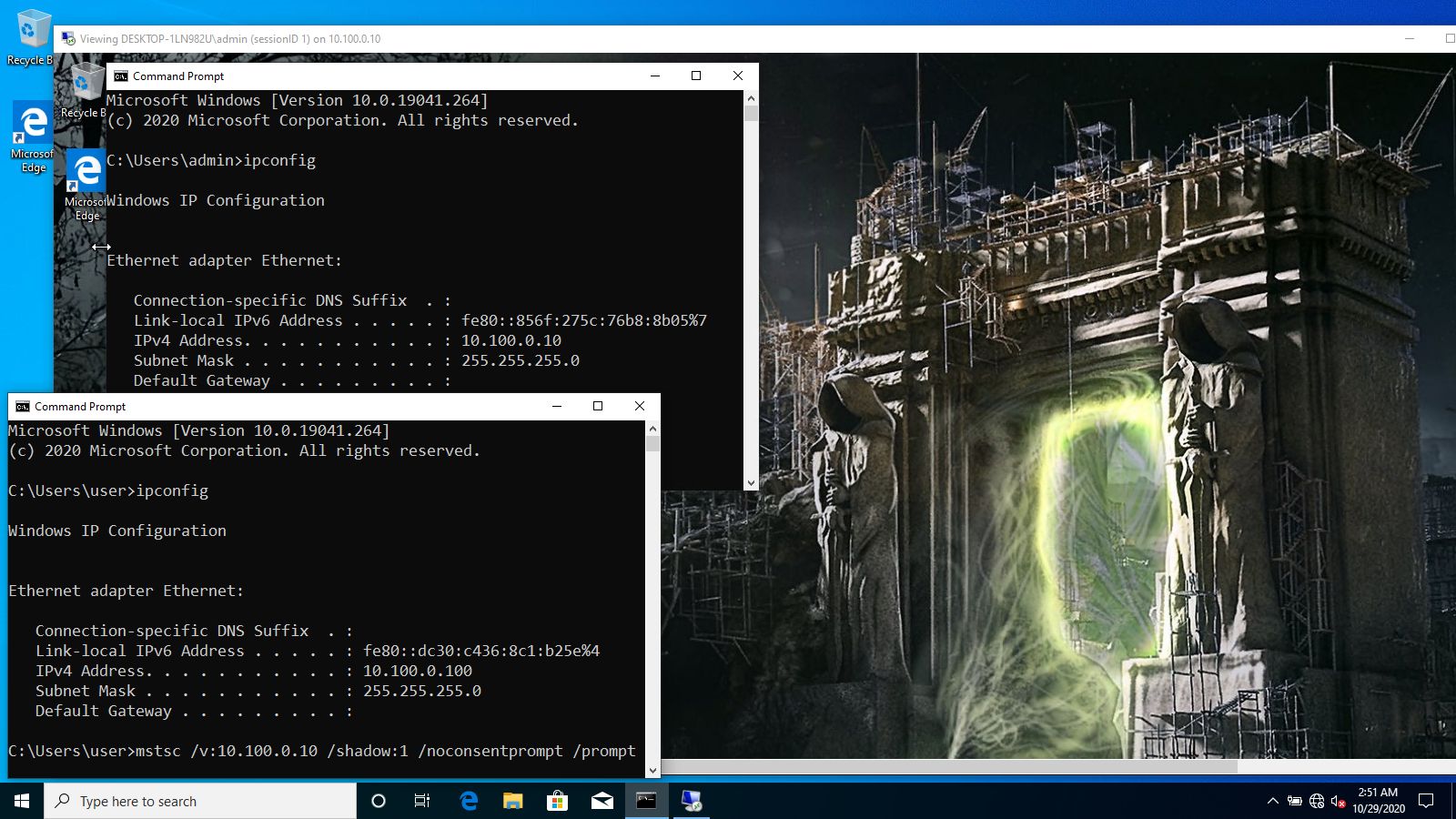
Potential Remote Desktop Shadowing Activity
Identifies the modification of the Remote Desktop Protocol (RDP) Shadow registry or the execution of processes indicative of an active RDP shadowing session. An adversary may abuse the RDP Shadowing feature to spy on or control other users active RDP sessions.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2021/04/12"
3integration = ["endpoint", "windows"]
4maturity = "production"
5updated_date = "2024/05/21"
6
7[rule]
8author = ["Elastic"]
9description = """
10Identifies the modification of the Remote Desktop Protocol (RDP) Shadow registry or the execution of processes
11indicative of an active RDP shadowing session. An adversary may abuse the RDP Shadowing feature to spy on or control
12other users active RDP sessions.
