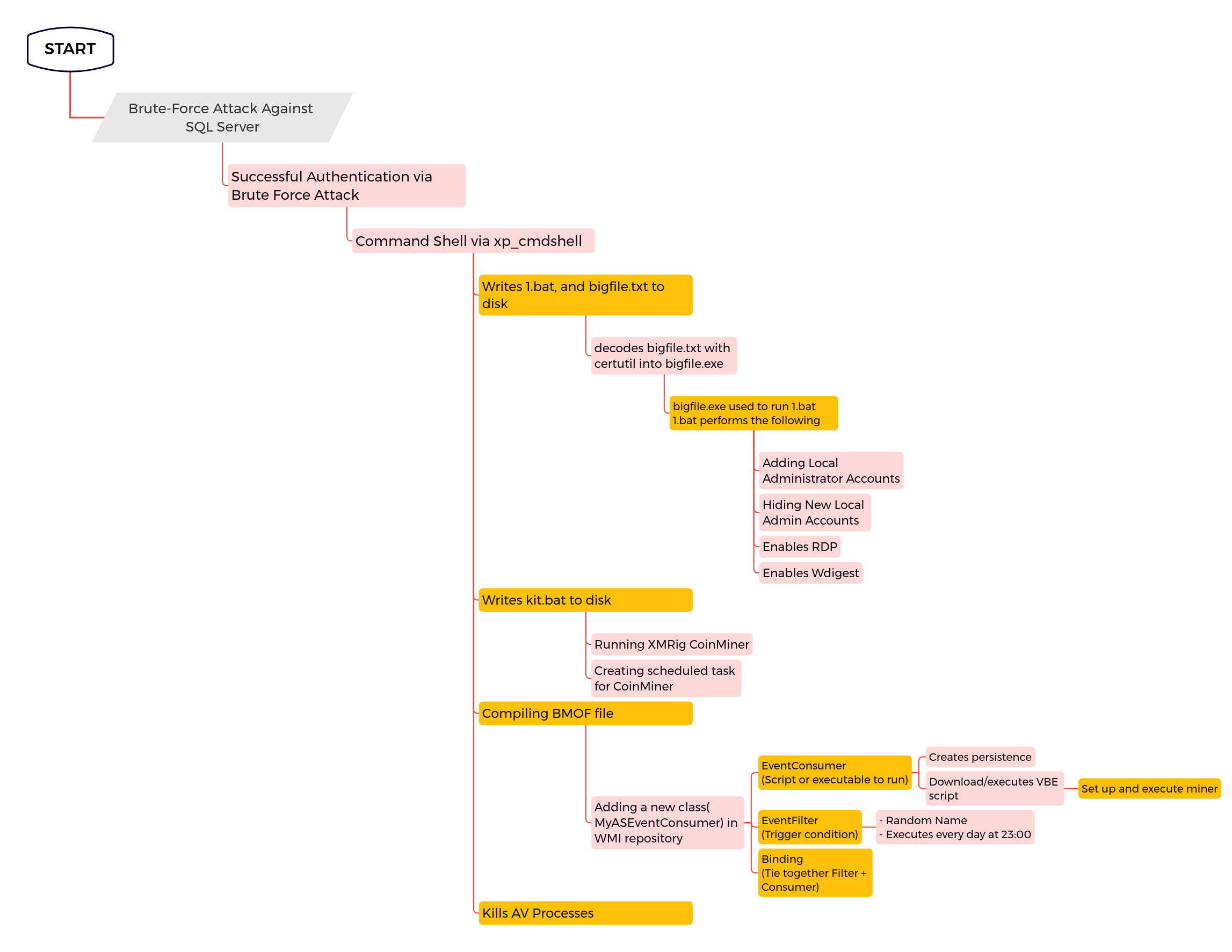
MOFComp Execution
Detects abuse of mofcomp to load WMI classes i.e. to create WMI event subscriptions
Sigma rule (View on GitHub)
1title: MOFComp Execution
2id: fd7aed23-7585-44fb-9920-5da82c740e6e
3status: experimental
4description: Detects abuse of mofcomp to load WMI classes i.e. to create WMI event subscriptions
5author: _pete_0, TheDFIRReport
6references:
7 - https://thedfirreport.com/2022/07/11/select-xmrig-from-sqlserver/
8date: 2022/07/11
9modified: 2022/07/11
10logsource:
11 category: process_creation
12 product: windows
13detection:
14 selection:
15 Image|endswith:
16 - '\mofcomp.exe'
17 ParentImage|endswith:
18 - '\cmd.exe'
19 - '\powershell.exe'
20 condition: selection
21fields:
22 - ParentCommandLine
23falsepositives:
24 - System administrator activities
25level: high
26tags:
27 - attack.execution
28 - attack.t1546.003
References
Related rules
- Operator Bloopers Cobalt Strike Commands
- Operator Bloopers Cobalt Strike Modules
- NTFS Alternate Data Stream
- Potential PowerShell Downgrade Attack
- PowerShell Create Local User