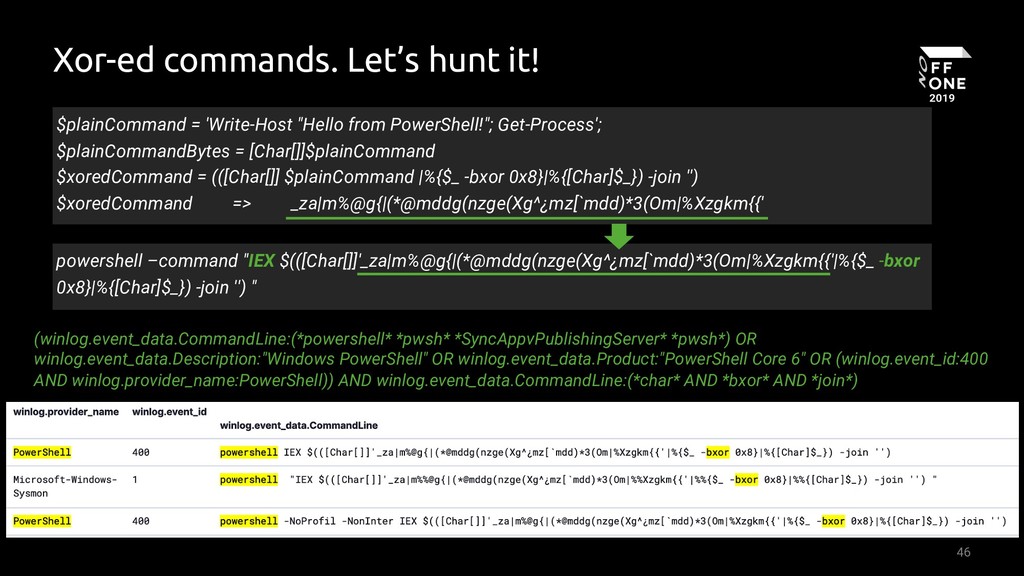
Suspicious XOR Encoded PowerShell Command Line - PowerShell
Detects suspicious powershell process which includes bxor command, alternative obfuscation method to b64 encoded commands.
Sigma rule (View on GitHub)
1title: Suspicious XOR Encoded PowerShell Command Line - PowerShell
2id: 812837bb-b17f-45e9-8bd0-0ec35d2e3bd6
3status: test
4description: Detects suspicious powershell process which includes bxor command, alternative obfuscation method to b64 encoded commands.
5references:
6 - https://speakerdeck.com/heirhabarov/hunting-for-powershell-abuse?slide=46
7author: Teymur Kheirkhabarov, Harish Segar (rule)
8date: 2020/06/29
9modified: 2023/10/27
10tags:
11 - attack.execution
12 - attack.t1059.001
13logsource:
14 product: windows
15 category: ps_classic_start
16detection:
17 selection:
18 Data|contains: 'HostName=ConsoleHost'
19 filter:
20 Data|contains:
21 - 'bxor'
22 - 'char'
23 - 'join'
24 condition: selection and filter
25falsepositives:
26 - Unknown
27level: medium
References
Related rules
- Nslookup PowerShell Download Cradle
- PowerShell Called from an Executable Version Mismatch
- PowerShell Downgrade Attack - PowerShell
- Renamed Powershell Under Powershell Channel
- Suspicious Non PowerShell WSMAN COM Provider