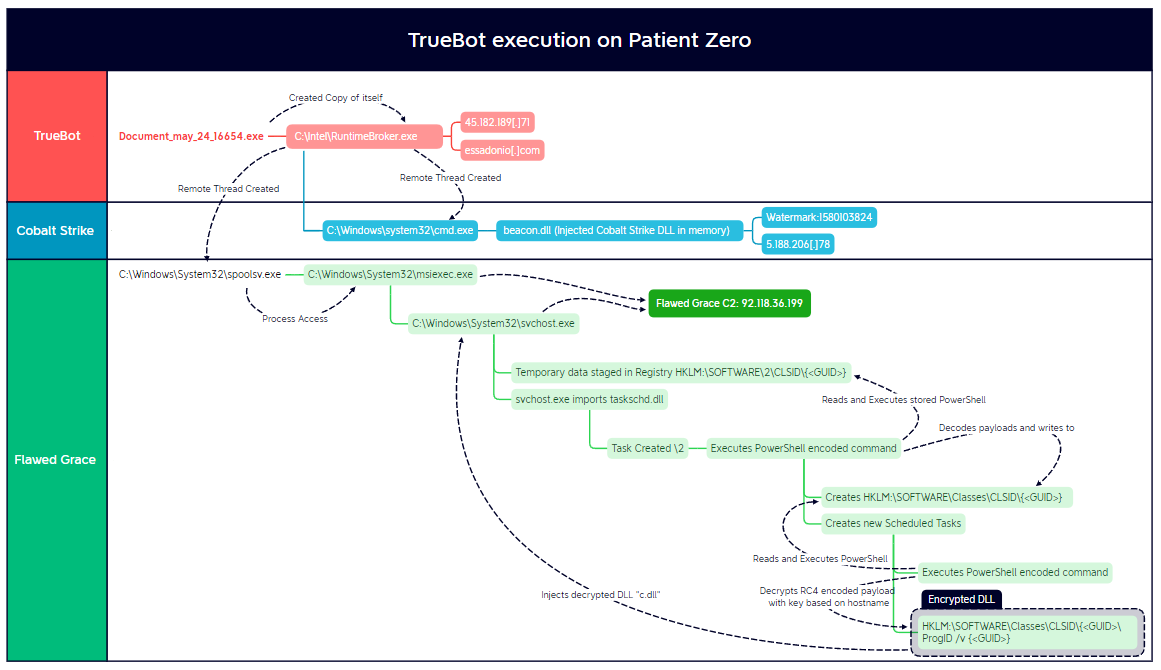
FlawedGrace spawning threat injection target
Detecting the command FlawedGrace is using for the purpose of injecting into it the spawned process, in this case the cmd.exe process.
Sigma rule (View on GitHub)
1title: FlawedGrace spawning threat injection target
2id: 295e71e5-38c9-4a59-90dd-9fa7bf617b4b
3description: Detecting the command FlawedGrace is using for the purpose of injecting into it the spawned process, in this case the cmd.exe process.
4status: experimental
5date: 2023-06-12
6modified: 2024-02-23
7author: "@kostastsale, @TheDFIRReport"
8references:
9 - https://thedfirreport.com/2023/06/12/a-truly-graceful-wipe-out
10logsource:
11 category: process_creation
12 product: windows
13detection:
14 selection1:
15 Image|endswith:
16 - '\cmd.exe'
17 CommandLine|contains|all:
18 - ' /I '
19 - ' /SI '
20 selection2:
21 Image|endswith:
22 - '\cmd.exe'
23 CommandLine|contains|all:
24 - ' /O '
25 - ' /SO '
26 condition: selection1 or selection2
27falsepositives:
28 - Unknown
29level: high
30tags:
31 - attack.defense_evasion #TA0005
32 - attack.t1055
33 - dist.public
References
Related rules
- Network Connection Initiated Via Notepad.EXE
- CobaltStrike Named Pipe Patterns
- PowerShell ShellCode
- Malicious Named Pipe Created
- Process Creation Using Sysnative Folder