PowerShell Share Enumeration Script
Detects PowerShell scripts that uses ShareFinder functions (Invoke-ShareFinder/Invoke-ShareFinderThreaded) or Windows share enumeration APIs (shi1_netname/shi1_remark with NetShareEnum/NetApiBufferFree). Attackers use share enumeration to map accessible network shares for collection, lateral movement, or ransomware targeting.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2022/08/17"
3integration = ["windows"]
4maturity = "production"
5updated_date = "2026/02/09"
6
7[rule]
8author = ["Elastic"]
9description = """
10Detects PowerShell scripts that uses ShareFinder functions (Invoke-ShareFinder/Invoke-ShareFinderThreaded) or Windows
11share enumeration APIs (shi1_netname/shi1_remark with NetShareEnum/NetApiBufferFree). Attackers use share enumeration to
12map accessible network shares for collection, lateral movement, or ransomware targeting.
13"""
14from = "now-9m"
15index = ["winlogbeat-*", "logs-windows.powershell*"]
16language = "kuery"
17license = "Elastic License v2"
18name = "PowerShell Share Enumeration Script"
19note = """## Triage and analysis
20
21> **Disclaimer**:
22> This guide was created by humans with the assistance of generative AI. While its contents have been manually curated to include the most valuable information, always validate assumptions and adjust procedures to match your internal runbooks and incident triage and response policies.
23
24### Investigating PowerShell Share Enumeration Script
25
26This alert indicates PowerShell script block content consistent with Windows network share enumeration. The matched text includes ShareFinder functions (for example, `Invoke-ShareFinder` or `Invoke-ShareFinderThreaded`) and/or native share enumeration API references (for example, `NetShareEnum` / `NetApiBufferFree` and `shi1_netname` / `shi1_remark`). Share discovery can be a normal administrative activity, but in attacks it is frequently used to map accessible shares prior to data collection, lateral movement, or impact activity.
27
28#### Key alert fields to review
29
30- `user.name`, `user.domain`, `user.id`: Account execution context for correlation, prioritization, and scoping.
31- `host.name`, `host.id`: Host execution context for correlation, prioritization, and scoping.
32- `powershell.file.script_block_text`: Script block content that matched the detection logic.
33- `powershell.file.script_block_id`, `powershell.sequence`, `powershell.total`: Script block metadata to pivot to other fragments or reconstruct full script content when split across multiple events.
34- `file.path`, `file.directory`, `file.name`: File-origin context when the script block is sourced from an on-disk file.
35- `powershell.file.script_block_length`: Script block length (size) context.
36
37#### Possible investigation steps
38
39- Establish context and triage priority:
40 - Use `@timestamp` as the activity anchor and note the executing `user.name` / `user.domain` / `user.id` and affected `host.name` / `host.id`.
41 - Determine whether the account and host are expected to perform share inventory (for example, administrative workstation or management server vs. a standard user endpoint).
42 - Check whether similar share enumeration activity has occurred recently for the same `user.id` or on the same `host.id` to identify repeated scanning or automation.
43
44- Review the script block content and classify the activity:
45 - Inspect `powershell.file.script_block_text` and capture relevant excerpts for the case record (function names, API calls, and any referenced hosts/shares).
46 - Differentiate between a function definition/import and an actual invocation:
47 - Function definition or module load (lower confidence): the text contains the function name as part of a definition or import logic.
48 - Function invocation (higher confidence): the text shows parameters, target lists, or loops that initiate enumeration.
49 - Identify which pattern is present and what it implies about scope:
50 - `Invoke-ShareFinder`: share discovery logic implemented in PowerShell.
51 - `Invoke-ShareFinderThreaded`: broader or faster discovery due to concurrent enumeration.
52 - `NetShareEnum` / `NetApiBufferFree` with `shi1_netname` / `shi1_remark`: direct use of Windows share enumeration APIs and may reflect customized scripting.
53 - Extract scoping and intent details from the text when available:
54 - Target hostnames/IPs, server lists, domain-related identifiers, or UNC paths.
55 - Filters for share names and remarks, or include/exclude logic that focuses discovery on specific systems or shares.
56 - Use of alternate credentials or explicit authentication material embedded in the script (if present).
57 - Any output handling (formatting, writing results to disk, or staging).
58
59- Reconstruct full content when script blocks are split:
60 - Pivot on `powershell.file.script_block_id` to collect all related fragments for the same execution context.
61 - Use `powershell.sequence` and `powershell.total` to order fragments and identify missing pieces (if populated).
