SplashTop Network
Detects use of SplashTop
Sigma rule (View on GitHub)
1title: SplashTop Network
2id: 53d94914-971a-4326-a3d6-b11e0d409914
3status: experimental
4description: Detects use of SplashTop
5author: _pete_0, TheDFIRReport
6references:
7 - https://support-splashtopbusiness.splashtop.com/hc/en-us/articles/212724303-Why-does-the-Splashtop-software-show-unable-to-reach-Splashtop-servers-
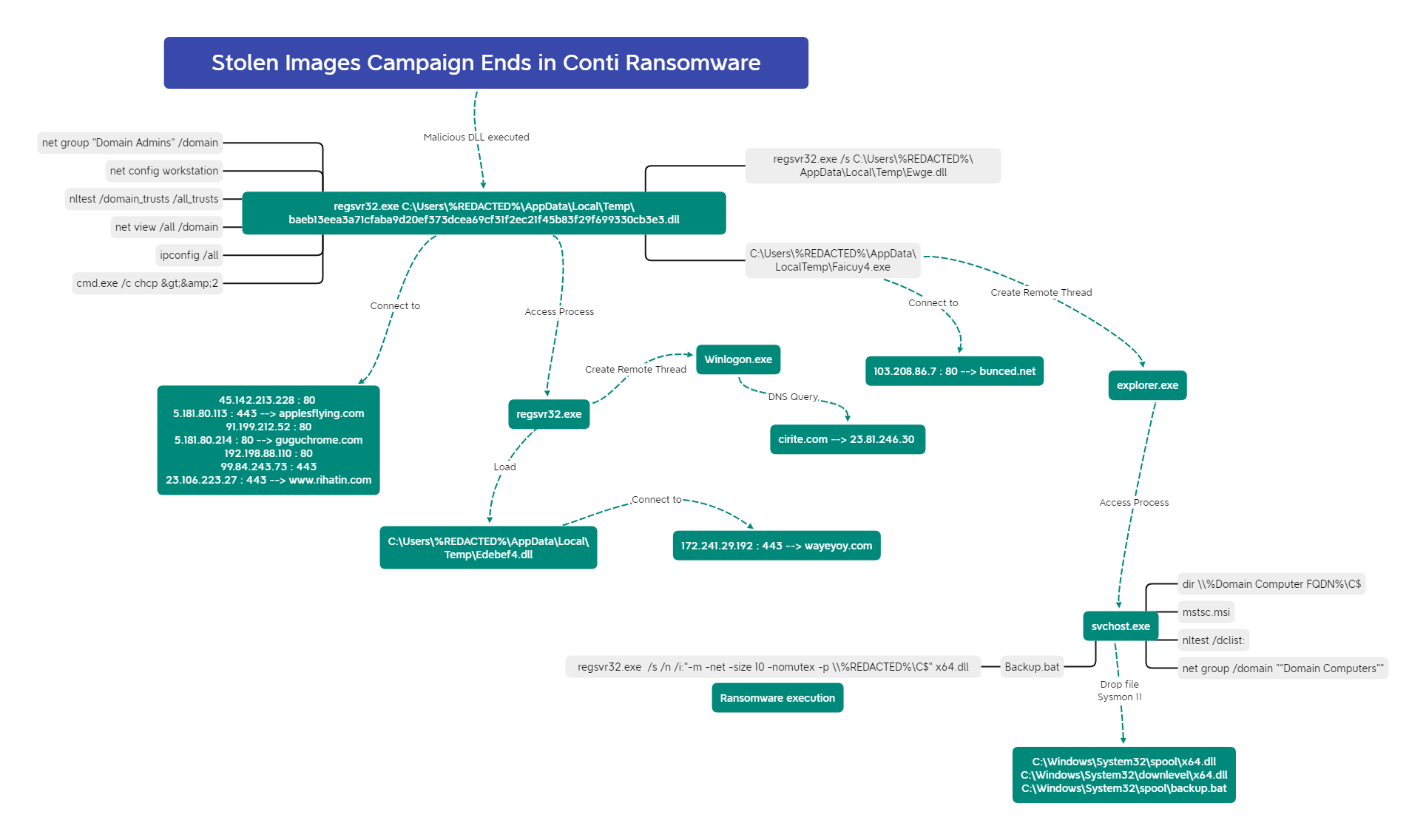
8 - https://thedfirreport.com/2022/04/04/stolen-images-campaign-ends-in-conti-ransomware/
9date: 2022-05-06
10modified: 2022-05-06
11logsource:
12 category: dns_query
13 product: windows
14detection:
15 selection:
16 QueryName|contains:
17 - '.splashtop.com'
18 - '.splashtop.eu'
19 Image|endswith:
20 - '\spupnp.exe'
21 - '\Dataproxy.exe'
22 - '\SRServer.exe'
23 - '\SRFeature.exe'
24 - '\SSUService.exe'
25 - '\strwinclt.exe'
26 condition: selection
27falsepositives:
28 - Legitimate SplashTop installation
29level: high
30tags:
31 - attack.lateral-movement
32 - attack.t1133
33 - attack.command-and-control
34 - attack.t1219
yaml
References
Related rules
- AnyDesk Network
- SplashTop Process
- Remote Access Tool - AnyDesk Execution
- Remote Access Tool - AnyDesk Incoming Connection
- Remote Access Tool - Anydesk Execution From Suspicious Folder