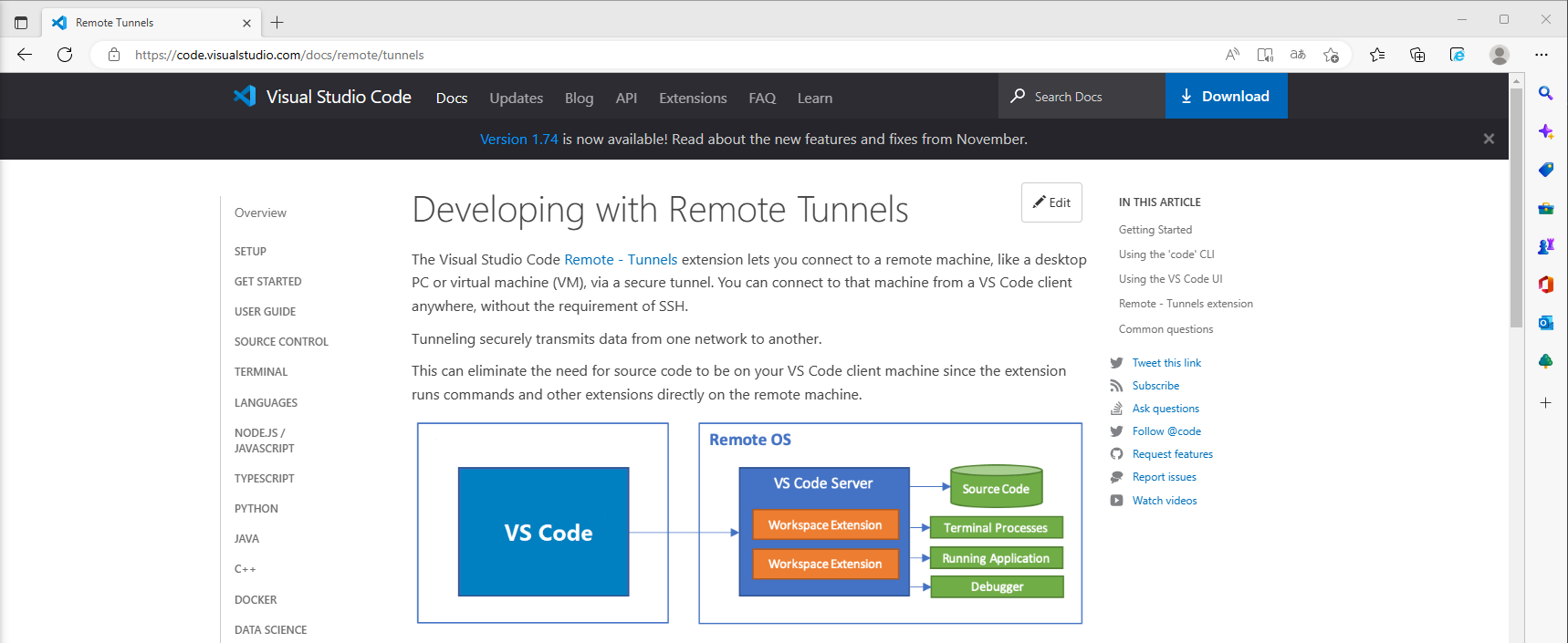
Visual Studio Code Tunnel Shell Execution
Detects the execution of a shell (powershell, bash, wsl...) via Visual Studio Code tunnel. Attackers can abuse this functionality to establish a C2 channel and execute arbitrary commands on the system.
Sigma rule (View on GitHub)
1title: Visual Studio Code Tunnel Shell Execution
2id: f4a623c2-4ef5-4c33-b811-0642f702c9f1
3status: test
4description: Detects the execution of a shell (powershell, bash, wsl...) via Visual Studio Code tunnel. Attackers can abuse this functionality to establish a C2 channel and execute arbitrary commands on the system.
5references:
6 - https://ipfyx.fr/post/visual-studio-code-tunnel/
7 - https://badoption.eu/blog/2023/01/31/code_c2.html
8 - https://code.visualstudio.com/docs/remote/tunnels
9author: Nasreddine Bencherchali (Nextron Systems)
10date: 2023-10-25
11tags:
12 - attack.command-and-control
13 - attack.t1071.001
14logsource:
15 category: process_creation
16 product: windows
17detection:
18 selection_parent:
19 ParentImage|contains: '\servers\Stable-'
20 ParentImage|endswith: '\server\node.exe'
21 ParentCommandLine|contains: '.vscode-server' # Technically one can host its own local server instead of using the VsCode one. And that would probably change the name (requires further research)
22 # Note: Child processes (ie: shells) can be whatever technically (with some efforts)
23 selection_child_1:
24 Image|endswith:
25 - '\powershell.exe'
26 - '\pwsh.exe'
27 CommandLine|contains: '\terminal\browser\media\shellIntegration.ps1'
28 selection_child_2:
29 Image|endswith:
30 - '\wsl.exe'
31 - '\bash.exe'
32 condition: selection_parent and 1 of selection_child_*
33falsepositives:
34 - Legitimate use of Visual Studio Code tunnel and running code from there
35level: medium
References
Related rules
- Visual Studio Code Tunnel Service Installation
- Bitsadmin to Uncommon IP Server Address
- HTTP Request With Empty User Agent
- HackTool - BabyShark Agent Default URL Pattern
- HackTool - CobaltStrike Malleable Profile Patterns - Proxy