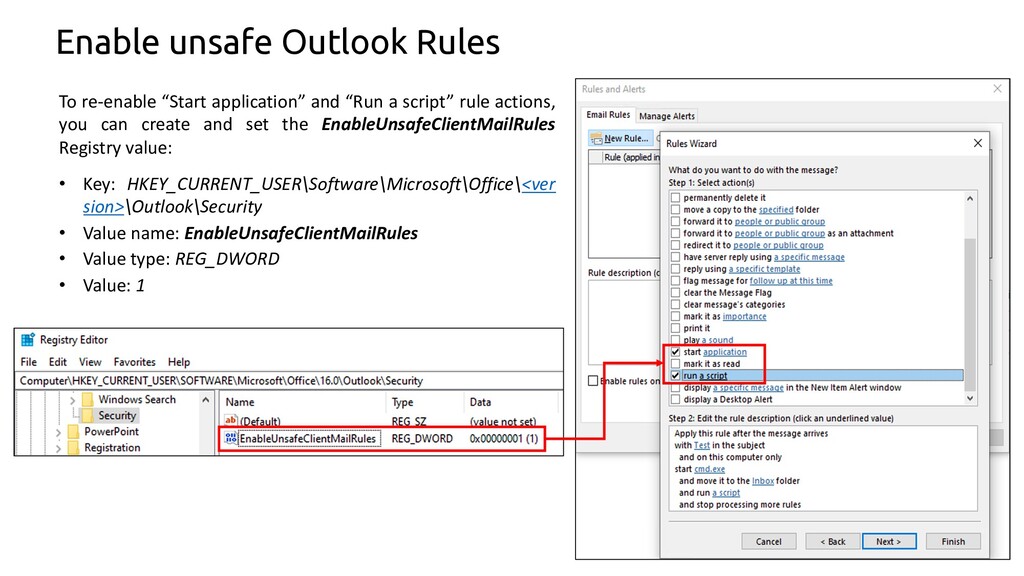
Outlook EnableUnsafeClientMailRules Setting Enabled
Detects an attacker trying to enable the outlook security setting "EnableUnsafeClientMailRules" which allows outlook to run applications or execute macros
Sigma rule (View on GitHub)
1title: Outlook EnableUnsafeClientMailRules Setting Enabled
2id: 55f0a3a1-846e-40eb-8273-677371b8d912
3related:
4 - id: 6763c6c8-bd01-4687-bc8d-4fa52cf8ba08 # Registry variation
5 type: similar
6status: test
7description: Detects an attacker trying to enable the outlook security setting "EnableUnsafeClientMailRules" which allows outlook to run applications or execute macros
8references:
9 - https://www.fireeye.com/blog/threat-research/2018/12/overruled-containing-a-potentially-destructive-adversary.html
10 - https://speakerdeck.com/heirhabarov/hunting-for-persistence-via-microsoft-exchange-server-or-outlook?slide=44
11 - https://support.microsoft.com/en-us/topic/how-to-control-the-rule-actions-to-start-an-application-or-run-a-macro-in-outlook-2016-and-outlook-2013-e4964b72-173c-959d-5d7b-ead562979048
12author: Markus Neis, Nasreddine Bencherchali (Nextron Systems)
13date: 2018/12/27
14modified: 2023/02/09
15tags:
16 - attack.execution
17 - attack.t1059
18 - attack.t1202
19logsource:
20 category: process_creation
21 product: windows
22detection:
23 selection:
24 CommandLine|contains: '\Outlook\Security\EnableUnsafeClientMailRules'
25 condition: selection
26falsepositives:
27 - Unknown
28level: high
References
Related rules
- Renamed FTP.EXE Execution
- Run PowerShell Script from Redirected Input Stream
- Hacktool Ruler
- Suspicious User-Initiated Process Execution on External Drive (Old)
- Suspicious User-Initiated Process Execution on External Drive (Sysmon)