62 - Review adjacent script blocks for the same `host.id` and `user.id` near `@timestamp` to capture supporting functions or follow-on actions that may not appear in the triggering fragment.
63
64- Determine whether the activity originated from an on-disk script:
65 - If present, use `file.path` / `file.directory` / `file.name` to identify the script source.
66 - Assess whether the script location and name align with approved administrative tooling. Scripts originating from user-writable or temporary locations are higher risk than centrally managed locations.
67 - If an on-disk script is involved, preserve the file for further analysis and determine whether it appears on additional hosts (pivot on `file.name` where applicable).
68
69- Scope across users and hosts:
70 - Look for additional events containing the same discovery keywords in `powershell.file.script_block_text` to identify other affected endpoints.
71 - Check whether the same `user.id` performed similar activity from multiple `host.id` values in a short period, which can indicate automation or credential misuse.
72 - Identify whether multiple users are performing similar enumeration from the same host, which can indicate a shared jump box or a compromised administrative endpoint.
73
74- Correlate with adjacent telemetry (as available) to confirm intent and detect follow-on behavior:
75 - Process execution telemetry on the same `host.id` around `@timestamp` to determine how PowerShell was launched and whether the initiating process and execution pattern are consistent with expected activity for `user.id`.
76 - Network telemetry around `@timestamp` for access to multiple remote hosts consistent with share enumeration and subsequent SMB activity.
77 - Authentication telemetry for `user.id` around `@timestamp` for unusual access to file servers or multiple servers, especially if the behavior is new for the account.
78 - File activity telemetry (endpoint and/or file server) for unusual access patterns to shared locations following the enumeration (for example, rapid directory traversal or access to sensitive paths).
79
80- Assess risk and impact:
81 - Prioritize investigation if the script targets high-value systems (for example, file servers) or if the discovery appears broad (large target lists, threading, repeated runs).
82 - If the executing `user.id` is privileged or the host is sensitive, treat the alert as higher risk and expand scoping to additional related activity.
83
84### False positive analysis
85
86- Legitimate administrative share inventory, auditing, or documentation activity performed by IT or infrastructure teams.
87- Approved operational scripts used for backup validation, migration planning, access reviews, or troubleshooting that enumerate shares across servers.
88
89### Response and remediation
90
91- If the activity is unauthorized or suspicious:
92 - Contain the affected endpoint (`host.id`) following your incident response procedures to reduce the risk of further discovery and lateral movement.
93 - Preserve evidence by retaining the complete `powershell.file.script_block_text` content and all fragments linked by `powershell.file.script_block_id` (including ordered reconstruction using `powershell.sequence` / `powershell.total` when available).
94 - Identify and prioritize potential targets referenced in the script content (servers and shares) and coordinate review of access patterns to those resources.
95 - Investigate the executing account (`user.name` / `user.id`) for compromise, including recent authentication activity and unexpected resource access, and take appropriate containment actions (credential reset, privilege review, and session invalidation where applicable).
96 - Expand hunting for additional share enumeration and subsequent access attempts associated with the same `user.id` or originating from the same `host.id`.
97 - If an on-disk script was used (`file.path` / `file.name` present), remove or quarantine the artifact per your response process and check for the same file on other systems.
98
99- If the activity is confirmed benign:
100 - Document the owner, purpose, expected timing, and expected scope (accounts and endpoints) of the share enumeration.
101 - If tuning is required, scope it narrowly to stable identifiers present in the alert (for example, specific `user.id` values and known management `host.id` endpoints) and continue to monitor for deviations from the expected pattern.
102 - Consider establishing a documented allowlist of approved share inventory scripts and their expected execution locations to reduce future triage time.
