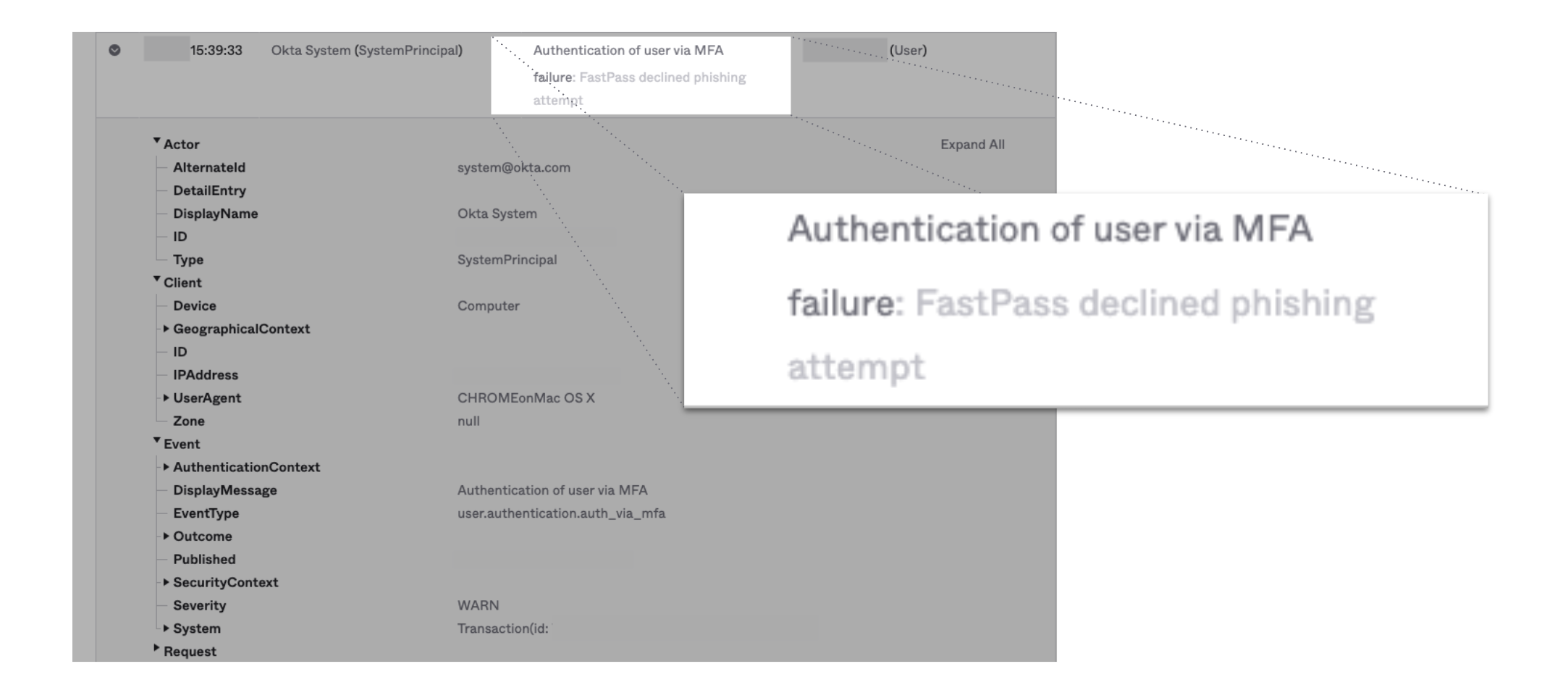
Okta FastPass Phishing Detection
Detects when Okta FastPass prevents a user from authenticating to a phishing website.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2023/05/07"
3integration = ["okta"]
4maturity = "production"
5min_stack_comments = "Breaking change in Okta integration bumping version to ^2.0.0"
6min_stack_version = "8.10.0"
7updated_date = "2023/11/07"
8
9[rule]
10author = ["Austin Songer"]
11description = """
12Detects when Okta FastPass prevents a user from authenticating to a phishing website.
13"""
14
15index = ["filebeat-*", "logs-okta*"]
16language = "kuery"
17license = "Elastic License v2"
18name = "Okta FastPass Phishing Detection"
19note = """## Setup
20
21The Okta Fleet integration, Filebeat module, or similarly structured data is required to be compatible with this rule.
22
23This rule requires Okta to have the following turned on:
24
25Okta Identity Engine - select 'Phishing Resistance for FastPass' under Settings > Features in the Admin Console.
26"""
27references = [
28 "https://developer.okta.com/docs/reference/api/system-log/",
29 "https://developer.okta.com/docs/reference/api/event-types/",
30 "https://sec.okta.com/fastpassphishingdetection",
31 "https://sec.okta.com/articles/2023/08/cross-tenant-impersonation-prevention-and-detection"
32]
33risk_score = 47
34rule_id = "ee39a9f7-5a79-4b0a-9815-d36b3cf28d3e"
35severity = "medium"
36tags = ["Tactic: Initial Access", "Use Case: Identity and Access Audit", "Data Source: Okta"]
37timestamp_override = "event.ingested"
38type = "query"
39
40query = '''
41event.dataset:okta.system and event.category:authentication and
42 okta.event_type:user.authentication.auth_via_mfa and event.outcome:failure and okta.outcome.reason:"FastPass declined phishing attempt"
43'''
44
45
46[[rule.threat]]
47framework = "MITRE ATT&CK"
48[[rule.threat.technique]]
49id = "T1566"
50name = "Phishing"
51reference = "https://attack.mitre.org/techniques/T1566/"
52
53
54[rule.threat.tactic]
55id = "TA0001"
56name = "Initial Access"
57reference = "https://attack.mitre.org/tactics/TA0001/"
Setup
The Okta Fleet integration, Filebeat module, or similarly structured data is required to be compatible with this rule.
This rule requires Okta to have the following turned on:
Okta Identity Engine - select 'Phishing Resistance for FastPass' under Settings > Features in the Admin Console.
References
Related rules
- Multiple Okta Client Addresses for a Single User Session
- Okta Sign-In Events via Third-Party IdP
- First Occurrence of Okta User Session Started via Proxy
- New Okta Authentication Behavior Detected
- Okta User Sessions Started from Different Geolocations