Suspicious File Download From File Sharing Websites
Detects the download of suspicious file type from a well-known file and paste sharing domain
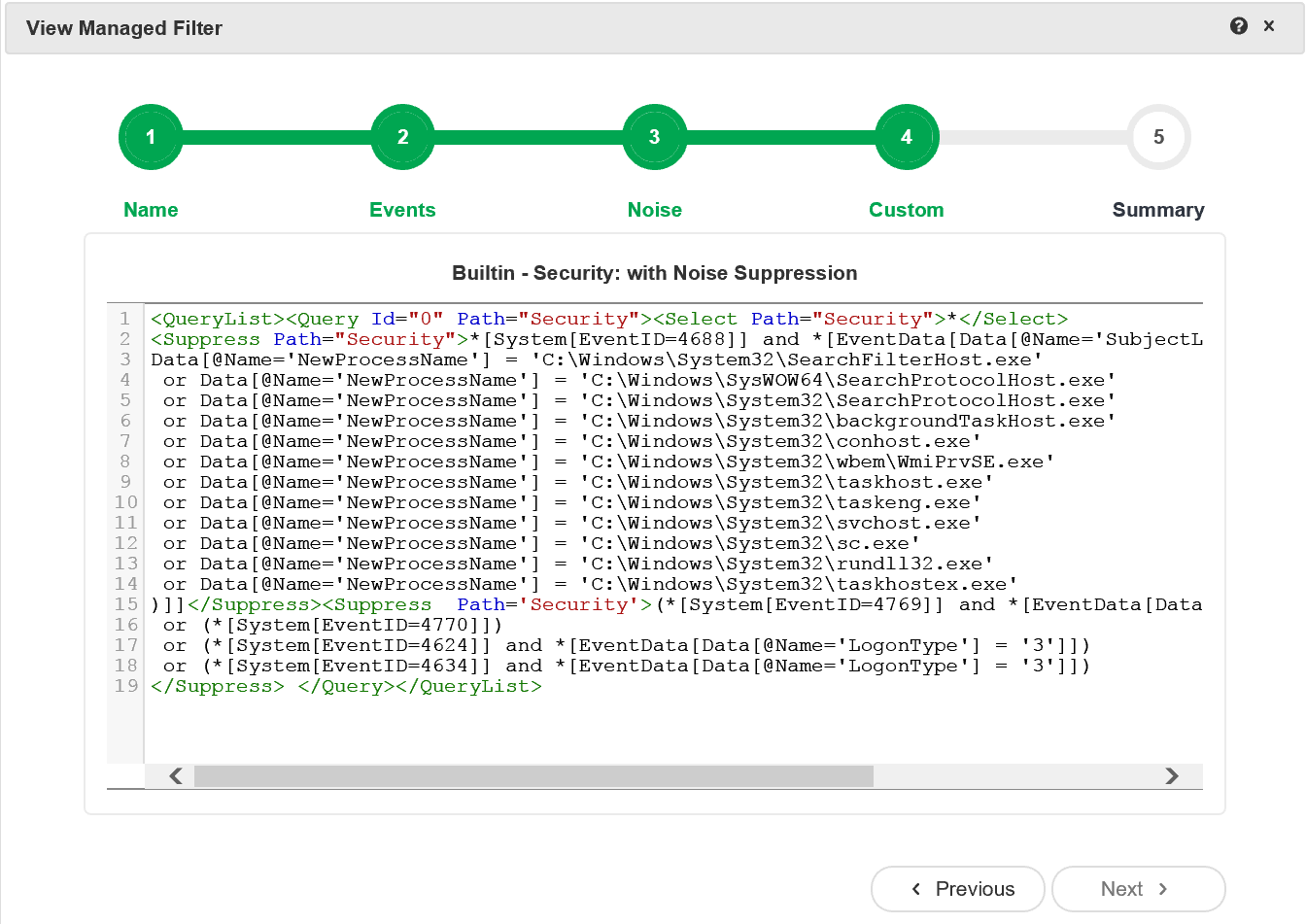
Sigma rule (View on GitHub)
1title: Suspicious File Download From File Sharing Websites
2id: 52182dfb-afb7-41db-b4bc-5336cb29b464
3related:
4 - id: ae02ed70-11aa-4a22-b397-c0d0e8f6ea99
5 type: similar
6status: experimental
7description: Detects the download of suspicious file type from a well-known file and paste sharing domain
8references:
9 - https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=90015
10 - https://www.cisa.gov/uscert/ncas/alerts/aa22-321a
11 - https://fabian-voith.de/2020/06/25/sysmon-v11-1-reads-alternate-data-streams/
12 - https://www.microsoft.com/en-us/security/blog/2024/01/17/new-ttps-observed-in-mint-sandstorm-campaign-targeting-high-profile-individuals-at-universities-and-research-orgs/
13author: Florian Roth (Nextron Systems)
14date: 2022/08/24
15modified: 2024/02/09
16tags:
17 - attack.defense_evasion
18 - attack.s0139
19 - attack.t1564.004
20logsource:
21 product: windows
22 category: create_stream_hash
23detection:
24 selection_domain:
25 Contents|contains:
26 - '.githubusercontent.com' # Includes both gists and github repositories / Michael Haag (idea)
27 - 'anonfiles.com'
28 - 'cdn.discordapp.com'
29 - 'cdn.discordapp.com/attachments/'
30 - 'ddns.net'
31 - 'dl.dropboxusercontent.com'
32 - 'ghostbin.co'
33 - 'glitch.me'
34 - 'gofile.io'
35 - 'hastebin.com'
36 - 'mediafire.com'
37 - 'mega.nz'
38 - 'onrender.com'
39 - 'paste.ee'
40 - 'pastebin.com'
41 - 'pastebin.pl'
42 - 'pastetext.net'
43 - 'privatlab.com'
44 - 'privatlab.net'
45 - 'send.exploit.in'
46 - 'sendspace.com'
47 - 'storage.googleapis.com'
48 - 'storjshare.io'
49 - 'supabase.co'
50 - 'temp.sh'
51 - 'transfer.sh'
52 - 'ufile.io'
53 selection_extension:
54 TargetFilename|contains:
55 - '.exe:Zone'
56 - '.vbs:Zone'
57 - '.vbe:Zone'
58 - '.dll:Zone'
59 - '.one:Zone'
60 - '.hta:Zone'
61 - '.lnk:Zone'
62 - '.xll:Zone'
63 - '.cpl:Zone'
64 condition: all of selection*
65falsepositives:
66 - Some false positives might occur with binaries download via Github
67level: high
References
Related rules
- Unusual File Download From File Sharing Websites
- HackTool Named File Stream Created
- Hidden Executable In NTFS Alternate Data Stream
- Potential Rundll32 Execution With DLL Stored In ADS
- Unusual File Download from Direct IP Address