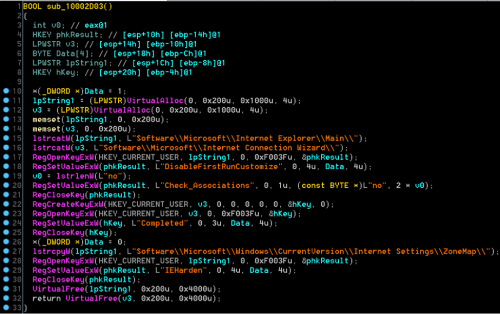
Internet Explorer DisableFirstRunCustomize Enabled
Detects changes to the Internet Explorer "DisableFirstRunCustomize" value, which prevents Internet Explorer from running the first run wizard the first time a user starts the browser after installing Internet Explorer or Windows.
Sigma rule (View on GitHub)
1title: Internet Explorer DisableFirstRunCustomize Enabled
2id: ab567429-1dfb-4674-b6d2-979fd2f9d125
3status: experimental
4description: |
5 Detects changes to the Internet Explorer "DisableFirstRunCustomize" value, which prevents Internet Explorer from running the first run wizard the first time a user starts the browser after installing Internet Explorer or Windows.
6references:
7 - https://www.ncsc.gov.uk/static-assets/documents/malware-analysis-reports/devil-bait/NCSC-MAR-Devil-Bait.pdf
8 - https://unit42.paloaltonetworks.com/operation-ke3chang-resurfaces-with-new-tidepool-malware/
9 - https://admx.help/?Category=InternetExplorer&Policy=Microsoft.Policies.InternetExplorer::NoFirstRunCustomise
10author: Nasreddine Bencherchali (Nextron Systems)
11date: 2023/05/16
12modified: 2023/08/17
13tags:
14 - attack.defense_evasion
15logsource:
16 product: windows
17 category: registry_set
18detection:
19 selection:
20 TargetObject|endswith: '\Microsoft\Internet Explorer\Main\DisableFirstRunCustomize'
21 Details:
22 - 'DWORD (0x00000001)' # Home Page
23 - 'DWORD (0x00000002)' # Welcome To IE
24 filter_main_generic:
25 Image:
26 - 'C:\Windows\explorer.exe'
27 - 'C:\Windows\System32\ie4uinit.exe'
28 condition: selection and not 1 of filter_main_*
29falsepositives:
30 - As this is controlled by group policy as well as user settings. Some false positives may occur.
31level: medium
References
Related rules
- Activate Suppression of Windows Security Center Notifications
- Add DisallowRun Execution to Registry
- Allow RDP Remote Assistance Feature
- Blackbyte Ransomware Registry
- Bypass UAC Using DelegateExecute