DarkGate - Autoit3.EXE Execution Parameters
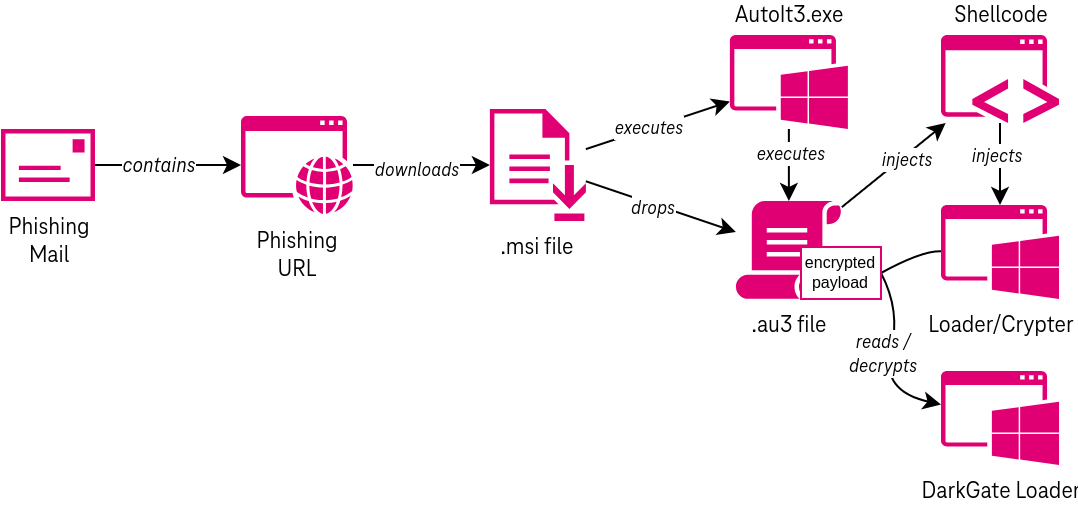
Detects execution of the legitimate Autoit3 utility from a suspicious parent process. AutoIt3.exe is used within the DarkGate infection chain to execute shellcode that performs process injection and connects to the DarkGate command-and-control server.
Sigma rule (View on GitHub)
1title: DarkGate - Autoit3.EXE Execution Parameters
2id: f8e9aa1c-14f2-4dbd-aa59-b98968ed650d
3status: experimental
4description: |
5 Detects execution of the legitimate Autoit3 utility from a suspicious parent process. AutoIt3.exe is used within
6 the DarkGate infection chain to execute shellcode that performs process injection and connects to the DarkGate
7 command-and-control server.
8references:
9 - https://github.security.telekom.com/2023/08/darkgate-loader.html
10 - https://www.kroll.com/en/insights/publications/cyber/microsoft-teams-used-as-initial-access-for-darkgate-malware
11 - https://github.com/pr0xylife/DarkGate/tree/main
12author: Micah Babinski
13date: 2023/10/15
14tags:
15 - attack.execution
16 - attack.t1059
17 - detection.emerging_threats
18logsource:
19 category: process_creation
20 product: windows
21detection:
22 selection_proc:
23 - Image|endswith: '\Autoit3.exe'
24 - OriginalFileName: 'AutoIt3.exe'
25 selection_parent:
26 ParentImage|endswith:
27 - '\cmd.exe'
28 - '\KeyScramblerLogon.exe'
29 - '\msiexec.exe'
30 filter_main_legit_autoit_location:
31 Image|endswith:
32 - ':\Program Files (x86)\AutoIt3\AutoIt3.exe'
33 - ':\Program Files\AutoIt3\AutoIt3.exe'
34 condition: all of selection_* and not 1 of filter_main_*
35falsepositives:
36 - Unlikely
37level: high
References
Related rules
- DarkGate - Autoit3.EXE File Creation By Uncommon Process
- Turla Group Lateral Movement
- Lazarus Group Activity
- Potential Atlassian Confluence CVE-2021-26084 Exploitation Attempt
- Potential CVE-2021-40444 Exploitation Attempt