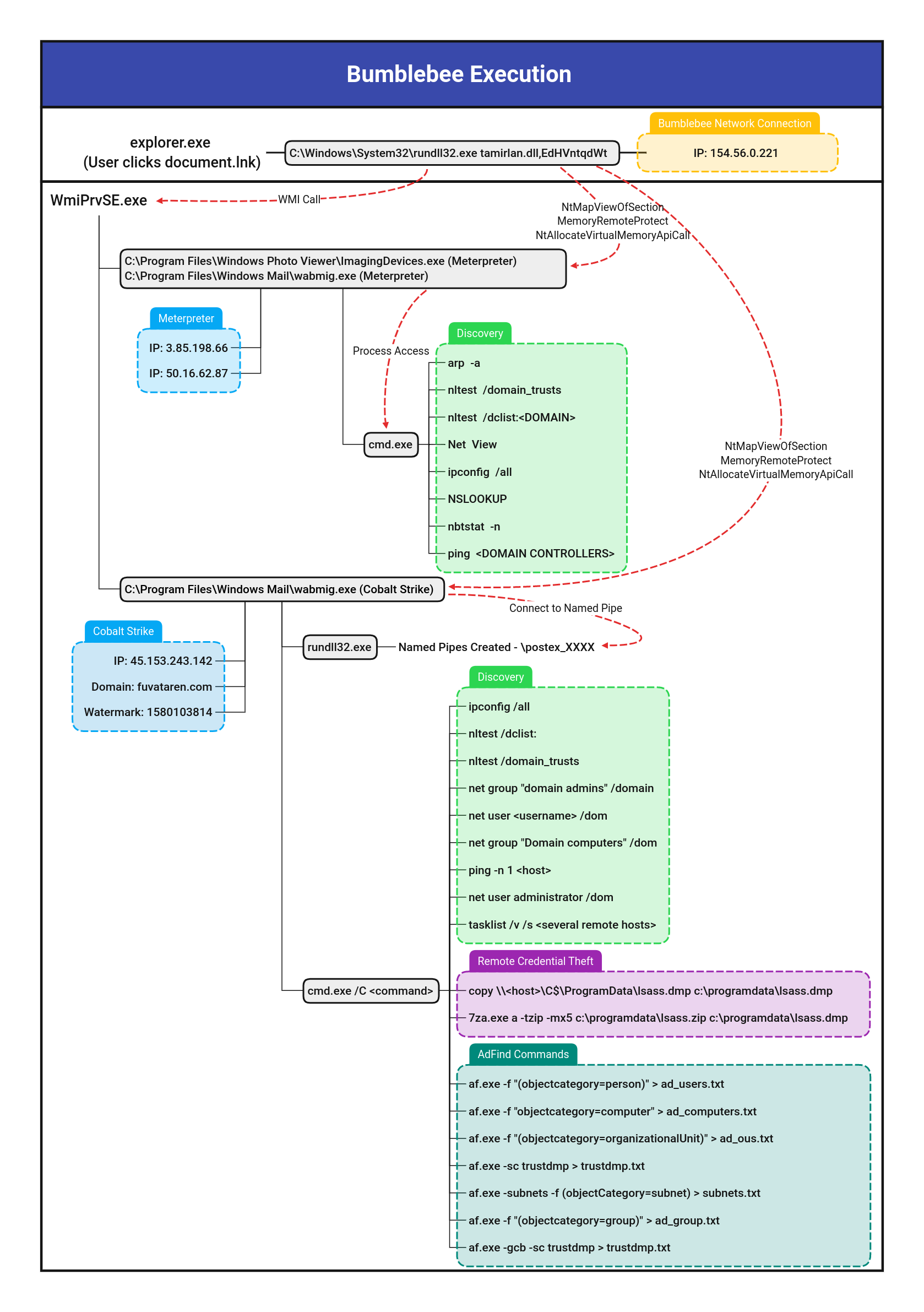
7Zip Compressing Dump Files
Detects execution of 7z in order to compress a file with a ".dmp"/".dump" extension, which could be a step in a process of dump file exfiltration.
Sigma rule (View on GitHub)
1title: 7Zip Compressing Dump Files
2id: ec570e53-4c76-45a9-804d-dc3f355ff7a7
3related:
4 - id: 1ac14d38-3dfc-4635-92c7-e3fd1c5f5bfc
5 type: derived
6status: test
7description: Detects execution of 7z in order to compress a file with a ".dmp"/".dump" extension, which could be a step in a process of dump file exfiltration.
8references:
9 - https://thedfirreport.com/2022/09/26/bumblebee-round-two/
10author: Nasreddine Bencherchali (Nextron Systems)
11date: 2022-09-27
12modified: 2023-09-12
13tags:
14 - attack.collection
15 - attack.t1560.001
16logsource:
17 category: process_creation
18 product: windows
19detection:
20 selection_img:
21 - Description|contains: '7-Zip'
22 - Image|endswith:
23 - '\7z.exe'
24 - '\7zr.exe'
25 - '\7za.exe'
26 - OriginalFileName:
27 - '7z.exe'
28 - '7za.exe'
29 selection_extension:
30 CommandLine|contains:
31 - '.dmp'
32 - '.dump'
33 - '.hdmp'
34 condition: all of selection_*
35falsepositives:
36 - Legitimate use of 7z with a command line in which ".dmp" or ".dump" appears accidentally
37 - Legitimate use of 7z to compress WER ".dmp" files for troubleshooting
38level: medium
References
Related rules
- Compress Data and Lock With Password for Exfiltration With 7-ZIP
- Compress Data and Lock With Password for Exfiltration With WINZIP
- Files Added To An Archive Using Rar.EXE
- Rar Usage with Password and Compression Level
- Suspicious Manipulation Of Default Accounts Via Net.EXE