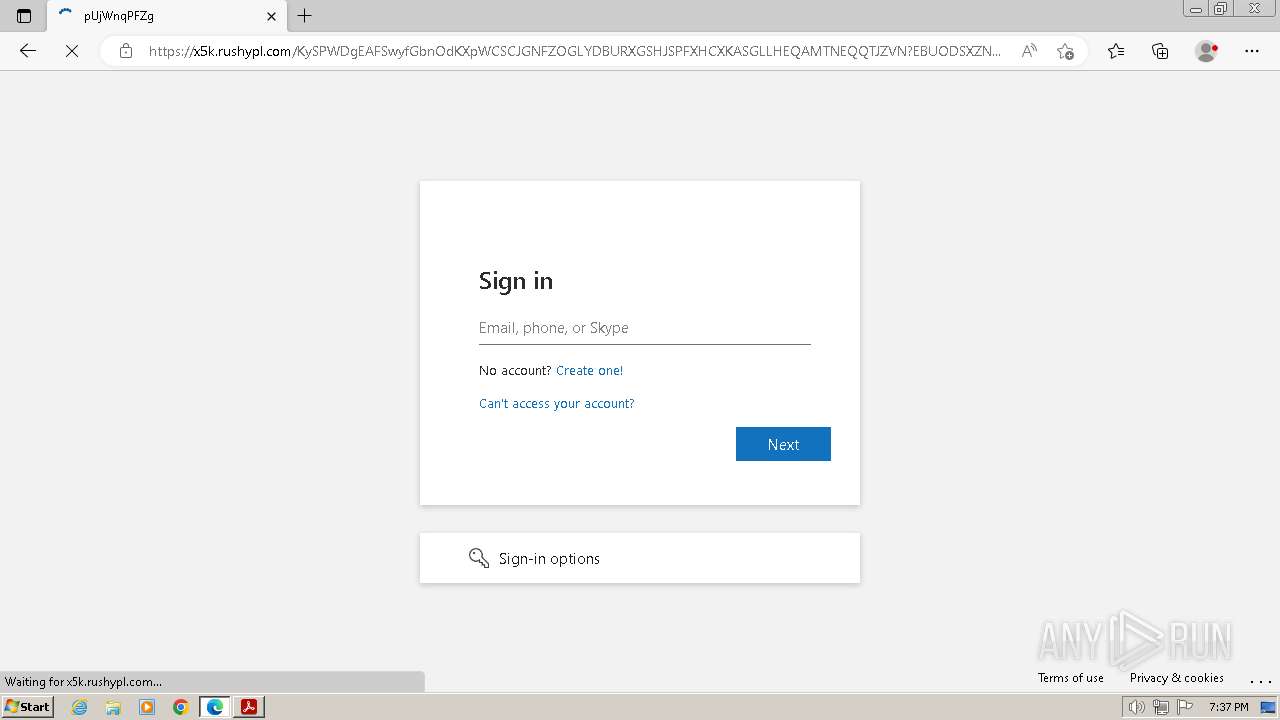
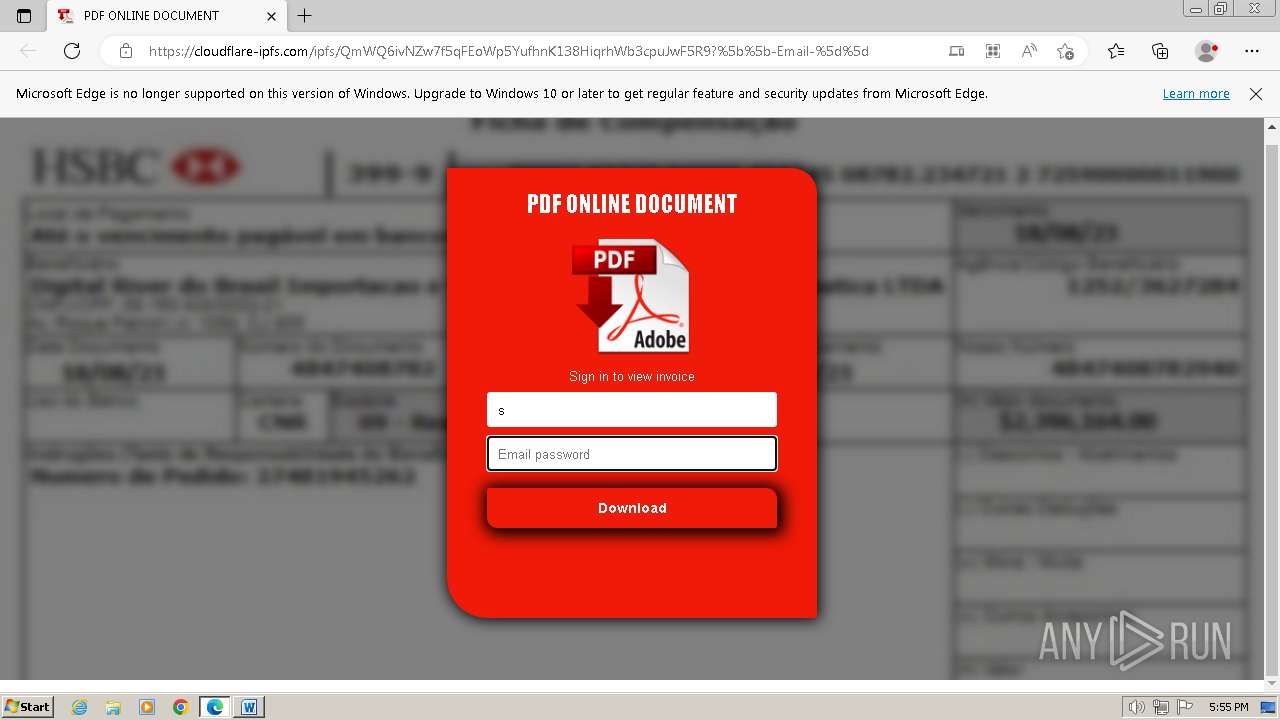
Potential Suspicious Browser Launch From Document Reader Process
Detects when a browser process or browser tab is launched from an application that handles document files such as Adobe, Microsoft Office, etc. And connects to a web application over http(s), this could indicate a possible phishing attempt.
Sigma rule (View on GitHub)
1title: Potential Suspicious Browser Launch From Document Reader Process
2id: 1193d960-2369-499f-a158-7b50a31df682
3status: experimental
4description: |
5 Detects when a browser process or browser tab is launched from an application that handles document files such as Adobe, Microsoft Office, etc. And connects to a web application over http(s), this could indicate a possible phishing attempt.
6references:
7 - https://app.any.run/tasks/69c5abaa-92ad-45ba-8c53-c11e23e05d04/ # PDF Document
8 - https://app.any.run/tasks/64043a79-165f-4052-bcba-e6e49f847ec1/ # Office Document
9author: Joseph Kamau
10date: 2024/05/27
11tags:
12 - attack.execution
13 - attack.t1204.002
14logsource:
15 product: windows
16 category: process_creation
17detection:
18 selection:
19 ParentImage|contains:
20 - 'Acrobat Reader'
21 - 'Microsoft Office'
22 - 'PDF Reader'
23 Image|endswith:
24 - '\brave.exe'
25 - '\chrome.exe'
26 - '\firefox.exe'
27 - '\msedge.exe'
28 - '\opera.exe'
29 - '\maxthon.exe'
30 - '\seamonkey.exe'
31 - '\vivaldi.exe'
32 - ''
33 CommandLine|contains: 'http'
34 condition: selection
35falsepositives:
36 - Unlikely in most cases, further investigation should be done in the commandline of the browser process to determine the context of the URL accessed.
37level: medium
References
Related rules
- File With Uncommon Extension Created By An Office Application
- Droppers Exploiting CVE-2017-11882
- Microsoft Excel Add-In Loaded From Uncommon Location
- Microsoft VBA For Outlook Addin Loaded Via Outlook
- Ursnif Malware C2 URL Pattern