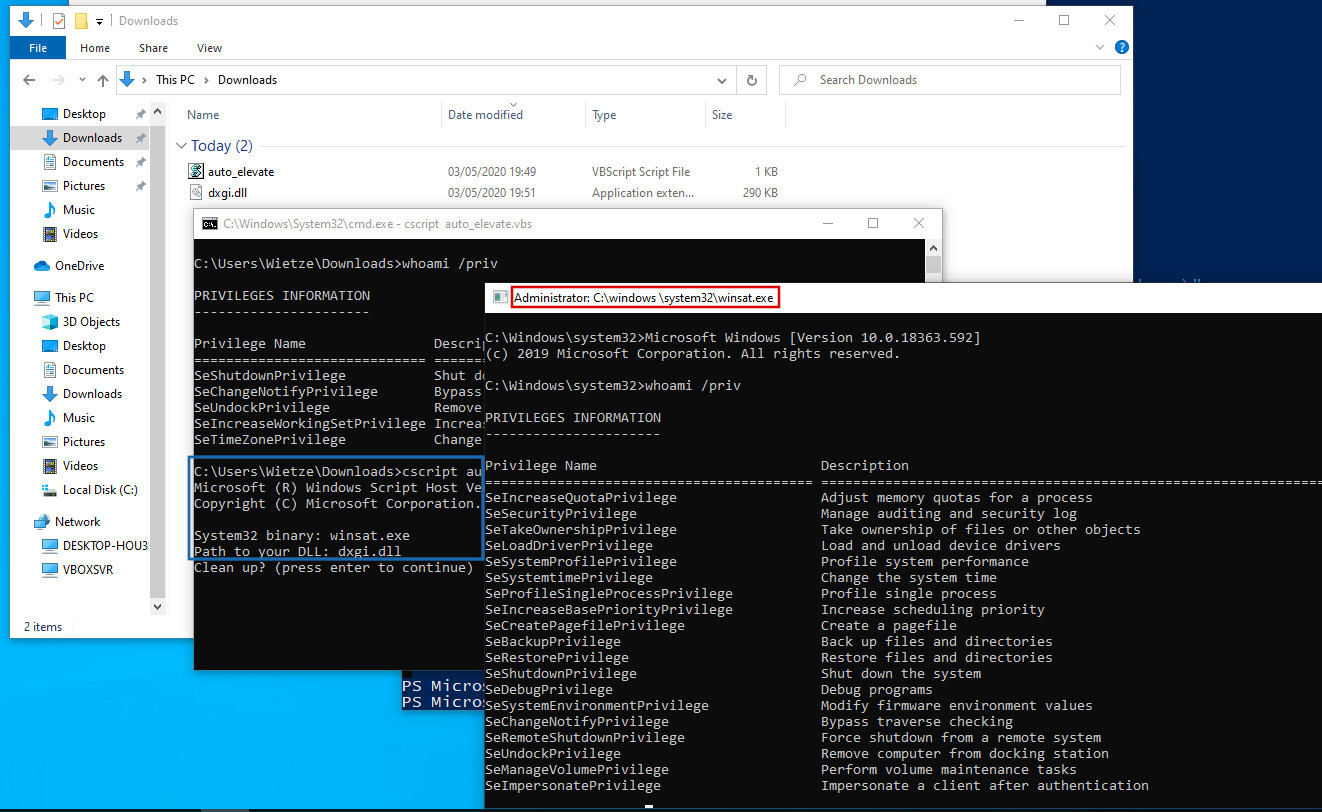
TrustedPath UAC Bypass Pattern
Detects indicators of a UAC bypass method by mocking directories
Sigma rule (View on GitHub)
1title: TrustedPath UAC Bypass Pattern
2id: 4ac47ed3-44c2-4b1f-9d51-bf46e8914126
3status: test
4description: Detects indicators of a UAC bypass method by mocking directories
5references:
6 - https://medium.com/tenable-techblog/uac-bypass-by-mocking-trusted-directories-24a96675f6e
7 - https://www.wietzebeukema.nl/blog/hijacking-dlls-in-windows
8 - https://github.com/netero1010/TrustedPath-UACBypass-BOF
9author: Florian Roth (Nextron Systems)
10date: 2021/08/27
11tags:
12 - attack.defense_evasion
13 - attack.t1548.002
14logsource:
15 category: process_creation
16 product: windows
17detection:
18 selection:
19 Image|contains: 'C:\Windows \System32\'
20 condition: selection
21falsepositives:
22 - Unknown
23level: critical
References
Related rules
- Potential UAC Bypass Via Sdclt.EXE
- UAC Bypass Tools Using ComputerDefaults
- Shell Open Registry Keys Manipulation
- UAC Bypass Abusing Winsat Path Parsing - File
- UAC Bypass Abusing Winsat Path Parsing - Process