Suspicious DNS Z Flag Bit Set
The DNS Z flag is bit within the DNS protocol header that is, per the IETF design, meant to be used reserved (unused). Although recently it has been used in DNSSec, the value being set to anything other than 0 should be rare. Otherwise if it is set to non 0 and DNSSec is being used, then excluding the legitimate domains is low effort and high reward. Determine if multiple of these files were accessed in a short period of time to further enhance the possibility of seeing if this was a one off or the possibility of larger sensitive file gathering. This Sigma query is designed to accompany the Corelight Threat Hunting Guide, which can be found here: https://www3.corelight.com/corelights-introductory-guide-to-threat-hunting-with-zeek-bro-logs'
Sigma rule (View on GitHub)
1title: Suspicious DNS Z Flag Bit Set
2id: ede05abc-2c9e-4624-9944-9ff17fdc0bf5
3status: test
4description: |
5 The DNS Z flag is bit within the DNS protocol header that is, per the IETF design, meant to be used reserved (unused).
6 Although recently it has been used in DNSSec, the value being set to anything other than 0 should be rare.
7 Otherwise if it is set to non 0 and DNSSec is being used, then excluding the legitimate domains is low effort and high reward.
8 Determine if multiple of these files were accessed in a short period of time to further enhance the possibility of seeing if this was a one off or the possibility of larger sensitive file gathering.
9 This Sigma query is designed to accompany the Corelight Threat Hunting Guide, which can be found here: https://www3.corelight.com/corelights-introductory-guide-to-threat-hunting-with-zeek-bro-logs'
10references:
11 - https://twitter.com/neu5ron/status/1346245602502443009
12 - https://tdm.socprime.com/tdm/info/eLbyj4JjI15v#sigma
13 - https://tools.ietf.org/html/rfc2929#section-2.1
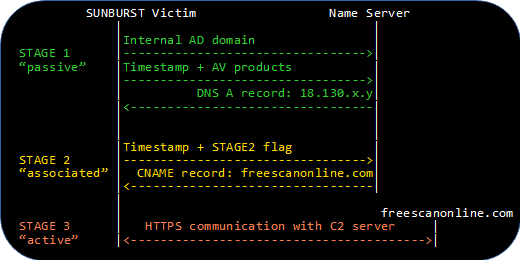
14 - https://www.netresec.com/?page=Blog&month=2021-01&post=Finding-Targeted-SUNBURST-Victims-with-pDNS
15author: '@neu5ron, SOC Prime Team, Corelight'
16date: 2021/05/04
17modified: 2022/11/29
18tags:
19 - attack.t1095
20 - attack.t1571
21 - attack.command_and_control
22logsource:
23 product: zeek
24 service: dns
25detection:
26 z_flag_unset:
27 Z: 0
28 most_probable_valid_domain:
29 query|contains: '.'
30 exclude_tlds:
31 query|endswith:
32 - '.arpa'
33 - '.local'
34 - '.ultradns.net'
35 - '.twtrdns.net'
36 - '.azuredns-prd.info'
37 - '.azure-dns.com'
38 - '.azuredns-ff.info'
39 - '.azuredns-ff.org'
40 - '.azuregov-dns.org'
41 exclude_query_types:
42 qtype_name:
43 - 'ns'
44 - 'mx'
45 exclude_responses:
46 answers|endswith: '\\x00'
47 exclude_netbios:
48 id.resp_p:
49 - 137
50 - 138
51 - 139
52 condition: not z_flag_unset and most_probable_valid_domain and not (exclude_tlds or exclude_query_types or exclude_responses or exclude_netbios)
53falsepositives:
54 - 'Internal or legitimate external domains using DNSSec. Verify if these are legitimate DNSSec domains and then exclude them.'
55 - 'If you work in a Public Sector then it may be good to exclude things like endswith ".edu", ".gov" and or ".mil"'
56level: medium
References
Related rules
- Netcat The Powershell Version
- Suspicious Werfault.exe Network Connection Outbound
- HackTool - Htran/NATBypass Execution
- PUA - Fast Reverse Proxy (FRP) Execution
- PUA - NPS Tunneling Tool Execution