Renamed Visual Studio Code Tunnel Execution
Detects renamed Visual Studio Code tunnel execution. Attackers can abuse this functionality to establish a C2 channel
Sigma rule (View on GitHub)
1title: Renamed Visual Studio Code Tunnel Execution
2id: 2cf29f11-e356-4f61-98c0-1bdb9393d6da
3status: test
4description: Detects renamed Visual Studio Code tunnel execution. Attackers can abuse this functionality to establish a C2 channel
5references:
6 - https://ipfyx.fr/post/visual-studio-code-tunnel/
7 - https://badoption.eu/blog/2023/01/31/code_c2.html
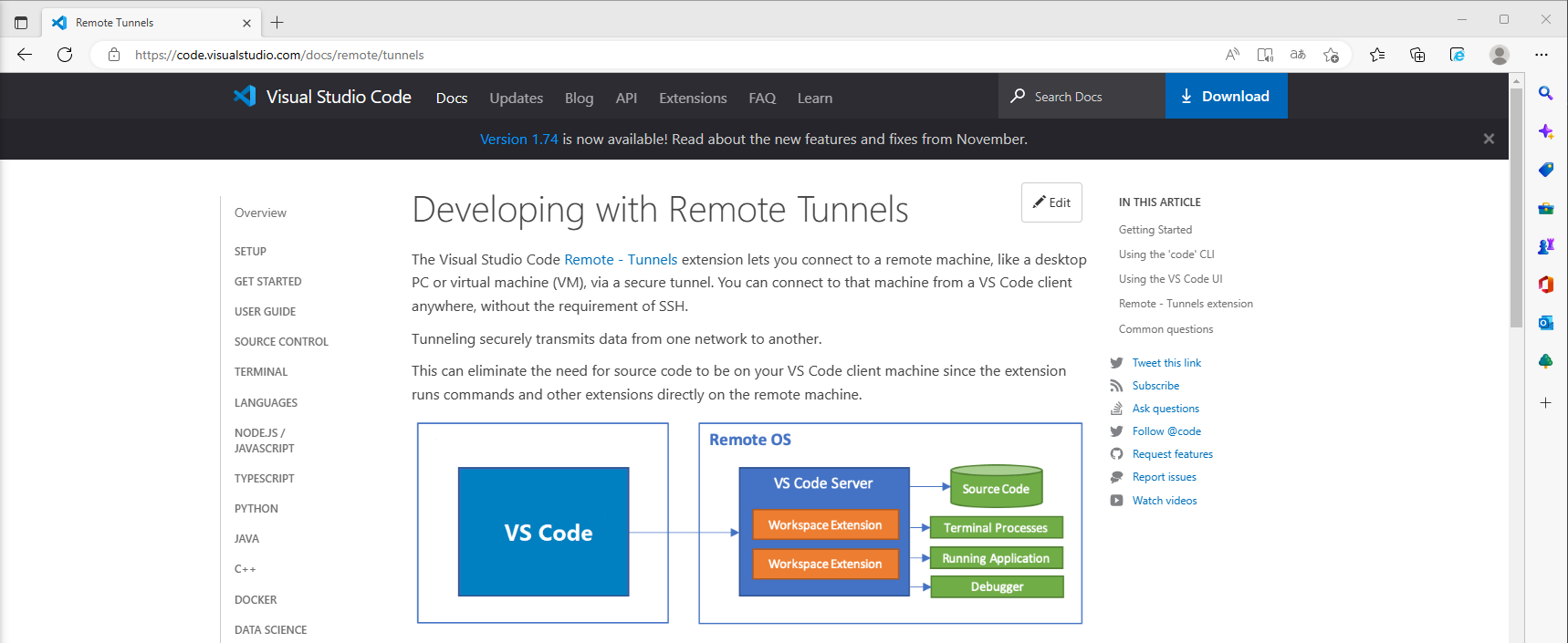
8 - https://code.visualstudio.com/docs/remote/tunnels
9author: Nasreddine Bencherchali (Nextron Systems)
10date: 2023-09-28
11modified: 2025-10-29
12tags:
13 - attack.command-and-control
14 - attack.t1071.001
15 - attack.t1219
16logsource:
17 category: process_creation
18 product: windows
19detection:
20 selection_image_only_tunnel:
21 OriginalFileName: null
22 CommandLine|endswith: '.exe tunnel'
23 selection_image_tunnel_args:
24 CommandLine|contains|all:
25 - '.exe tunnel'
26 - '--accept-server-license-terms'
27 selection_image_tunnel_service:
28 CommandLine|contains|all:
29 - 'tunnel '
30 - 'service'
31 - 'internal-run'
32 - 'tunnel-service.log'
33 selection_parent_tunnel:
34 ParentCommandLine|endswith: ' tunnel'
35 Image|endswith: '\cmd.exe'
36 CommandLine|contains|all:
37 - '/d /c '
38 - '\servers\Stable-'
39 - 'code-server.cmd'
40 filter_main_parent_code:
41 ParentImage|endswith:
42 - '\code-tunnel.exe'
43 - '\code.exe'
44 filter_main_image_code:
45 Image|endswith:
46 - '\code-tunnel.exe'
47 - '\code.exe'
48 condition: (1 of selection_image_* and not 1 of filter_main_image_*) or (selection_parent_tunnel and not 1 of filter_main_parent_*)
49falsepositives:
50 - Unknown
51level: high
References
Related rules
- Visual Studio Code Tunnel Execution
- Cloudflared Tunnels Related DNS Requests
- DNS Query To Devtunnels Domain
- Change User Agents with WebRequest
- APT40 Dropbox Tool User Agent