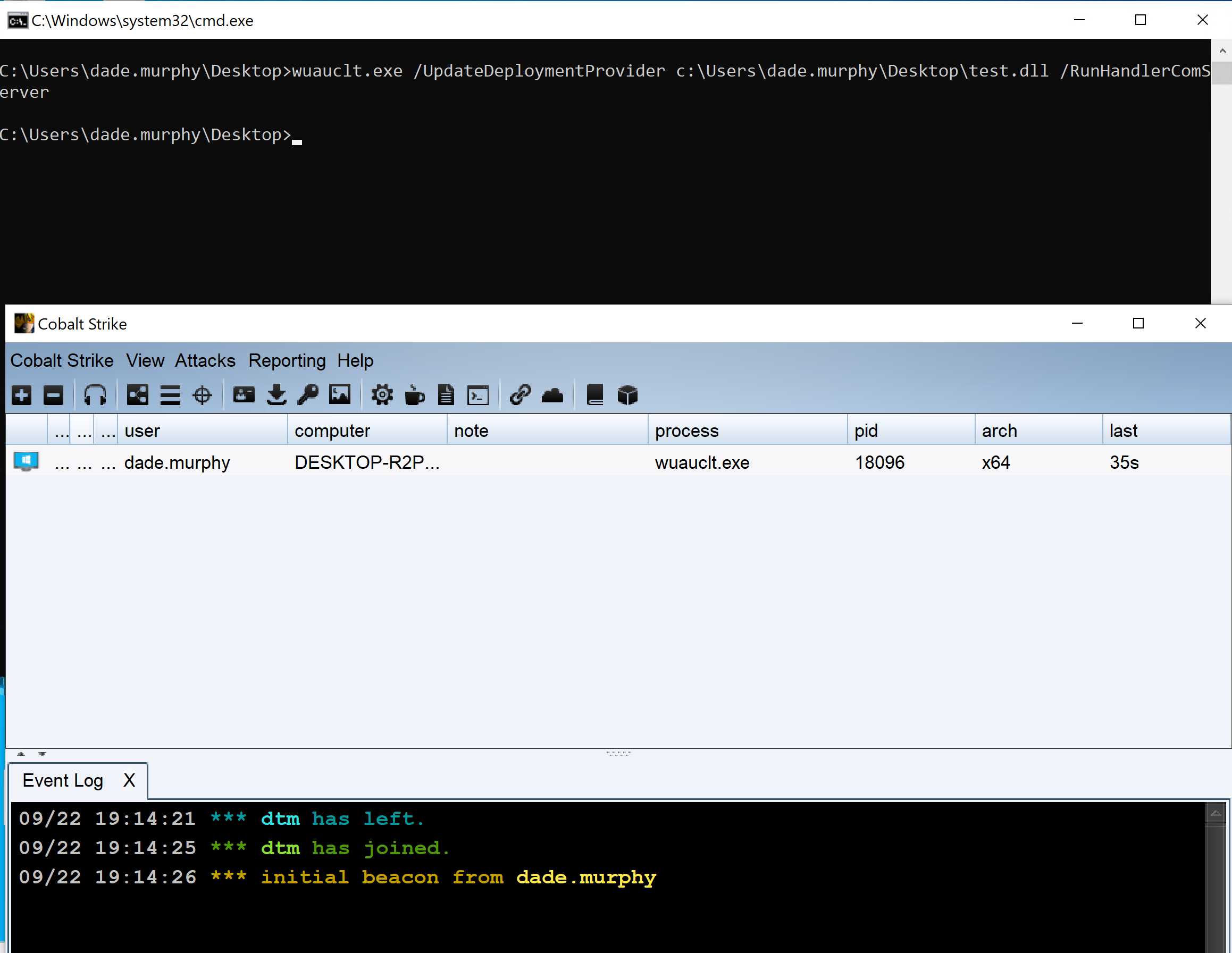
ImageLoad via Windows Update Auto Update Client
Identifies abuse of the Windows Update Auto Update Client (wuauclt.exe) to load an arbitrary DLL. This behavior is used as a defense evasion technique to blend-in malicious activity with legitimate Windows software.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2020/10/13"
3integration = ["endpoint", "windows", "system"]
4maturity = "production"
5updated_date = "2024/05/21"
6
7[transform]
8[[transform.osquery]]
9label = "Osquery - Retrieve DNS Cache"
10query = "SELECT * FROM dns_cache"
11
12[[transform.osquery]]
13label = "Osquery - Retrieve All Services"
14query = "SELECT description, display_name, name, path, pid, service_type, start_type, status, user_account FROM services"
15
16[[transform.osquery]]
17label = "Osquery - Retrieve Services Running on User Accounts"
18query = """
19SELECT description, display_name, name, path, pid, service_type, start_type, status, user_account FROM services WHERE
20NOT (user_account LIKE '%LocalSystem' OR user_account LIKE '%LocalService' OR user_account LIKE '%NetworkService' OR
21user_account == null)
22"""
23
24[[transform.osquery]]
25label = "Osquery - Retrieve Service Unsigned Executables with Virustotal Link"
26query = """
27SELECT concat('https://www.virustotal.com/gui/file/', sha1) AS VtLink, name, description, start_type, status, pid,
28services.path FROM services JOIN authenticode ON services.path = authenticode.path OR services.module_path =
29authenticode.path JOIN hash ON services.path = hash.path WHERE authenticode.result != 'trusted'
30"""
31
32
33[rule]
34author = ["Elastic"]
35description = """
36Identifies abuse of the Windows Update Auto Update Client (wuauclt.exe) to load an arbitrary DLL. This behavior is used
37as a defense evasion technique to blend-in malicious activity with legitimate Windows software.
38"""
39from = "now-9m"
40index = [
41 "logs-endpoint.events.process-*",
42 "winlogbeat-*",
43 "logs-windows.*",
44 "endgame-*",
45 "logs-system.security*",
