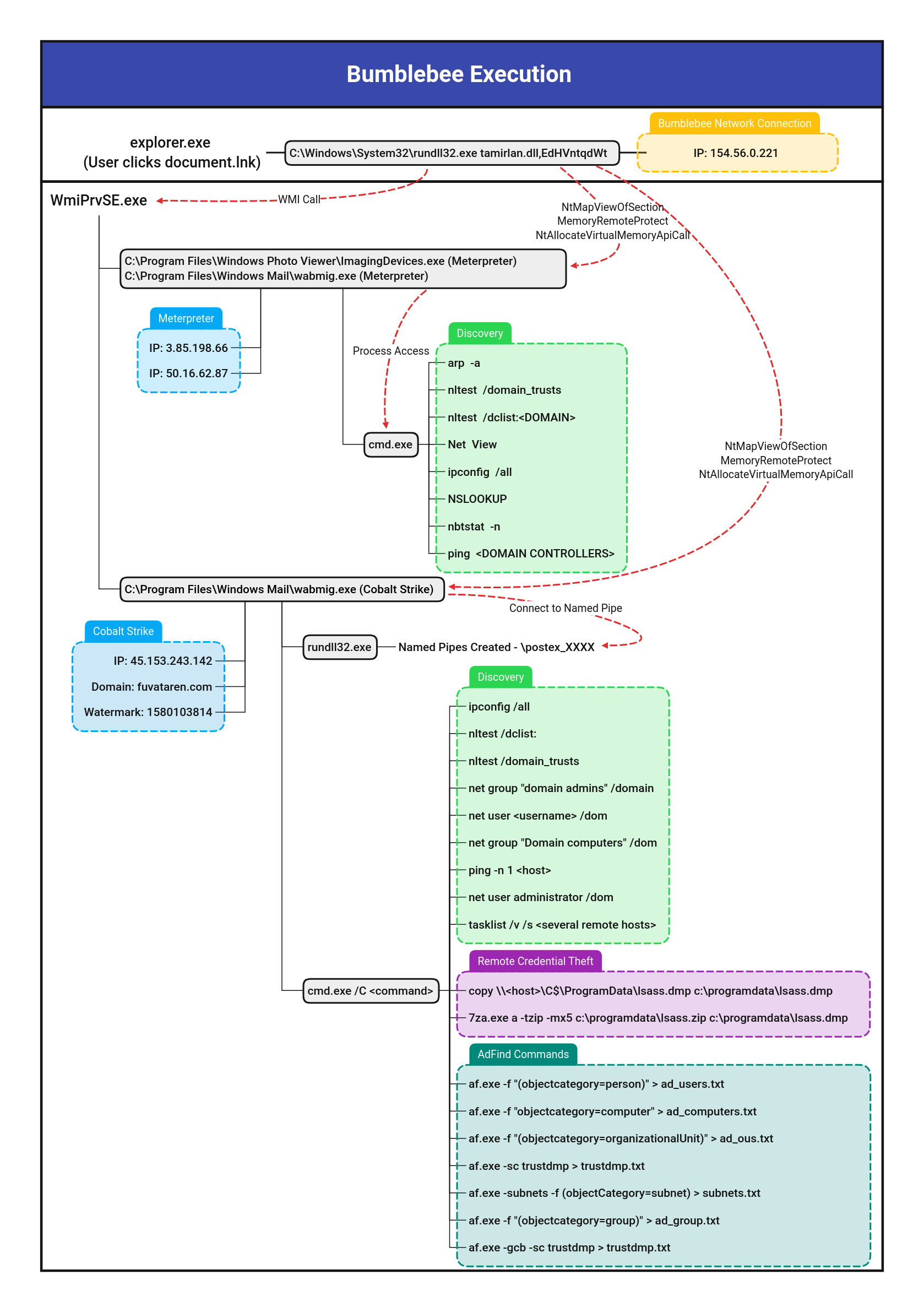
Weak or Abused Passwords In CLI
Detects weak passwords or often abused passwords (seen used by threat actors) via the CLI. An example would be a threat actor creating a new user via the net command and providing the password inline
Sigma rule (View on GitHub)
1title: Weak or Abused Passwords In CLI
2id: 91edcfb1-2529-4ac2-9ecc-7617f895c7e4
3status: test
4description: |
5 Detects weak passwords or often abused passwords (seen used by threat actors) via the CLI.
6 An example would be a threat actor creating a new user via the net command and providing the password inline
7references:
8 - https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/espionage-asia-governments
9 - https://thedfirreport.com/2022/09/26/bumblebee-round-two/
10 - https://www.microsoft.com/en-us/security/blog/2022/10/25/dev-0832-vice-society-opportunistic-ransomware-campaigns-impacting-us-education-sector/
11 - https://www.huntress.com/blog/slashandgrab-screen-connect-post-exploitation-in-the-wild-cve-2024-1709-cve-2024-1708
12author: Nasreddine Bencherchali (Nextron Systems)
13date: 2022/09/14
14modified: 2024/02/23
15tags:
16 - attack.defense_evasion
17 - attack.execution
18logsource:
19 category: process_creation
20 product: windows
21detection:
22 selection:
23 CommandLine|contains:
24 # Add more passwords
25 - '123456789'
26 - '123123qwE'
27 - 'Asd123.aaaa'
28 - 'Decryptme'
29 - 'P@ssw0rd!'
30 - 'Pass8080'
31 - 'password123' # Also covers PASSWORD123123! as seen in https://www.microsoft.com/en-us/security/blog/2022/10/25/dev-0832-vice-society-opportunistic-ransomware-campaigns-impacting-us-education-sector/
32 - 'test@202' # Covers multiple years
33 condition: selection
34falsepositives:
35 - Legitimate usage of the passwords by users via commandline (should be discouraged)
36 - Other currently unknown false positives
37level: medium
References
Related rules
- Custom Cobalt Strike Command Execution
- Network Connection Initiated By Regsvr32.EXE
- Network Connection Initiated Via Notepad.EXE
- Potential Compromised 3CXDesktopApp Execution
- Potential Compromised 3CXDesktopApp Update Activity