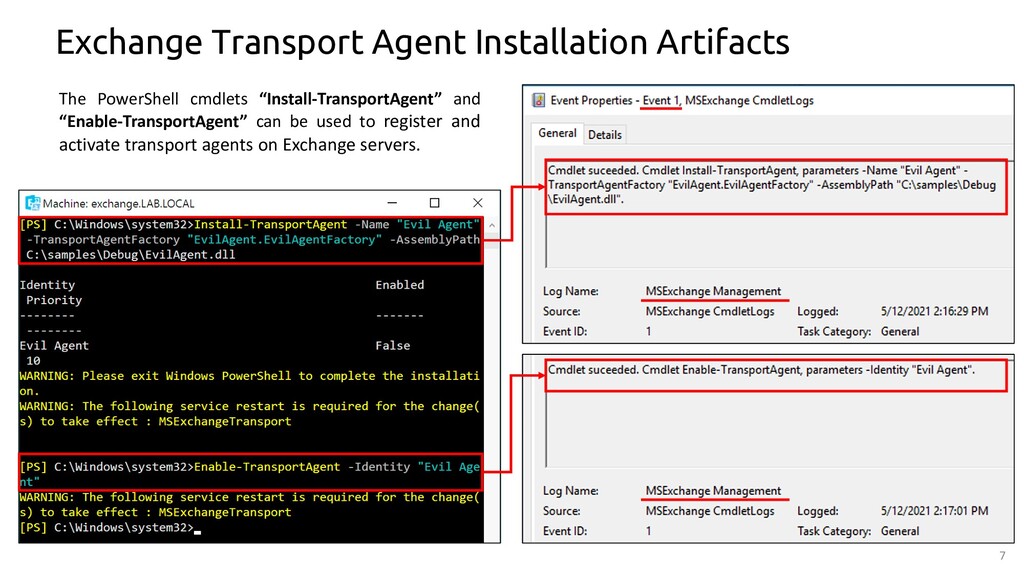
MSExchange Transport Agent Installation - Builtin
Detects the Installation of a Exchange Transport Agent
Sigma rule (View on GitHub)
1title: MSExchange Transport Agent Installation - Builtin
2id: 4fe151c2-ecf9-4fae-95ae-b88ec9c2fca6
3related:
4 - id: 83809e84-4475-4b69-bc3e-4aad8568612f
5 type: derived
6status: test
7description: Detects the Installation of a Exchange Transport Agent
8references:
9 - https://speakerdeck.com/heirhabarov/hunting-for-persistence-via-microsoft-exchange-server-or-outlook?slide=7
10author: Tobias Michalski (Nextron Systems)
11date: 2021-06-08
12modified: 2022-11-27
13tags:
14 - attack.persistence
15 - attack.t1505.002
16logsource:
17 product: windows
18 service: msexchange-management
19detection:
20 selection:
21 - 'Install-TransportAgent'
22 condition: selection
23falsepositives:
24 - Legitimate installations of exchange TransportAgents. AssemblyPath is a good indicator for this.
25level: medium
References
Related rules
- Failed MSExchange Transport Agent Installation
- MSExchange Transport Agent Installation
- AWS IAM Backdoor Users Keys
- Bitsadmin to Uncommon TLD
- CVE-2021-40539 Zoho ManageEngine ADSelfService Plus Exploit