46]
47language = "eql"
48license = "Elastic License v2"
49name = "ImageLoad via Windows Update Auto Update Client"
50note = """## Triage and analysis
51
52### Investigating ImageLoad via Windows Update Auto Update Client
53
54The Windows Update Auto Update Client (wuauclt.exe) is the component responsible for managing system updates. However, adversaries may abuse this process to load a malicious DLL and execute malicious code while blending into a legitimate system mechanism.
55
56This rule identifies potential abuse for code execution by monitoring for specific process arguments ("/RunHandlerComServer" and "/UpdateDeploymentProvider") and common writable paths where the target DLL can be placed (e.g., "C:\\Users\\*.dll", "C:\\ProgramData\\*.dll", etc.).
57
58> **Note**:
59> This investigation guide uses the [Osquery Markdown Plugin](https://www.elastic.co/guide/en/security/master/invest-guide-run-osquery.html) introduced in Elastic Stack version 8.5.0. Older Elastic Stack versions will display unrendered Markdown in this guide.
60
61### Possible investigation steps
62
63- Investigate the process execution chain (parent process tree) for unknown processes. Examine their executable files for prevalence, whether they are located in expected locations, and if they are signed with valid digital signatures.
64- Investigate any abnormal behavior by the subject process, such as network connections, registry or file modifications, and any spawned child processes.
65- Examine the command line and identify the DLL location.
66- Examine whether the DLL is signed.
67- Retrieve the DLL and determine if it is malicious:
68 - Analyze the file using a private sandboxed analysis system.
69 - Observe and collect information about the following activities in both the sandbox and the alert subject host:
70 - Attempts to contact external domains and addresses.
71 - Use the Elastic Defend network events to determine domains and addresses contacted by the subject process by filtering by the process' `process.entity_id`.