13"""
14from = "now-9m"
15index = [
16 "logs-endpoint.events.process-*",
17 "logs-endpoint.events.registry-*",
18 "winlogbeat-*",
19 "logs-windows.sysmon_operational-*",
20 "endgame-*",
21]
22language = "eql"
23license = "Elastic License v2"
24name = "Potential Remote Desktop Shadowing Activity"
25references = [
26 "https://bitsadm.in/blog/spying-on-users-using-rdp-shadowing",
27 "https://swarm.ptsecurity.com/remote-desktop-services-shadowing/",
28]
29risk_score = 73
30rule_id = "c57f8579-e2a5-4804-847f-f2732edc5156"
31setup = """## Setup
32
33If enabling an EQL rule on a non-elastic-agent index (such as beats) for versions <8.2,
34events will not define `event.ingested` and default fallback for EQL rules was not added until version 8.2.
35Hence for this rule to work effectively, users will need to add a custom ingest pipeline to populate
36`event.ingested` to @timestamp.
37For more details on adding a custom ingest pipeline refer - https://www.elastic.co/guide/en/fleet/current/data-streams-pipeline-tutorial.html
38"""
39severity = "high"
40tags = [
41 "Domain: Endpoint",
42 "OS: Windows",
43 "Use Case: Threat Detection",
44 "Tactic: Lateral Movement",
45 "Data Source: Elastic Endgame",
46 "Data Source: Elastic Defend",
47 "Data Source: Sysmon",
48]
49timestamp_override = "event.ingested"
50type = "eql"
51
52query = '''
53/* Identifies the modification of RDP Shadow registry or
54 the execution of processes indicative of active shadow RDP session */
55
56any where host.os.type == "windows" and
57(
58 (event.category == "registry" and
59 registry.path : (
60 "HKLM\\Software\\Policies\\Microsoft\\Windows NT\\Terminal Services\\Shadow",
61 "\\REGISTRY\\MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Terminal Services\\Shadow"
62 )
63 ) or
64 (event.category == "process" and event.type == "start" and
65 (process.name : ("RdpSaUacHelper.exe", "RdpSaProxy.exe") and process.parent.name : "svchost.exe") or
66 (process.pe.original_file_name : "mstsc.exe" and process.args : "/shadow:*")
67 )
68)
69'''
70
71
72[[rule.threat]]
73framework = "MITRE ATT&CK"
74[[rule.threat.technique]]
75id = "T1021"
76name = "Remote Services"
77reference = "https://attack.mitre.org/techniques/T1021/"
78[[rule.threat.technique.subtechnique]]
79id = "T1021.001"
80name = "Remote Desktop Protocol"
81reference = "https://attack.mitre.org/techniques/T1021/001/"
82
83
84
85[rule.threat.tactic]
86id = "TA0008"
87name = "Lateral Movement"
88reference = "https://attack.mitre.org/tactics/TA0008/"
References
Related rules
- Lateral Movement via Startup Folder
- Microsoft Exchange Server UM Writing Suspicious Files
- NullSessionPipe Registry Modification
- RDP Enabled via Registry
- Suspicious RDP ActiveX Client Loaded