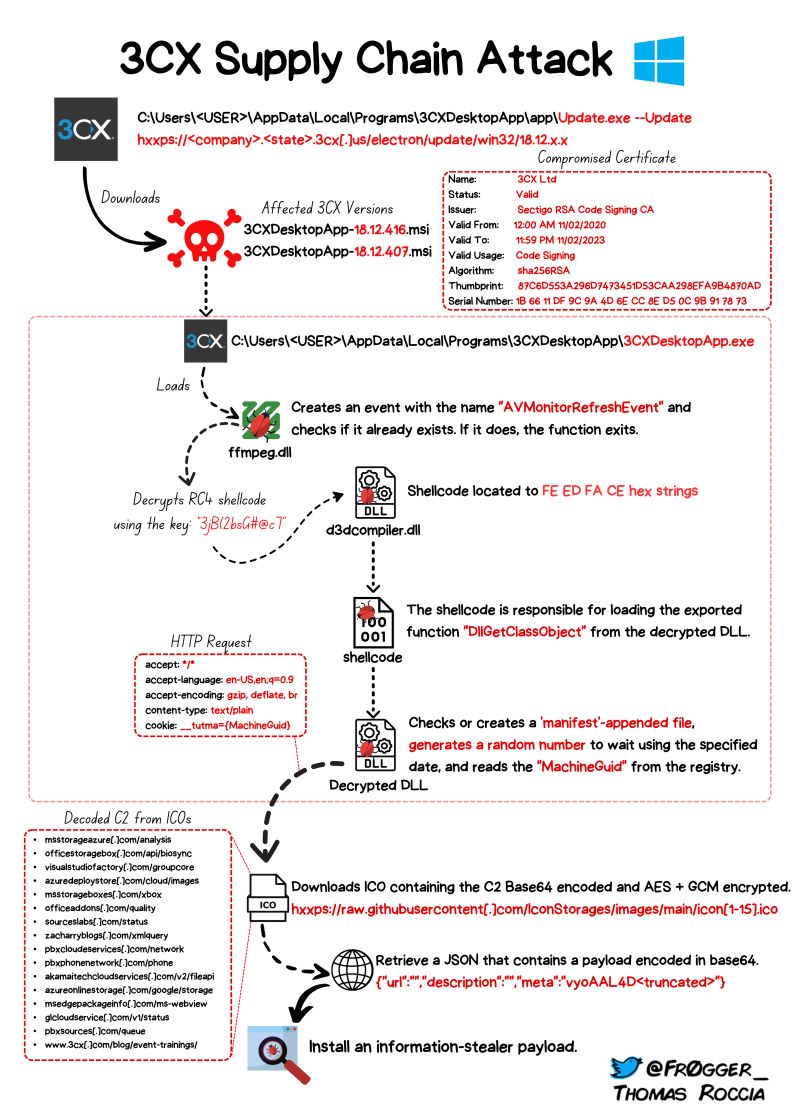
Potential Compromised 3CXDesktopApp ICO C2 File Download
Detects potential malicious .ICO files download from a compromised 3CXDesktopApp via web requests to the the malicious Github repository
Sigma rule (View on GitHub)
1title: Potential Compromised 3CXDesktopApp ICO C2 File Download
2id: 76bc1601-9546-4b75-9419-06e0e8d10651
3related:
4 - id: 3c4b3bbf-36b4-470c-b6cf-f07e8b1c7e26 # Proxy C2
5 type: similar
6 - id: bd03a0dc-5d93-49eb-b2e8-2dfd268600f8 # DNS C2
7 type: similar
8 - id: 51eecf75-d069-43c7-9ea2-63f75499edd4 # net_connection C2
9 type: similar
10 - id: 93bbde78-dc86-4e73-9ffc-ff8a384ca89c # ProcCreation Exec
11 type: similar
12 - id: 63f3605b-979f-48c2-b7cc-7f90523fed88 # ProcCreation ChildProc
13 type: similar
14 - id: e7581747-1e44-4d4b-85a6-0db0b4a00f2a # ProcCreation Update
15 type: similar
16 - id: d0b65ad3-e945-435e-a7a9-438e62dd48e9 # ImageLoad
17 type: similar
18status: test
19description: Detects potential malicious .ICO files download from a compromised 3CXDesktopApp via web requests to the the malicious Github repository
20references:
21 - https://www.sentinelone.com/blog/smoothoperator-ongoing-campaign-trojanizes-3cx-software-in-software-supply-chain-attack/
22 - https://www.linkedin.com/feed/update/urn:li:activity:7047435754834198529/
23author: Nasreddine Bencherchali (Nextron Systems)
24date: 2023/03/31
25tags:
26 - attack.command_and_control
27 - detection.emerging_threats
28logsource:
29 category: proxy
30detection:
31 selection:
32 c-uri|contains|all:
33 - 'IconStorages/images/main/icon'
34 - '.ico'
35 condition: selection
36falsepositives:
37 - Unknown
38level: high
References
Related rules
- OilRig APT Schedule Task Persistence - System
- Potential Compromised 3CXDesktopApp Beaconing Activity - DNS
- Potential Compromised 3CXDesktopApp Beaconing Activity - Netcon
- Potential Suspicious Child Process Of 3CXDesktopApp
- Equation Group C2 Communication