72 - Examine the DNS cache for suspicious or anomalous entries.
73 - $osquery_0
74 - Use the Elastic Defend registry events to examine registry keys accessed, modified, or created by the related processes in the process tree.
75 - Examine the host services for suspicious or anomalous entries.
76 - $osquery_1
77 - $osquery_2
78 - $osquery_3
79 - Retrieve the files' SHA-256 hash values using the PowerShell `Get-FileHash` cmdlet and search for the existence and reputation of the hashes in resources like VirusTotal, Hybrid-Analysis, CISCO Talos, Any.run, etc.
80- Investigate the behavior of child processes, such as network connections, registry or file modifications, and any spawned processes.
81
82### False positive analysis
83
84- This activity is unlikely to happen legitimately. Any activity that triggered the alert and is not inherently malicious must be monitored by the security team.
85
86### Response and Remediation
87
88- Initiate the incident response process based on the outcome of the triage.
89- Isolate the involved host to prevent further post-compromise behavior.
90- If the triage identified malware, search the environment for additional compromised hosts.
91 - Implement temporary network rules, procedures, and segmentation to contain the malware.
92 - Stop suspicious processes.
93 - Immediately block the identified indicators of compromise (IoCs).
94 - Inspect the affected systems for additional malware backdoors like reverse shells, reverse proxies, or droppers that attackers could use to reinfect the system.
95- Remove and block malicious artifacts identified during triage.
96- Run a full antimalware scan. This may reveal additional artifacts left in the system, persistence mechanisms, and malware components.
97- Investigate credential exposure on systems compromised or used by the attacker to ensure all compromised accounts are identified. Reset passwords for these accounts and other potentially compromised credentials, such as email, business systems, and web services.
98- Determine the initial vector abused by the attacker and take action to prevent reinfection through the same vector.
99- Using the incident response data, update logging and audit policies to improve the mean time to detect (MTTD) and the mean time to respond (MTTR).
100"""
101references = ["https://dtm.uk/wuauclt/"]
102risk_score = 47
103rule_id = "edf8ee23-5ea7-4123-ba19-56b41e424ae3"
104setup = """## Setup
105
106If enabling an EQL rule on a non-elastic-agent index (such as beats) for versions <8.2,
107events will not define `event.ingested` and default fallback for EQL rules was not added until version 8.2.
108Hence for this rule to work effectively, users will need to add a custom ingest pipeline to populate
109`event.ingested` to @timestamp.
110For more details on adding a custom ingest pipeline refer - https://www.elastic.co/guide/en/fleet/current/data-streams-pipeline-tutorial.html
111"""
112severity = "medium"
113tags = [
114 "Domain: Endpoint",
115 "OS: Windows",
116 "Use Case: Threat Detection",
117 "Tactic: Defense Evasion",
118 "Tactic: Execution",
119 "Data Source: Elastic Endgame",
120 "Data Source: Elastic Defend",
121]
122timeline_id = "e70679c2-6cde-4510-9764-4823df18f7db"
123timeline_title = "Comprehensive Process Timeline"
124timestamp_override = "event.ingested"
125type = "eql"
126
127query = '''
128process where host.os.type == "windows" and event.type == "start" and
129 (?process.pe.original_file_name == "wuauclt.exe" or process.name : "wuauclt.exe") and
130 /* necessary windows update client args to load a dll */
131 process.args : "/RunHandlerComServer" and process.args : "/UpdateDeploymentProvider" and
132 /* common paths writeable by a standard user where the target DLL can be placed */
133 process.args : ("C:\\Users\\*.dll", "C:\\ProgramData\\*.dll", "C:\\Windows\\Temp\\*.dll", "C:\\Windows\\Tasks\\*.dll")
134'''
135
136
137[[rule.threat]]
138framework = "MITRE ATT&CK"
139[[rule.threat.technique]]
140id = "T1218"
141name = "System Binary Proxy Execution"
142reference = "https://attack.mitre.org/techniques/T1218/"
143
144
145[rule.threat.tactic]
146id = "TA0005"
147name = "Defense Evasion"
148reference = "https://attack.mitre.org/tactics/TA0005/"
Triage and analysis
Investigating ImageLoad via Windows Update Auto Update Client
The Windows Update Auto Update Client (wuauclt.exe) is the component responsible for managing system updates. However, adversaries may abuse this process to load a malicious DLL and execute malicious code while blending into a legitimate system mechanism.
