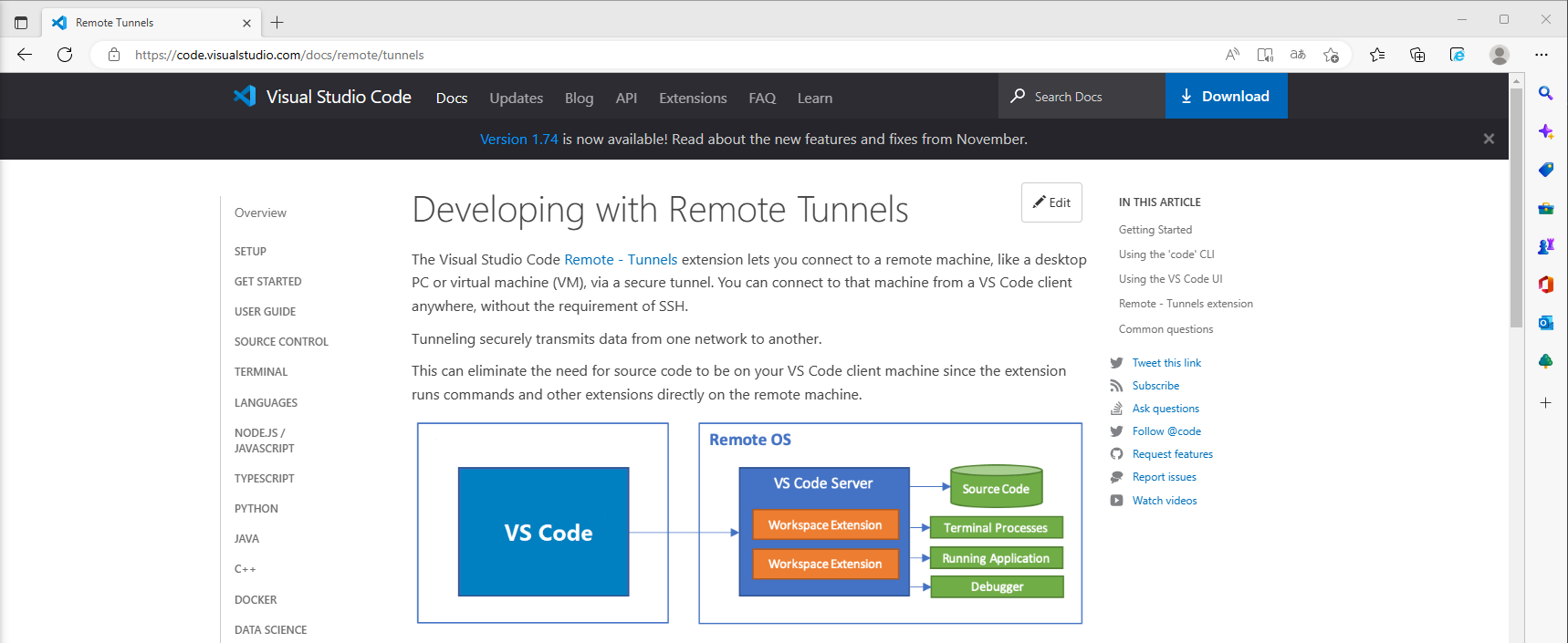
Renamed VsCode Code Tunnel Execution - File Indicator
Detects the creation of a file with the name "code_tunnel.json" which indicate execution and usage of VsCode tunneling utility by an "Image" or "Process" other than VsCode.
Sigma rule (View on GitHub)
1title: Renamed VsCode Code Tunnel Execution - File Indicator
2id: d102b8f5-61dc-4e68-bd83-9a3187c67377
3status: experimental
4description: |
5 Detects the creation of a file with the name "code_tunnel.json" which indicate execution and usage of VsCode tunneling utility by an "Image" or "Process" other than VsCode.
6references:
7 - https://ipfyx.fr/post/visual-studio-code-tunnel/
8 - https://badoption.eu/blog/2023/01/31/code_c2.html
9author: Nasreddine Bencherchali (Nextron Systems)
10date: 2023/10/25
11tags:
12 - attack.command_and_control
13logsource:
14 category: file_event
15 product: windows
16detection:
17 selection:
18 TargetFilename|endswith: '\code_tunnel.json'
19 filter_main_legit_name:
20 # Note: There might be other legitimate names for VsCode. Please add them if found
21 Image|endswith:
22 - '\code-tunnel.exe'
23 - '\code.exe'
24 condition: selection and not 1 of filter_main_*
25falsepositives:
26 - Unknown
27level: high
References
Related rules
- Renamed Visual Studio Code Tunnel Execution
- Visual Studio Code Tunnel Execution
- Visual Studio Code Tunnel Remote File Creation
- Visual Studio Code Tunnel Service Installation
- Visual Studio Code Tunnel Shell Execution