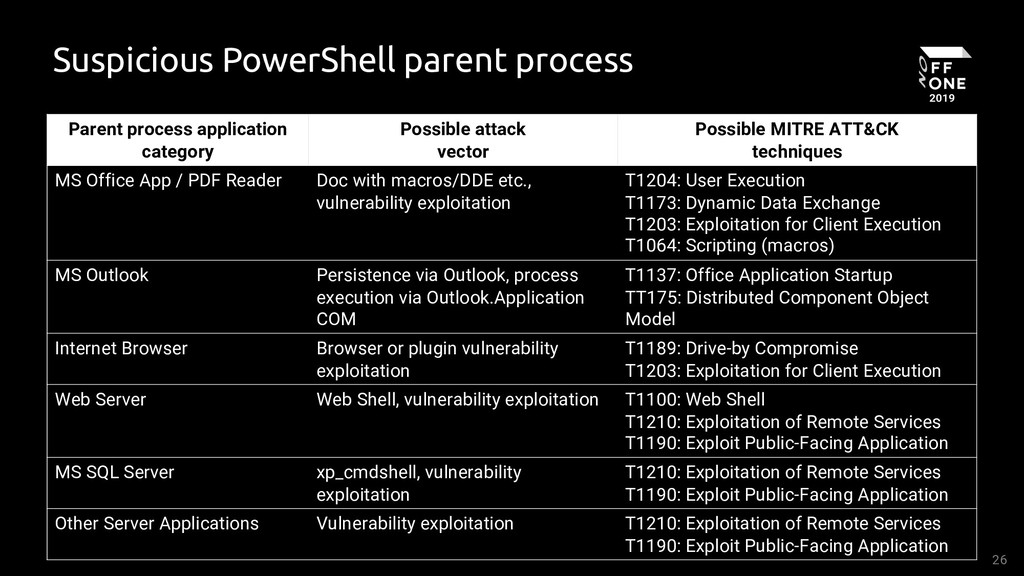
Suspicious PowerShell Parent Process
Detects a suspicious or uncommon parent processes of PowerShell
Sigma rule (View on GitHub)
1title: Suspicious PowerShell Parent Process
2id: 754ed792-634f-40ae-b3bc-e0448d33f695
3related:
4 - id: 692f0bec-83ba-4d04-af7e-e884a96059b6
5 type: derived
6status: test
7description: Detects a suspicious or uncommon parent processes of PowerShell
8references:
9 - https://speakerdeck.com/heirhabarov/hunting-for-powershell-abuse?slide=26
10author: Teymur Kheirkhabarov, Harish Segar
11date: 2020/03/20
12modified: 2023/02/04
13tags:
14 - attack.execution
15 - attack.t1059.001
16logsource:
17 category: process_creation
18 product: windows
19detection:
20 selection_parent:
21 - ParentImage|contains: 'tomcat'
22 - ParentImage|endswith:
23 - '\amigo.exe'
24 - '\browser.exe'
25 - '\chrome.exe'
26 - '\firefox.exe'
27 - '\httpd.exe'
28 - '\iexplore.exe'
29 - '\jbosssvc.exe'
30 - '\microsoftedge.exe'
31 - '\microsoftedgecp.exe'
32 - '\MicrosoftEdgeSH.exe'
33 - '\mshta.exe'
34 - '\nginx.exe'
35 - '\outlook.exe'
36 - '\php-cgi.exe'
37 - '\regsvr32.exe'
38 - '\rundll32.exe'
39 - '\safari.exe'
40 - '\services.exe'
41 - '\sqlagent.exe'
42 - '\sqlserver.exe'
43 - '\sqlservr.exe'
44 - '\vivaldi.exe'
45 - '\w3wp.exe'
46 selection_powershell:
47 - Image|endswith:
48 - '\powershell.exe'
49 - '\pwsh.exe'
50 - CommandLine|contains:
51 - '/c powershell' # FPs with sub processes that contained "powershell" somewhere in the command line
52 - '/c pwsh'
53 - Description: 'Windows PowerShell'
54 - Product: 'PowerShell Core 6'
55 - OriginalFileName:
56 - 'PowerShell.EXE'
57 - 'pwsh.dll'
58 condition: all of selection_*
59falsepositives:
60 - Other scripts
61level: high
References
Related rules
- Bad Opsec Powershell Code Artifacts
- ConvertTo-SecureString Cmdlet Usage Via CommandLine
- HackTool - Bloodhound/Sharphound Execution
- HackTool - CrackMapExec PowerShell Obfuscation
- Invoke-Obfuscation CLIP+ Launcher - Security