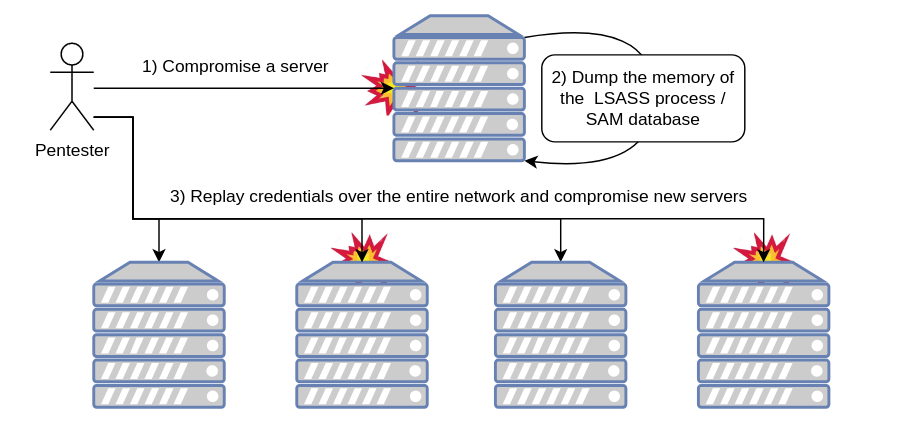
HackTool - Impersonate Execution
Detects execution of the Impersonate tool. Which can be used to manipulate tokens on a Windows computers remotely (PsExec/WmiExec) or interactively
Sigma rule (View on GitHub)
1title: HackTool - Impersonate Execution
2id: cf0c254b-22f1-4b2b-8221-e137b3c0af94
3status: test
4description: Detects execution of the Impersonate tool. Which can be used to manipulate tokens on a Windows computers remotely (PsExec/WmiExec) or interactively
5references:
6 - https://sensepost.com/blog/2022/abusing-windows-tokens-to-compromise-active-directory-without-touching-lsass/
7 - https://github.com/sensepost/impersonate
8author: Sai Prashanth Pulisetti @pulisettis
9date: 2022-12-21
10modified: 2023-02-08
11tags:
12 - attack.privilege-escalation
13 - attack.defense-evasion
14 - attack.t1134.001
15 - attack.t1134.003
16logsource:
17 product: windows
18 category: process_creation
19detection:
20 selection_commandline_exe:
21 CommandLine|contains: 'impersonate.exe'
22 selection_commandline_opt:
23 CommandLine|contains:
24 - ' list '
25 - ' exec '
26 - ' adduser '
27 selection_hash_plain:
28 Hashes|contains:
29 - 'MD5=9520714AB576B0ED01D1513691377D01'
30 - 'SHA256=E81CC96E2118DC4FBFE5BAD1604E0AC7681960143E2101E1A024D52264BB0A8A'
31 - 'IMPHASH=0A358FFC1697B7A07D0E817AC740DF62'
32 selection_hash_ext:
33 - md5: '9520714AB576B0ED01D1513691377D01'
34 - sha256: 'E81CC96E2118DC4FBFE5BAD1604E0AC7681960143E2101E1A024D52264BB0A8A'
35 - Imphash: '0A358FFC1697B7A07D0E817AC740DF62'
36 condition: all of selection_commandline_* or 1 of selection_hash_*
37falsepositives:
38 - Unknown
39level: medium
References
Related rules
- HackTool - SharpDPAPI Execution
- HackTool - SharpImpersonation Execution
- Potential Access Token Abuse
- APT PRIVATELOG Image Load Pattern
- Abuse of Service Permissions to Hide Services Via Set-Service