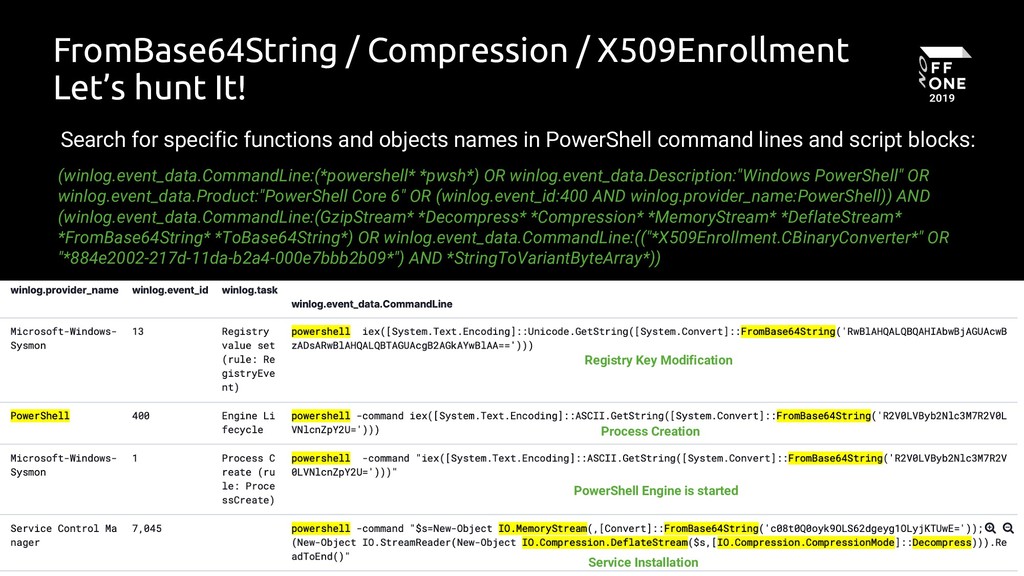
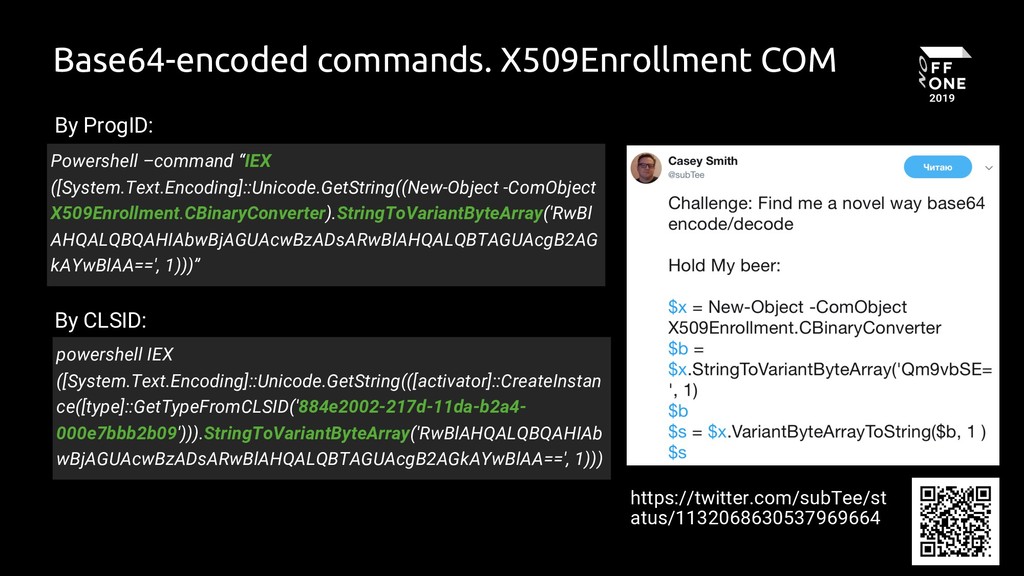
Suspicious X509Enrollment - Process Creation
Detect use of X509Enrollment
Sigma rule (View on GitHub)
1title: Suspicious X509Enrollment - Process Creation
2id: 114de787-4eb2-48cc-abdb-c0b449f93ea4
3related:
4 - id: 504d63cb-0dba-4d02-8531-e72981aace2c
5 type: similar
6status: test
7description: Detect use of X509Enrollment
8references:
9 - https://speakerdeck.com/heirhabarov/hunting-for-powershell-abuse?slide=42
10 - https://speakerdeck.com/heirhabarov/hunting-for-powershell-abuse?slide=41
11 - https://learn.microsoft.com/en-us/dotnet/api/microsoft.hpc.scheduler.store.cx509enrollmentwebclassfactoryclass?view=hpc-sdk-5.1.6115
12author: frack113
13date: 2022-12-23
14tags:
15 - attack.defense-evasion
16 - attack.t1553.004
17logsource:
18 product: windows
19 category: process_creation
20detection:
21 selection:
22 CommandLine|contains:
23 - 'X509Enrollment.CBinaryConverter'
24 - '884e2002-217d-11da-b2a4-000e7bbb2b09'
25 condition: selection
26falsepositives:
27 - Legitimate administrative script
28level: medium
References
Related rules
- Cisco Crypto Commands
- Install Root Certificate
- New Root Certificate Installed Via CertMgr.EXE
- Root Certificate Installed - PowerShell
- Root Certificate Installed From Susp Locations