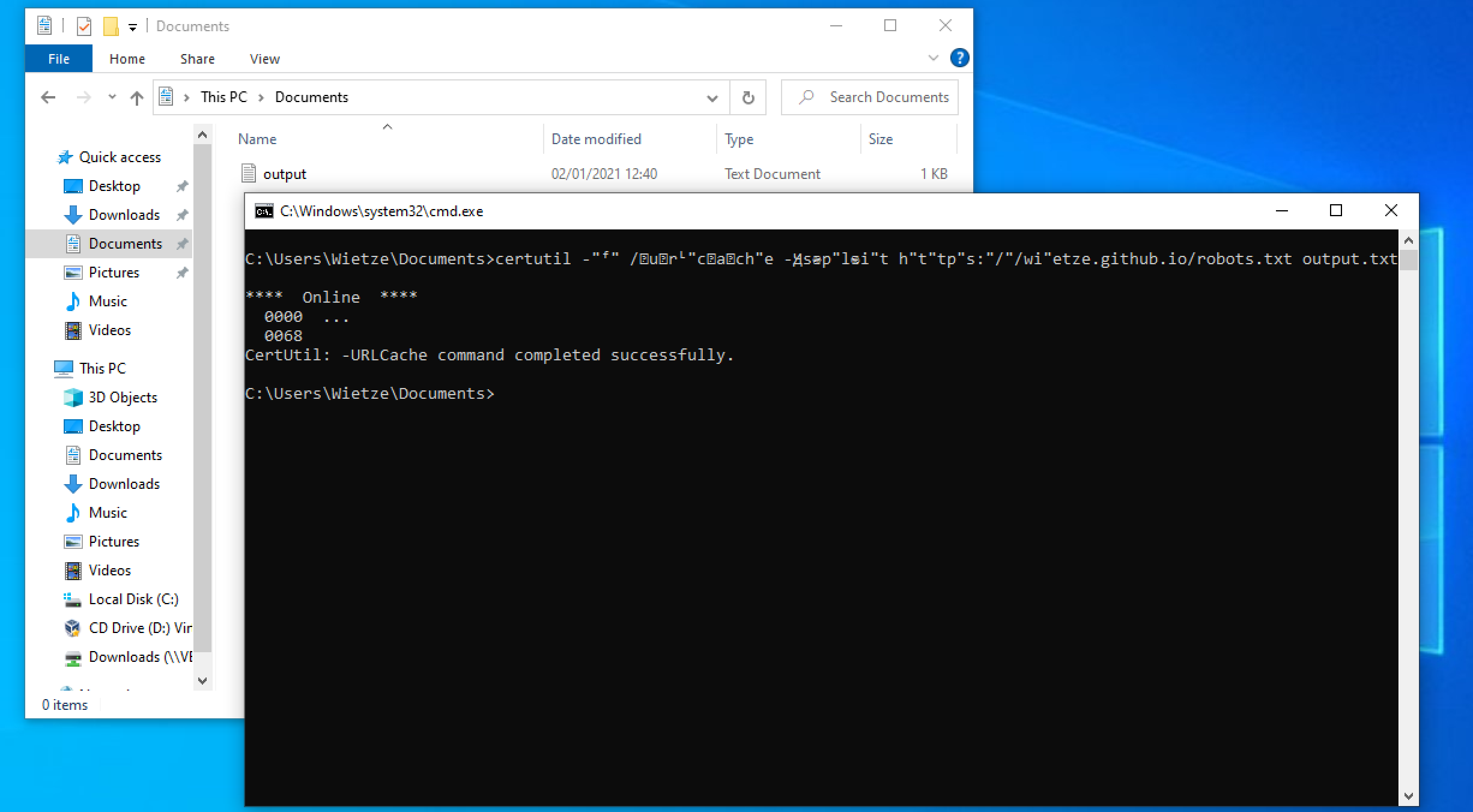
Potential CommandLine Obfuscation Using Unicode Characters From Suspicious Image
Detects potential commandline obfuscation using unicode characters. Adversaries may attempt to make an executable or file difficult to discover or analyze by encrypting, encoding, or otherwise obfuscating its contents on the system or in transit.
Sigma rule (View on GitHub)
1title: Potential CommandLine Obfuscation Using Unicode Characters From Suspicious Image
2id: 584bca0f-3608-4402-80fd-4075ff6072e3
3related:
4 - id: e0552b19-5a83-4222-b141-b36184bb8d79
5 type: similar
6 - id: ad691d92-15f2-4181-9aa4-723c74f9ddc3 # RTLO
7 type: similar
8 - id: 2c0d2d7b-30d6-4d14-9751-7b9113042ab9
9 type: obsolete
10status: test
11description: |
12 Detects potential commandline obfuscation using unicode characters.
13 Adversaries may attempt to make an executable or file difficult to discover or analyze by encrypting, encoding, or otherwise obfuscating its contents on the system or in transit.
14references:
15 - https://www.wietzebeukema.nl/blog/windows-command-line-obfuscation
16 - https://github.com/redcanaryco/atomic-red-team/blob/f339e7da7d05f6057fdfcdd3742bfcf365fee2a9/atomics/T1027/T1027.md#atomic-test-6---dlp-evasion-via-sensitive-data-in-vba-macro-over-http
17author: frack113, Florian Roth (Nextron Systems), Josh Nickels
18date: 2024-09-02
19modified: 2025-05-30
20tags:
21 - attack.defense-evasion
22 - attack.t1027
23logsource:
24 category: process_creation
25 product: windows
26detection:
27 selection_img:
28 Image|endswith:
29 - '\cmd.exe'
30 - '\cscript.exe'
31 - '\powershell.exe'
32 - '\powershell_ise.exe'
33 - '\pwsh.exe'
34 - '\wscript.exe'
35 OriginalFileName:
36 - 'Cmd.EXE'
37 - 'cscript.exe'
38 - 'PowerShell.EXE'
39 - 'PowerShell_ISE.EXE'
40 - 'pwsh.dll'
41 - 'wscript.exe'
42 selection_special_chars:
43 CommandLine|contains:
44 # spacing modifier letters that get auto-replaced
45 - 'ˣ' # 0x02E3
46 - '˪' # 0x02EA
47 - 'ˢ' # 0x02E2
48 # Forward slash alternatives
49 - '∕' # 0x22FF
50 - '⁄' # 0x206F
51 # Hyphen alternatives
52 - '―' # 0x2015
53 - '—' # 0x2014
54 # Whitespace that don't work as path separator
55 - ' ' # 0x00A0
56 # Other
57 - '¯'
58 - '®'
59 - '¶'
60 # Unicode whitespace characters
61 - '⠀' # Braille Pattern Blank (Unicode: U+2800)
62 condition: all of selection_*
63falsepositives:
64 - Unknown
65level: high
References
Related rules
- Potential PowerShell Obfuscation Via WCHAR/CHAR
- Base64 Encoded PowerShell Command Detected
- Renamed AutoIt Execution
- ConvertTo-SecureString Cmdlet Usage Via CommandLine
- Decode Base64 Encoded Text