103"""
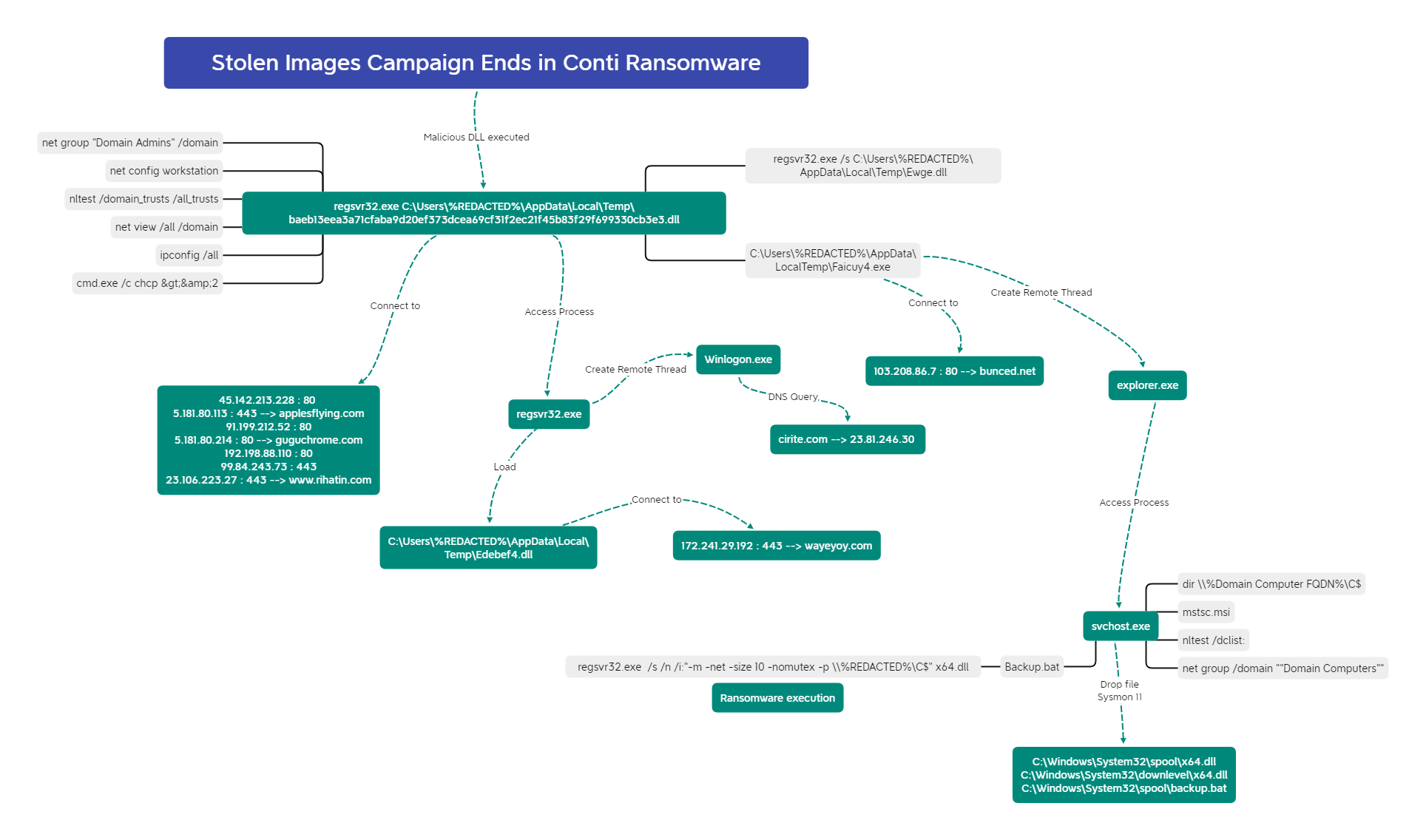
104references = [
105 "https://www.advintel.io/post/hunting-for-corporate-insurance-policies-indicators-of-ransom-exfiltrations",
106 "https://thedfirreport.com/2022/04/04/stolen-images-campaign-ends-in-conti-ransomware/",
107 "https://github.com/atc-project/atc-data/blob/master/docs/Logging_Policies/LP_0109_windows_powershell_script_block_log.md",
108]
109risk_score = 73
110rule_id = "4c59cff1-b78a-41b8-a9f1-4231984d1fb6"
111setup = """## Setup
112
113PowerShell Script Block Logging must be enabled to generate the events used by this rule (e.g., 4104).
