Potential Persistence via Cron Job
Identifies the creation or execution of a cron job. Adversaries may abuse cron jobs to perform task scheduling for initial or recurring execution of malicious code.
Elastic rule (View on GitHub)
1[metadata]
2creation_date = "2021/01/15"
3deprecation_date = "2021/04/15"
4maturity = "deprecated"
5updated_date = "2021/04/15"
6
7[rule]
8author = ["Elastic"]
9description = """
10Identifies the creation or execution of a cron job. Adversaries may abuse cron jobs to perform task scheduling for
11initial or recurring execution of malicious code.
12"""
13false_positives = ["Legitimate software or scripts using cron jobs for recurring tasks."]
14from = "now-9m"
15index = ["auditbeat-*", "logs-endpoint.events.*"]
16language = "kuery"
17license = "Elastic License v2"
18name = "Potential Persistence via Cron Job"
19references = ["https://archive.f-secure.com/weblog/archives/00002576.html", "https://ss64.com/osx/crontab.html"]
20risk_score = 21
21rule_id = "b1c14366-f4f8-49a0-bcbb-51d2de8b0bb8"
22severity = "low"
23tags = ["Elastic", "Host", "Linux", "macOS", "Threat Detection", "Persistence"]
24timestamp_override = "event.ingested"
25type = "query"
26
27query = '''
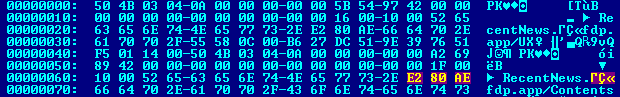
28event.category:process and event.type:(start or process_started or info) and
29 not user.name:root and
30 ((process.name:crontab and not process.args:("-l" or "-r" or "-e" or "-help" or "-h")) or
31 (process.parent.name:cron and not process.name:"running job" and
32 not process.executable:(/Applications/Docker.app/Contents/Resources/bin/docker or
33 /usr/bin/killall or
34 /usr/sbin/sendmail or
35 /usr/bin/env or
36 /usr/bin/timeshift or
37 /bin/rm)))
38'''
39
40
41[[rule.threat]]
42framework = "MITRE ATT&CK"
43[[rule.threat.technique]]
44id = "T1053"
45name = "Scheduled Task/Job"
46reference = "https://attack.mitre.org/techniques/T1053/"
47[[rule.threat.technique.subtechnique]]
48id = "T1053.003"
49name = "Cron"
50reference = "https://attack.mitre.org/techniques/T1053/003/"
51
52
53
54[rule.threat.tactic]
55id = "TA0003"
56name = "Persistence"
57reference = "https://attack.mitre.org/tactics/TA0003/"
References
Related rules
- Persistence via Kernel Module Modification
- Base64 Encoding/Decoding Activity
- Hex Encoding/Decoding Activity
- Mknod Process Activity
- Network Sniffing via Tcpdump