Hiding local user accounts
Detects the use reg.exe to hide users from listed in the logon screen. This is possible by changing the registry key value to 0 for a specific user.
Sigma rule (View on GitHub)
1title: Hiding local user accounts
2id: 59e3a079-4245-4203-9d5c-f11290c5ba24
3description: Detects the use reg.exe to hide users from listed in the logon screen. This is possible by changing the registry key value to 0 for a specific user.
4status: experimental
5references:
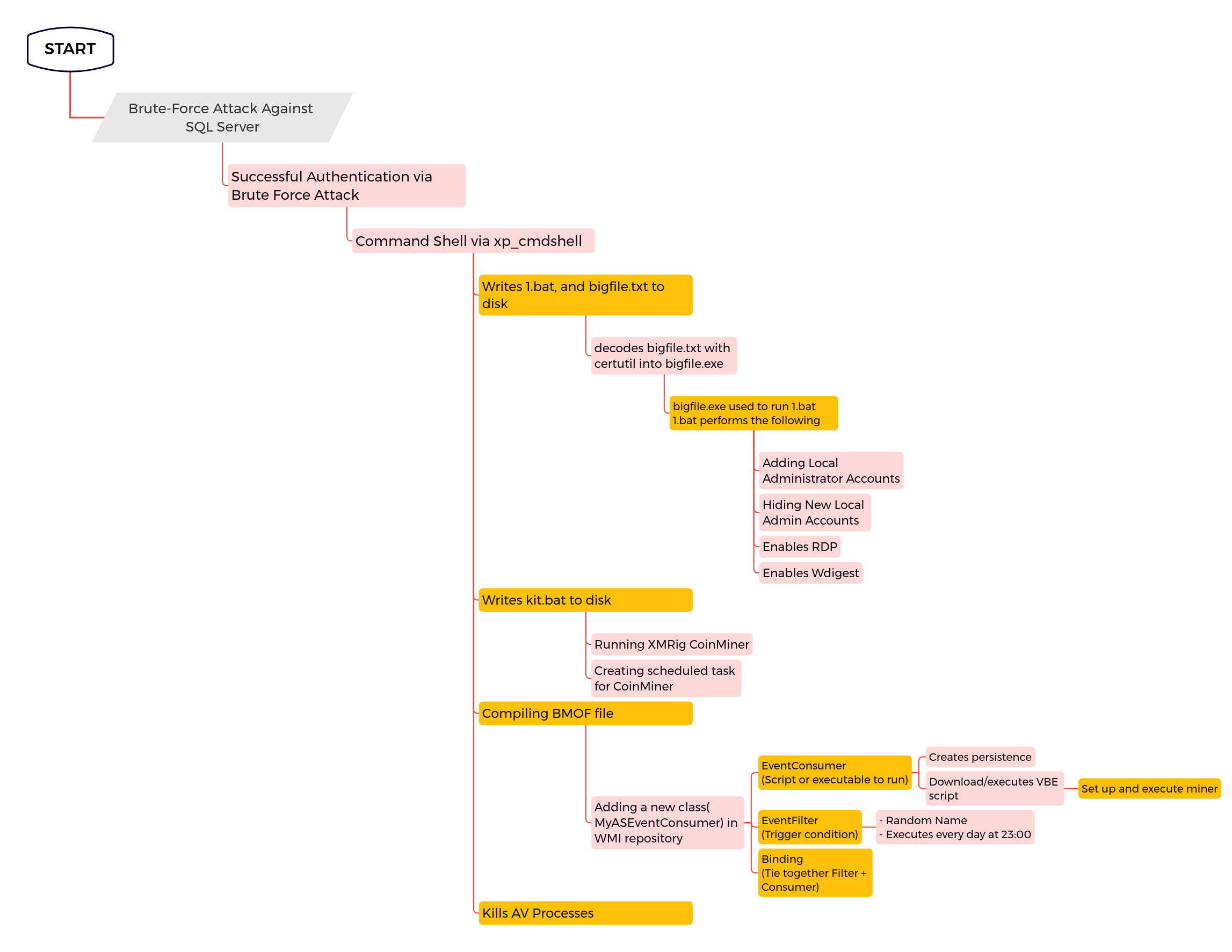
6 - https://thedfirreport.com/2022/07/11/select-xmrig-from-sqlserver/
7author: 'Kostastsale, TheDFIRReport'
8date: 2022-07-11
9modified: 2024-02-23
10logsource:
11 category: process_creation
12 product: windows
13detection:
14 selection1:
15 ParentImage|endswith:
16 - '\cmd.exe'
17 - '\powershell.exe'
18 Image|endswith:
19 - '\reg.exe'
20 CommandLine|contains|all:
21 - 'HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\Userlist'
22 - 'add'
23 - '/t'
24 - 'REG_DWORD'
25 - '/v'
26 - '/d 0'
27 condition: selection1
28falsepositives:
29 - System administrator activities
30level: medium
31tags:
32 - attack.t1564.002
33 - attack.defense_evasion
yaml
References
Related rules
- Custom Cobalt Strike Command Execution
- Deleting Windows Defender scheduled tasks
- FlawedGrace spawning threat injection target
- Enable WDigest using PowerShell
- Enabling RDP service via reg.exe command execution