This rule identifies potential abuse for code execution by monitoring for specific process arguments ("/RunHandlerComServer" and "/UpdateDeploymentProvider") and common writable paths where the target DLL can be placed (e.g., "C:\Users*.dll", "C:\ProgramData*.dll", etc.).
Note: This investigation guide uses the Osquery Markdown Plugin introduced in Elastic Stack version 8.5.0. Older Elastic Stack versions will display unrendered Markdown in this guide.
Possible investigation steps
- Investigate the process execution chain (parent process tree) for unknown processes. Examine their executable files for prevalence, whether they are located in expected locations, and if they are signed with valid digital signatures.
- Investigate any abnormal behavior by the subject process, such as network connections, registry or file modifications, and any spawned child processes.
- Examine the command line and identify the DLL location.
- Examine whether the DLL is signed.
- Retrieve the DLL and determine if it is malicious:
- Analyze the file using a private sandboxed analysis system.
- Observe and collect information about the following activities in both the sandbox and the alert subject host:
- Attempts to contact external domains and addresses.
- Use the Elastic Defend network events to determine domains and addresses contacted by the subject process by filtering by the process'
process.entity_id. - Examine the DNS cache for suspicious or anomalous entries.
- $osquery_0
- Use the Elastic Defend network events to determine domains and addresses contacted by the subject process by filtering by the process'
- Use the Elastic Defend registry events to examine registry keys accessed, modified, or created by the related processes in the process tree.
- Examine the host services for suspicious or anomalous entries.
- $osquery_1
- $osquery_2
- $osquery_3
- Attempts to contact external domains and addresses.
- Retrieve the files' SHA-256 hash values using the PowerShell
Get-FileHashcmdlet and search for the existence and reputation of the hashes in resources like VirusTotal, Hybrid-Analysis, CISCO Talos, Any.run, etc.
- Investigate the behavior of child processes, such as network connections, registry or file modifications, and any spawned processes.
False positive analysis
- This activity is unlikely to happen legitimately. Any activity that triggered the alert and is not inherently malicious must be monitored by the security team.
Response and Remediation
- Initiate the incident response process based on the outcome of the triage.
- Isolate the involved host to prevent further post-compromise behavior.
- If the triage identified malware, search the environment for additional compromised hosts.
- Implement temporary network rules, procedures, and segmentation to contain the malware.
- Stop suspicious processes.
- Immediately block the identified indicators of compromise (IoCs).
- Inspect the affected systems for additional malware backdoors like reverse shells, reverse proxies, or droppers that attackers could use to reinfect the system.
- Remove and block malicious artifacts identified during triage.
- Run a full antimalware scan. This may reveal additional artifacts left in the system, persistence mechanisms, and malware components.
- Investigate credential exposure on systems compromised or used by the attacker to ensure all compromised accounts are identified. Reset passwords for these accounts and other potentially compromised credentials, such as email, business systems, and web services.
- Determine the initial vector abused by the attacker and take action to prevent reinfection through the same vector.
- Using the incident response data, update logging and audit policies to improve the mean time to detect (MTTD) and the mean time to respond (MTTR).
References
Related rules
- Clearing Windows Console History
- Command Shell Activity Started via RunDLL32
- Conhost Spawned By Suspicious Parent Process
- Control Panel Process with Unusual Arguments
- Disabling Windows Defender Security Settings via PowerShell