114Setup instructions: https://ela.st/powershell-logging-setup
115"""
116severity = "high"
117tags = [
118 "Domain: Endpoint",
119 "OS: Windows",
120 "Use Case: Threat Detection",
121 "Tactic: Discovery",
122 "Tactic: Collection",
123 "Tactic: Execution",
124 "Resources: Investigation Guide",
125 "Data Source: PowerShell Logs",
126]
127timestamp_override = "event.ingested"
128type = "query"
129
130query = '''
131event.category:process and host.os.type:windows and
132 powershell.file.script_block_text:(
133 "Invoke-ShareFinder" or
134 "Invoke-ShareFinderThreaded" or
135 (
136 "shi1_netname" and
137 "shi1_remark"
138 ) or
139 (
140 "NetShareEnum" and
141 "NetApiBufferFree"
142 )
143 ) and not user.id : "S-1-5-18"
144'''
145
146
147[[rule.threat]]
148framework = "MITRE ATT&CK"
149[[rule.threat.technique]]
150id = "T1135"
151name = "Network Share Discovery"
152reference = "https://attack.mitre.org/techniques/T1135/"
153
154
155[rule.threat.tactic]
156id = "TA0007"
157name = "Discovery"
158reference = "https://attack.mitre.org/tactics/TA0007/"
159[[rule.threat]]
160framework = "MITRE ATT&CK"
161[[rule.threat.technique]]
162id = "T1059"
163name = "Command and Scripting Interpreter"
164reference = "https://attack.mitre.org/techniques/T1059/"
165[[rule.threat.technique.subtechnique]]
166id = "T1059.001"
167name = "PowerShell"
168reference = "https://attack.mitre.org/techniques/T1059/001/"
169
170
171[[rule.threat.technique]]
172id = "T1106"
173name = "Native API"
174reference = "https://attack.mitre.org/techniques/T1106/"
175
176
177[rule.threat.tactic]
178id = "TA0002"
179name = "Execution"
180reference = "https://attack.mitre.org/tactics/TA0002/"
181[[rule.threat]]
182framework = "MITRE ATT&CK"
183[[rule.threat.technique]]
184id = "T1039"
185name = "Data from Network Shared Drive"
186reference = "https://attack.mitre.org/techniques/T1039/"
187
188
189[rule.threat.tactic]
190id = "TA0009"
191name = "Collection"
192reference = "https://attack.mitre.org/tactics/TA0009/"
193
194[rule.investigation_fields]
195field_names = [
196 "@timestamp",
197 "user.name",
198 "user.id",
199 "user.domain",
200 "powershell.file.script_block_text",
201 "powershell.file.script_block_id",
202 "powershell.sequence",
203 "powershell.total",
204 "file.path",
205 "file.directory",
206 "file.name",
207 "process.pid",
208 "host.name",
209 "host.id",
210 "powershell.file.script_block_length"
211]
Triage and analysis
Disclaimer: This guide was created by humans with the assistance of generative AI. While its contents have been manually curated to include the most valuable information, always validate assumptions and adjust procedures to match your internal runbooks and incident triage and response policies.
Investigating PowerShell Share Enumeration Script
This alert indicates PowerShell script block content consistent with Windows network share enumeration. The matched text includes ShareFinder functions (for example, Invoke-ShareFinder or Invoke-ShareFinderThreaded) and/or native share enumeration API references (for example, NetShareEnum / NetApiBufferFree and shi1_netname / shi1_remark). Share discovery can be a normal administrative activity, but in attacks it is frequently used to map accessible shares prior to data collection, lateral movement, or impact activity.
Key alert fields to review
user.name,user.domain,user.id: Account execution context for correlation, prioritization, and scoping.host.name,host.id: Host execution context for correlation, prioritization, and scoping.powershell.file.script_block_text: Script block content that matched the detection logic.powershell.file.script_block_id,powershell.sequence,powershell.total: Script block metadata to pivot to other fragments or reconstruct full script content when split across multiple events.file.path,file.directory,file.name: File-origin context when the script block is sourced from an on-disk file.powershell.file.script_block_length: Script block length (size) context.
Possible investigation steps
-
Establish context and triage priority:
- Use
@timestampas the activity anchor and note the executinguser.name/user.domain/user.idand affectedhost.name/host.id. - Determine whether the account and host are expected to perform share inventory (for example, administrative workstation or management server vs. a standard user endpoint).
- Check whether similar share enumeration activity has occurred recently for the same
user.idor on the samehost.idto identify repeated scanning or automation.
- Use
-
Review the script block content and classify the activity:
- Inspect
powershell.file.script_block_textand capture relevant excerpts for the case record (function names, API calls, and any referenced hosts/shares). - Differentiate between a function definition/import and an actual invocation:
- Function definition or module load (lower confidence): the text contains the function name as part of a definition or import logic.
- Function invocation (higher confidence): the text shows parameters, target lists, or loops that initiate enumeration.
- Identify which pattern is present and what it implies about scope:
Invoke-ShareFinder: share discovery logic implemented in PowerShell.Invoke-ShareFinderThreaded: broader or faster discovery due to concurrent enumeration.NetShareEnum/NetApiBufferFreewithshi1_netname/shi1_remark: direct use of Windows share enumeration APIs and may reflect customized scripting.
