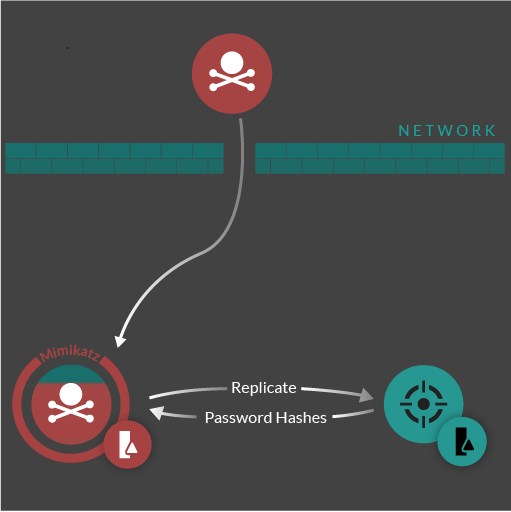
Possible Impacket Secretsdump.py Activity
Detects attempts to retrieve/dump credentials using the DL_DRSGetNCChanges() method.
Sigma rule (View on GitHub)
1title: Possible Impacket Secretsdump.py Activity
2id: 8d1476b7-0f57-43a4-b56b-50bfab66943d
3status: experimental
4description: Detects attempts to retrieve/dump credentials using the DL_DRSGetNCChanges() method.
5references:
6 - https://www.extrahop.com/company/blog/2021/dcsync-definition-and-protection/
7 - https://www.secureauth.com/labs/open-source-tools/impacket/
8 - https://wiki.samba.org/index.php/DRSUAPI
9 - https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-drsr/9b4bfb44-6656-4404-bcc8-dc88111658b3
10author: Micah Babinski
11date: 2023/04/13
12tags:
13 - attack.s0357
14 - attack.credential_access
15 - attack.t1003
16 - attack.t1003.003
17 - attack.t1003.006
18logsource:
19 product: zeek
20 service: dce_rpc
21detection:
22 selection:
23 operation: DRSGetNCChanges
24 endpoint: drsuapi
25 id.resp_p: 49666
26 named_pipe: 49666
27 condition: selection
28fields:
29 - id.orig_h
30falsepositives:
31 - This may detect legitimate Active Directory domain control replication/sync activity (perhaps filter by inbound/outbound IP addresses of your known DCs)
32level: low```
References
Related rules
- Esentutl Gather Credentials
- Mimikatz Command Line With Ticket Export
- NTDSutil Pulling of NTDS.dit File
- Credential Dumping Tools Service Execution - Security
- Potential Russian APT Credential Theft Activity