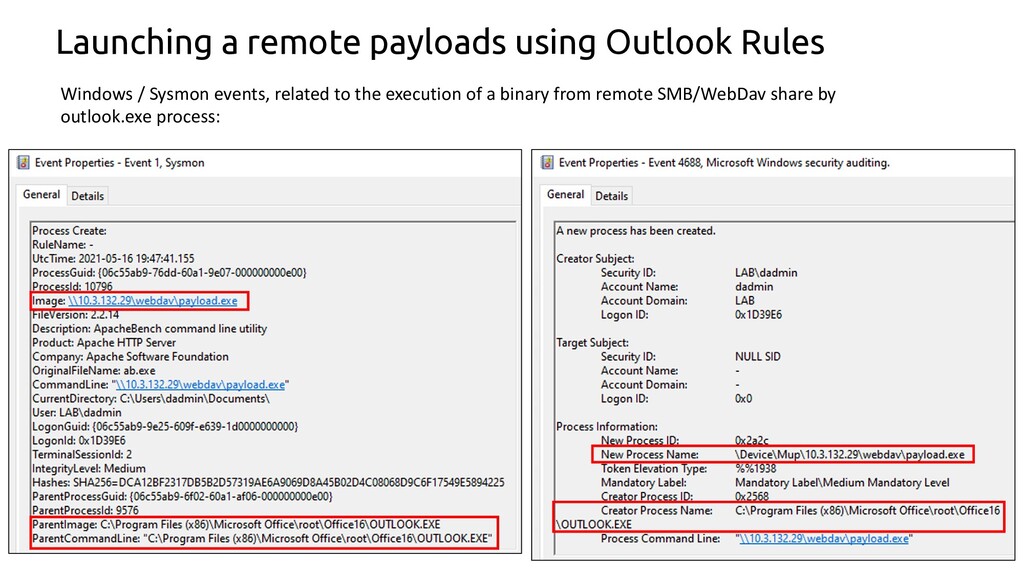
Suspicious Remote Child Process From Outlook
Detects a suspicious child process spawning from Outlook where the image is located in a remote location (SMB/WebDav shares).
Sigma rule (View on GitHub)
1title: Suspicious Remote Child Process From Outlook
2id: e212d415-0e93-435f-9e1a-f29005bb4723
3related:
4 - id: 208748f7-881d-47ac-a29c-07ea84bf691d # Outlook Child Processes
5 type: similar
6status: test
7description: Detects a suspicious child process spawning from Outlook where the image is located in a remote location (SMB/WebDav shares).
8references:
9 - https://github.com/sensepost/ruler
10 - https://www.fireeye.com/blog/threat-research/2018/12/overruled-containing-a-potentially-destructive-adversary.html
11 - https://speakerdeck.com/heirhabarov/hunting-for-persistence-via-microsoft-exchange-server-or-outlook?slide=49
12author: Markus Neis, Nasreddine Bencherchali (Nextron Systems)
13date: 2018/12/27
14modified: 2023/02/09
15tags:
16 - attack.execution
17 - attack.t1059
18 - attack.t1202
19logsource:
20 category: process_creation
21 product: windows
22detection:
23 selection:
24 ParentImage|endswith: '\outlook.exe'
25 Image|startswith: '\\\\'
26 condition: selection
27falsepositives:
28 - Unknown
29level: high
References
Related rules
- Renamed CURL.EXE Execution
- LOLBIN Execution Of The FTP.EXE Binary
- Suspicious Runscripthelper.exe
- Outlook EnableUnsafeClientMailRules Setting Enabled
- Renamed FTP.EXE Execution