- Extract scoping and intent details from the text when available:
- Target hostnames/IPs, server lists, domain-related identifiers, or UNC paths.
- Filters for share names and remarks, or include/exclude logic that focuses discovery on specific systems or shares.
- Use of alternate credentials or explicit authentication material embedded in the script (if present).
- Any output handling (formatting, writing results to disk, or staging).
- Inspect
-
Reconstruct full content when script blocks are split:
- Pivot on
powershell.file.script_block_idto collect all related fragments for the same execution context. - Use
powershell.sequenceandpowershell.totalto order fragments and identify missing pieces (if populated). - Review adjacent script blocks for the same
host.idanduser.idnear@timestampto capture supporting functions or follow-on actions that may not appear in the triggering fragment.
- Pivot on
-
Determine whether the activity originated from an on-disk script:
- If present, use
file.path/file.directory/file.nameto identify the script source. - Assess whether the script location and name align with approved administrative tooling. Scripts originating from user-writable or temporary locations are higher risk than centrally managed locations.
- If an on-disk script is involved, preserve the file for further analysis and determine whether it appears on additional hosts (pivot on
file.namewhere applicable).
- If present, use
-
Scope across users and hosts:
- Look for additional events containing the same discovery keywords in
powershell.file.script_block_textto identify other affected endpoints. - Check whether the same
user.idperformed similar activity from multiplehost.idvalues in a short period, which can indicate automation or credential misuse. - Identify whether multiple users are performing similar enumeration from the same host, which can indicate a shared jump box or a compromised administrative endpoint.
- Look for additional events containing the same discovery keywords in
-
Correlate with adjacent telemetry (as available) to confirm intent and detect follow-on behavior:
- Process execution telemetry on the same
host.idaround@timestampto determine how PowerShell was launched and whether the initiating process and execution pattern are consistent with expected activity foruser.id. - Network telemetry around
@timestampfor access to multiple remote hosts consistent with share enumeration and subsequent SMB activity. - Authentication telemetry for
user.idaround@timestampfor unusual access to file servers or multiple servers, especially if the behavior is new for the account. - File activity telemetry (endpoint and/or file server) for unusual access patterns to shared locations following the enumeration (for example, rapid directory traversal or access to sensitive paths).
- Process execution telemetry on the same
-
Assess risk and impact:
- Prioritize investigation if the script targets high-value systems (for example, file servers) or if the discovery appears broad (large target lists, threading, repeated runs).
- If the executing
user.idis privileged or the host is sensitive, treat the alert as higher risk and expand scoping to additional related activity.
False positive analysis
- Legitimate administrative share inventory, auditing, or documentation activity performed by IT or infrastructure teams.
- Approved operational scripts used for backup validation, migration planning, access reviews, or troubleshooting that enumerate shares across servers.
Response and remediation
-
If the activity is unauthorized or suspicious:
- Contain the affected endpoint (
host.id) following your incident response procedures to reduce the risk of further discovery and lateral movement. - Preserve evidence by retaining the complete
powershell.file.script_block_textcontent and all fragments linked bypowershell.file.script_block_id(including ordered reconstruction usingpowershell.sequence/powershell.totalwhen available). - Identify and prioritize potential targets referenced in the script content (servers and shares) and coordinate review of access patterns to those resources.
- Investigate the executing account (
user.name/user.id) for compromise, including recent authentication activity and unexpected resource access, and take appropriate containment actions (credential reset, privilege review, and session invalidation where applicable). - Expand hunting for additional share enumeration and subsequent access attempts associated with the same
user.idor originating from the samehost.id. - If an on-disk script was used (
file.path/file.namepresent), remove or quarantine the artifact per your response process and check for the same file on other systems.
- Contain the affected endpoint (
-
If the activity is confirmed benign:
- Document the owner, purpose, expected timing, and expected scope (accounts and endpoints) of the share enumeration.
- If tuning is required, scope it narrowly to stable identifiers present in the alert (for example, specific
user.idvalues and known managementhost.idendpoints) and continue to monitor for deviations from the expected pattern. - Consider establishing a documented allowlist of approved share inventory scripts and their expected execution locations to reduce future triage time.
References
Related rules
- PowerShell Suspicious Discovery Related Windows API Functions
- Potential PowerShell HackTool Script by Author
- Potential Process Injection via PowerShell
- Suspicious .NET Reflection via PowerShell
- PowerShell Script with Webcam Video Capture Capabilities