NTDS.DIT Creation By Uncommon Parent Process
Detects creation of a file named "ntds.dit" (Active Directory Database) by an uncommon parent process or directory
Sigma rule (View on GitHub)
1title: NTDS.DIT Creation By Uncommon Parent Process
2id: 4e7050dd-e548-483f-b7d6-527ab4fa784d
3related:
4 - id: 11b1ed55-154d-4e82-8ad7-83739298f720
5 type: similar
6status: test
7description: Detects creation of a file named "ntds.dit" (Active Directory Database) by an uncommon parent process or directory
8references:
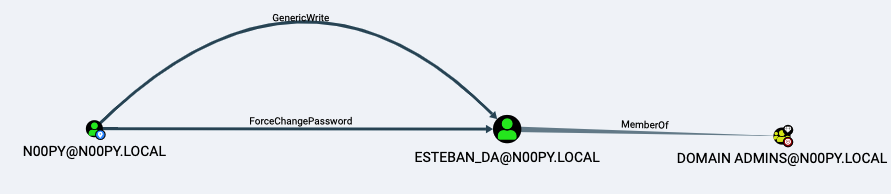
9 - https://www.ired.team/offensive-security/credential-access-and-credential-dumping/ntds.dit-enumeration
10 - https://www.n00py.io/2022/03/manipulating-user-passwords-without-mimikatz/
11 - https://pentestlab.blog/tag/ntds-dit/
12 - https://github.com/samratashok/nishang/blob/414ee1104526d7057f9adaeee196d91ae447283e/Gather/Copy-VSS.ps1
13author: Florian Roth (Nextron Systems)
14date: 2022/03/11
15modified: 2023/01/05
16tags:
17 - attack.credential_access
18 - attack.t1003.003
19logsource:
20 product: windows
21 category: file_event
22 definition: 'Requirements: The "ParentImage" field is not available by default on EID 11 of Sysmon logs. To be able to use this rule to the full extent you need to enrich the log with additional ParentImage data'
23detection:
24 selection_file:
25 TargetFilename|endswith: '\ntds.dit'
26 selection_process_parent:
27 # Note: ParentImage is a custom field and is not available by default on Sysmon EID 11
28 ParentImage|endswith:
29 - '\cscript.exe'
30 - '\httpd.exe'
31 - '\nginx.exe'
32 - '\php-cgi.exe'
33 - '\powershell.exe'
34 - '\pwsh.exe'
35 - '\w3wp.exe'
36 - '\wscript.exe'
37 selection_process_parent_path:
38 # Note: ParentImage is a custom field and is not available by default on Sysmon EID 11
39 ParentImage|contains:
40 - '\apache'
41 - '\tomcat'
42 - '\AppData\'
43 - '\Temp\'
44 - '\Public\'
45 - '\PerfLogs\'
46 condition: selection_file and 1 of selection_process_*
47falsepositives:
48 - Unknown
49level: high
References
Related rules
- NTDS Exfiltration Filename Patterns
- NTDS.DIT Creation By Uncommon Process
- VolumeShadowCopy Symlink Creation Via Mklink
- Copying Sensitive Files with Credential Data
- Transferring Files with Credential Data via Network Shares