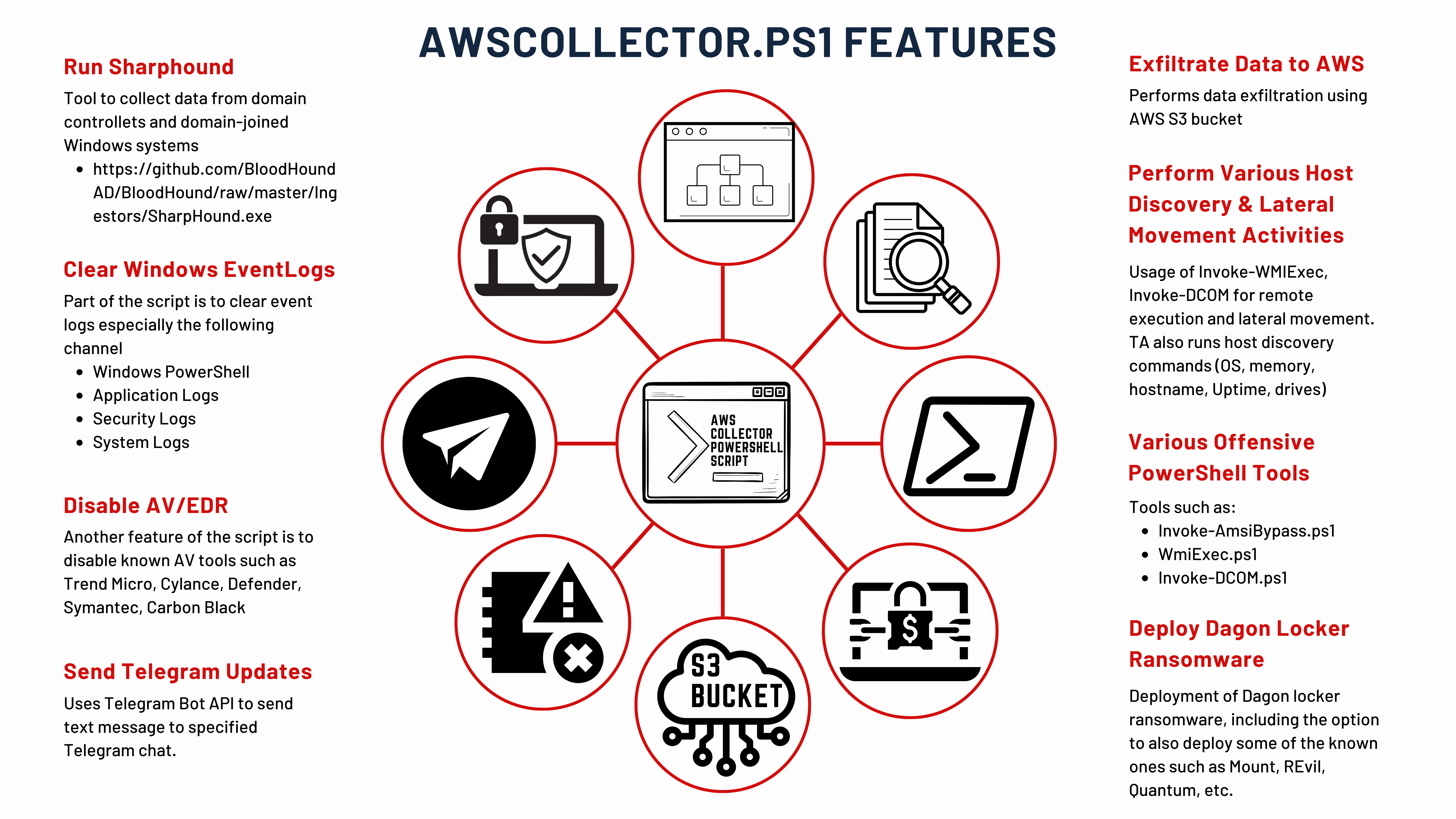
Data Exfiltration via AWS CLI
Detects usage of AWS CLI to exfiltrate data
Sigma rule (View on GitHub)
1title: Data Exfiltration via AWS CLI
2id: e7732014-c4b9-4653-92b2-aa7cfe154bf7
3status: experimental
4description: Detects usage of AWS CLI to exfiltrate data
5references:
6 - https://thedfirreport.com/2024/04/29/from-icedid-to-dagon-locker-ransomware-in-29-days/
7 - https://awscli.amazonaws.com/v2/documentation/api/latest/reference/s3/cp.html
8author: TheDFIRReport
9date: 2024/03/22
10modified: 2024/04/23
11tags:
12 - attack.exfiltration
13 - attack.t1567.002
14 - dist.public
15logsource:
16 category: process_creation
17 product: windows
18detection:
19 selection_cmdline_1:
20 CommandLine|contains: 's3 cp'
21 selection_cmdline_2:
22 CommandLine|contains: '--recursive'
23 selection_cmdline_3:
24 CommandLine|contains: '--region'
25 selection_cmdline_4:
26 CommandLine|contains: '--endpoint-url'
27 condition: all of selection_*
28falsepositives:
29 - Some administrators or automation could use AWS CLI to transfer data to S3.
30level: medium
References
Related rules
- APT40 Dropbox Tool User Agent
- DNS Query for Ufile.io Upload Domain
- Rclone SMB Share Exfiltration
- PUA - Rclone Execution
- DNS Query for Anonfiles.com Domain - DNS Client