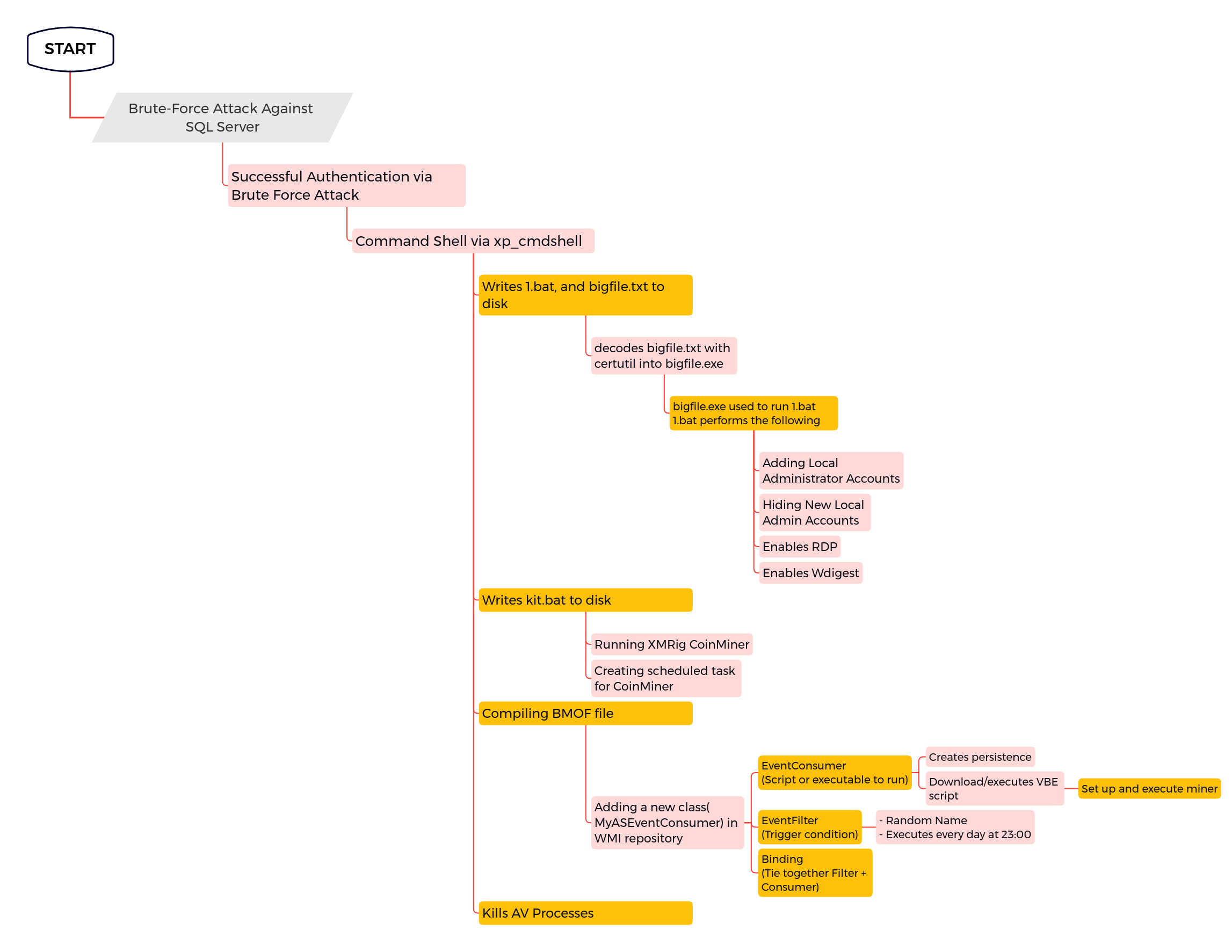
Potential Suspicious Mofcomp Execution
Detects execution of the "mofcomp" utility as a child of a suspicious shell or script running utility or by having a suspicious path in the commandline. The "mofcomp" utility parses a file containing MOF statements and adds the classes and class instances defined in the file to the WMI repository. Attackers abuse this utility to install malicious MOF scripts
Sigma rule (View on GitHub)
1title: Potential Suspicious Mofcomp Execution
2id: 1dd05363-104e-4b4a-b963-196a534b03a1
3status: test
4description: |
5 Detects execution of the "mofcomp" utility as a child of a suspicious shell or script running utility or by having a suspicious path in the commandline.
6 The "mofcomp" utility parses a file containing MOF statements and adds the classes and class instances defined in the file to the WMI repository.
7 Attackers abuse this utility to install malicious MOF scripts
8references:
9 - https://thedfirreport.com/2022/07/11/select-xmrig-from-sqlserver/
10 - https://github.com/The-DFIR-Report/Sigma-Rules/blob/75260568a7ffe61b2458ca05f6f25914efb44337/win_mofcomp_execution.yml
11 - https://learn.microsoft.com/en-us/windows/win32/wmisdk/mofcomp
12author: Nasreddine Bencherchali (Nextron Systems)
13date: 2022-07-12
14modified: 2023-04-11
15tags:
16 - attack.defense-evasion
17 - attack.t1218
18logsource:
19 category: process_creation
20 product: windows
21detection:
22 selection_img:
23 - Image|endswith: '\mofcomp.exe'
24 - OriginalFileName: 'mofcomp.exe'
25 selection_case:
26 - ParentImage|endswith:
27 - '\cmd.exe'
28 - '\powershell.exe'
29 - '\pwsh.exe'
30 - '\wsl.exe'
31 - '\wscript.exe'
32 - '\cscript.exe'
33 - CommandLine|contains:
34 - '\AppData\Local\Temp'
35 - '\Users\Public\'
36 - '\WINDOWS\Temp\'
37 - '%temp%'
38 - '%tmp%'
39 - '%appdata%'
40 filter_main_wmiprvse:
41 ParentImage: 'C:\Windows\System32\wbem\WmiPrvSE.exe'
42 CommandLine|contains: 'C:\Windows\TEMP\'
43 CommandLine|endswith: '.mof'
44 filter_optional_null_parent:
45 # Sometimes the parent information isn't available from the Microsoft-Windows-Security-Auditing provider.
46 CommandLine|contains: 'C:\Windows\TEMP\'
47 CommandLine|endswith: '.mof'
48 condition: all of selection_* and not 1 of filter_main_* and not 1 of filter_optional_*
49falsepositives:
50 - Unknown
51level: high
References
Related rules
- Abusing Print Executable
- AgentExecutor PowerShell Execution
- Arbitrary File Download Via MSOHTMED.EXE
- Arbitrary File Download Via MSPUB.EXE
- Arbitrary File Download Via PresentationHost.EXE