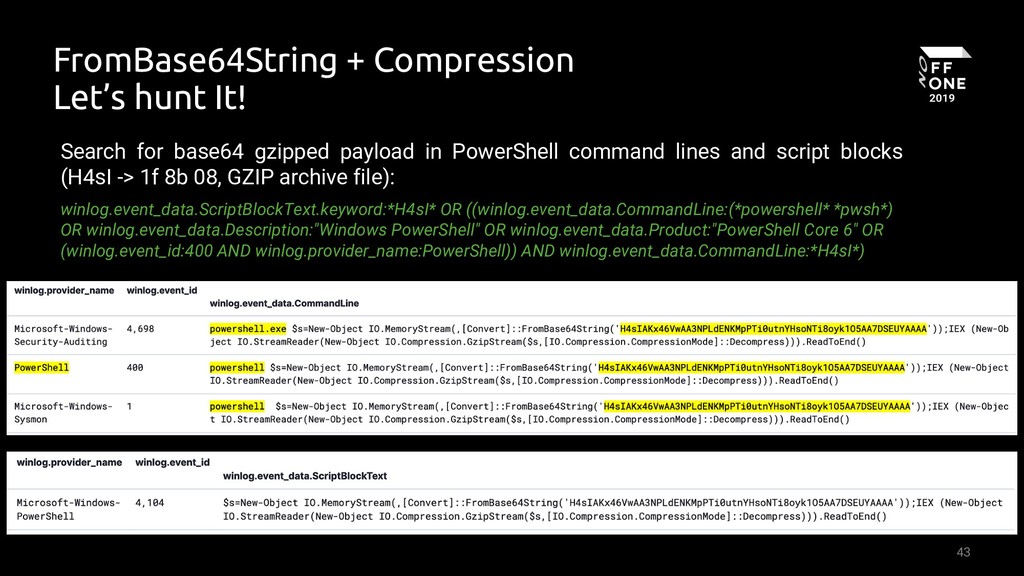
Suspicious FromBase64String Usage On Gzip Archive - Process Creation
Detects attempts of decoding a base64 Gzip archive via PowerShell. This technique is often used as a method to load malicious content into memory afterward.
Sigma rule (View on GitHub)
1title: Suspicious FromBase64String Usage On Gzip Archive - Process Creation
2id: d75d6b6b-adb9-48f7-824b-ac2e786efe1f
3related:
4 - id: df69cb1d-b891-4cd9-90c7-d617d90100ce
5 type: similar
6status: test
7description: Detects attempts of decoding a base64 Gzip archive via PowerShell. This technique is often used as a method to load malicious content into memory afterward.
8references:
9 - https://speakerdeck.com/heirhabarov/hunting-for-powershell-abuse?slide=43
10author: frack113
11date: 2022-12-23
12tags:
13 - attack.command-and-control
14 - attack.t1132.001
15logsource:
16 product: windows
17 category: process_creation
18detection:
19 selection:
20 CommandLine|contains|all:
21 - 'FromBase64String'
22 - 'MemoryStream'
23 - 'H4sI'
24 condition: selection
25falsepositives:
26 - Legitimate administrative script
27level: medium
References
Related rules
- DNS Exfiltration and Tunneling Tools Execution
- Gzip Archive Decode Via PowerShell
- Suspicious FromBase64String Usage On Gzip Archive - Ps Script
- ADSI-Cache File Creation By Uncommon Tool
- Activity from Anonymous IP Addresses