Download File To Potentially Suspicious Directory Via Wget
Detects the use of wget to download content to a suspicious directory
Sigma rule (View on GitHub)
1title: Download File To Potentially Suspicious Directory Via Wget
2id: cf610c15-ed71-46e1-bdf8-2bd1a99de6c4
3status: test
4description: Detects the use of wget to download content to a suspicious directory
5references:
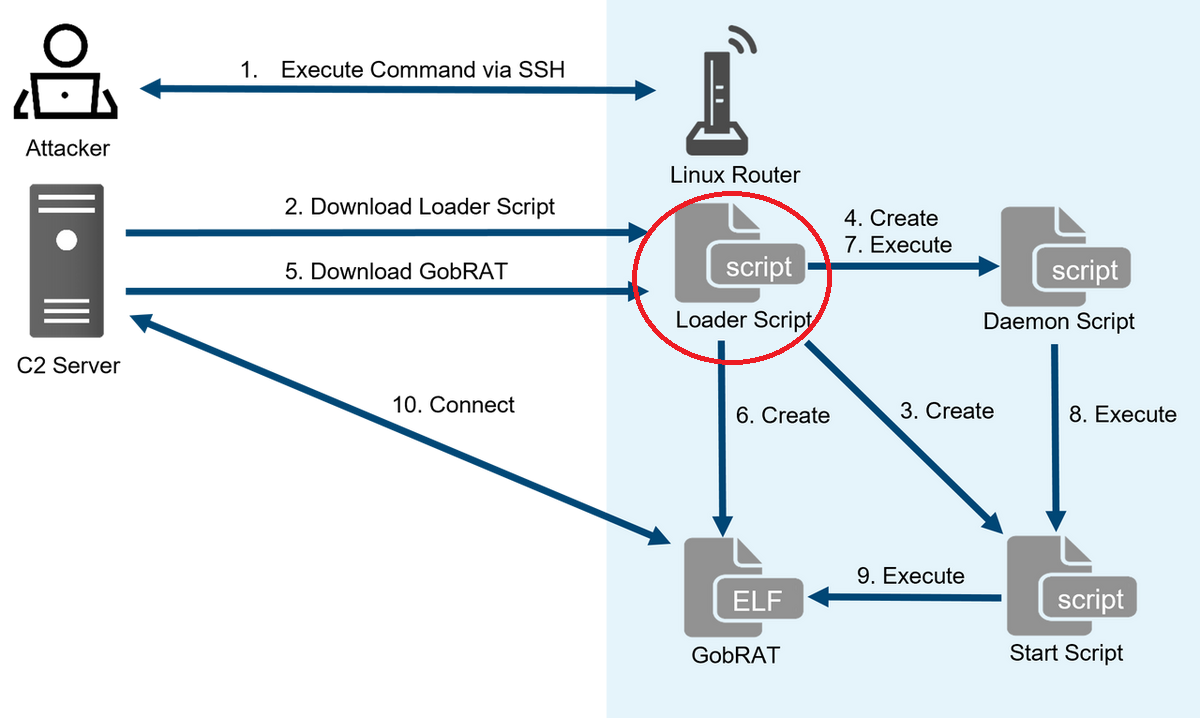
6 - https://blogs.jpcert.or.jp/en/2023/05/gobrat.html
7 - https://jstnk9.github.io/jstnk9/research/GobRAT-Malware/
8 - https://www.virustotal.com/gui/file/60bcd645450e4c846238cf0e7226dc40c84c96eba99f6b2cffcd0ab4a391c8b3/detection
9 - https://www.virustotal.com/gui/file/3e44c807a25a56f4068b5b8186eee5002eed6f26d665a8b791c472ad154585d1/detection
10author: Joseliyo Sanchez, @Joseliyo_Jstnk
11date: 2023/06/02
12tags:
13 - attack.command_and_control
14 - attack.t1105
15logsource:
16 category: process_creation
17 product: linux
18detection:
19 selection_img:
20 Image|endswith: '/wget'
21 selection_output:
22 - CommandLine|re: '\s-O\s' # We use regex to ensure a case sensitive argument detection
23 - CommandLine|contains: '--output-document'
24 selection_path:
25 CommandLine|contains: '/tmp/'
26 condition: all of selection_*
27falsepositives:
28 - Unknown
29level: medium
References
Related rules
- Wget Creating Files in Tmp Directory
- Pandemic Registry Key
- BITSAdmin Downloading Malicious Binaries
- CertUtil Downloading Malicious Binaries
- Certreq Downloading Malicious Binaries