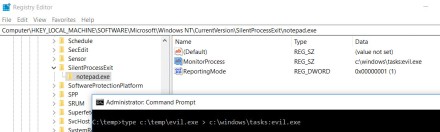
Potential Credential Dumping Via LSASS SilentProcessExit Technique
Detects changes to the Registry in which a monitor program gets registered to dump the memory of the lsass.exe process
Sigma rule (View on GitHub)
1title: Potential Credential Dumping Via LSASS SilentProcessExit Technique
2id: 55e29995-75e7-451a-bef0-6225e2f13597
3related:
4 - id: 36803969-5421-41ec-b92f-8500f79c23b0
5 type: similar
6status: test
7description: Detects changes to the Registry in which a monitor program gets registered to dump the memory of the lsass.exe process
8references:
9 - https://www.deepinstinct.com/2021/02/16/lsass-memory-dumps-are-stealthier-than-ever-before-part-2/
10 - https://oddvar.moe/2018/04/10/persistence-using-globalflags-in-image-file-execution-options-hidden-from-autoruns-exe/
11author: Florian Roth (Nextron Systems)
12date: 2021/02/26
13modified: 2022/12/19
14tags:
15 - attack.credential_access
16 - attack.t1003.001
17logsource:
18 category: registry_event
19 product: windows
20detection:
21 selection:
22 TargetObject|contains: 'Microsoft\Windows NT\CurrentVersion\SilentProcessExit\lsass.exe'
23 condition: selection
24falsepositives:
25 - Unlikely
26level: critical
References
Related rules
- Credential Dumping Tools Service Execution - System
- LSASS Process Dump Artefact In CrashDumps Folder
- Potential Credential Dumping Attempt Via PowerShell Remote Thread
- Potential Credential Dumping Via WER
- Potential Credential Dumping Via WER - Application